Best Keylogger for iPhone & Android
Support all iOS & Android devices
What is SpyX Phone Keystroke Logger?
Everyone knows that keystroke loggers have many uses. It has been the tool of choice for parents, employers, spouses, security professionals and network administrators.
Keylogger captures all keystroke activity, records remote user behaviour analysis. SpyX tracking is completely invisible and the monitoring data is only available to you.
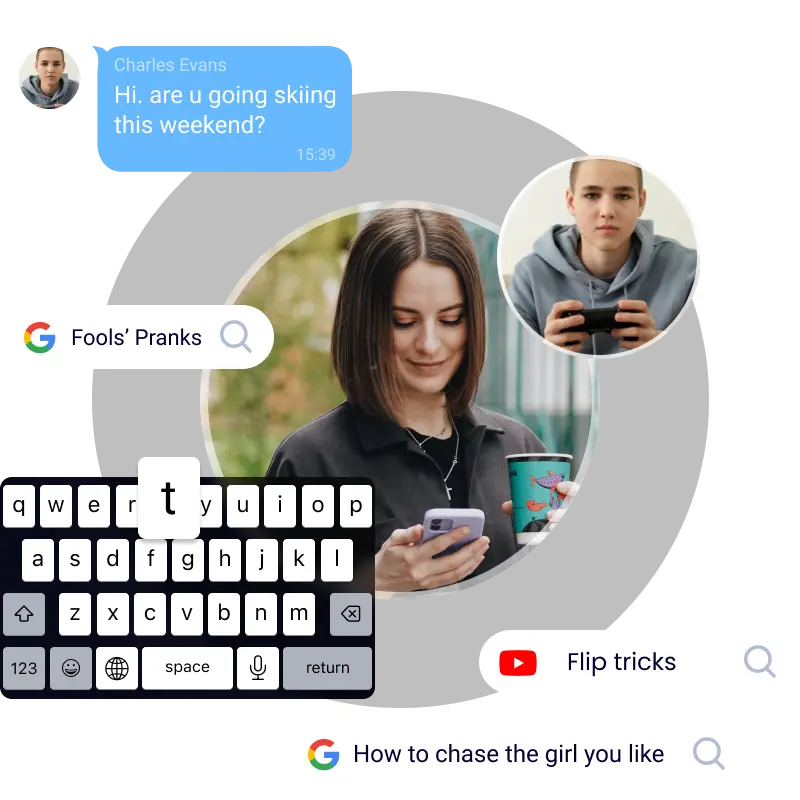
Track what they typed on Android
With the help of SpyX monitoring software, you can monitor what else your child is typing on the device. Such as viewing all the keystrokes in messages, social apps and emails. Find out what they are interested in or talking about.
Check all keylogger details remotely
With SpyX, you can view keystrokes history in real time. You can get the full content of keystrokes and keystroke details. SpyX runs completely covertly and they won't know how you are monitoring them. And SpyX being the top keylogger for android does not require rooting.
Private keystroke monitoring guaranteed
SpyX Mobile Keylogger Software uses advanced encryption technology. Make sure only you know the monitoring data. No data is distributed to third parties or stored on your own servers. That's why SpyX is becoming more and more popular with parents and companies.
How to use SpyX Android Keylogger?
It is very simple to use a phone keylogger. You just finish the setup with the following steps:
Step 1. Create an account
Visit the official website and click on "Try now". Register an account for keylogger by entering your valid email address.
Step 2. Connect target Android phone
Purchase a suitable plan. Then connect the target android phone to the SpyX keylogger. All you need is to enter the iCloud login details associated with the target device.
Step 3. Use keylogger online
To start monitoring the keystrokes of target device, just go to your control panel and click on “Keylogger”, and you can see all data and details typed on specific apps.
Why Do You Need a Phone Keylogger App?
Kelogger can record everything the target types. You can know what they are searching for or what they are talking about.
With the help of SpyX keylogger app, you can monitor every activities on your child's mobile phone. Detect potential threats in advance by monitoring keystrokes history. Keep your children safe from strangers, terrorist threats and other dangers.
It can also help company managers to know how their employees are working online. Know if your employees are wasting time by remotely viewing their keystrokes logs.
Track the keystrokes of your loved ones and check if they are hiding something from you. You can also see the tracked person's location in real time.
FAQ about Keylogger
Q1
How Does Keylogger App Work?
With SpyX keylogger, you can check all of the keywords used so far without letting them know anything about it. The logger keeps a log of the entire keystroke history and also provides alerts for some designated keywords.
Q2
Why Do You Need A Keylogger App?
With keylogger app, parents can know what their children typed on the phone and protect them from potential risk factors. For company, the employers can check whether employees are talking about sensitive information during office hours. In a word, keylogger can prevent communication with potentially threat.
Q3
Do I Need to Root or Jailbreak the Target Device for Keylogger?
No. SpyX keylogger doesn't need to root or jailbreak the target device. SpyX is user-friendly with simple three steps to start keylog the typed content on the target phone.
Q4
What Are Benefits of SpyX Keylogger?
With SpyX keylogger, you can get to know more about your children and employees. Monitor the keystrokes on your children's device, you will know what they are search/talking about. And you can help them when it is necessary.
Q5
Can I Track My children's Keystrokes without Them Knowing?
With SpyX keylogger, you can get to know more about your children and employees. Monitor the keystrokes on your children's device, you will know what they are search/talking about. And you can help them when it is necessary.