How to hack Facebook Messenger without a Password?
Meta's Messenger is a popular and free social media messaging app that allows Facebook users to interact and chat with their friends and family in real time. Though Facebook Messenger, like other Chat applications, aims at reducing communication gaps, it is frequently exploited for numerous hacking purposes. For a variety of reasons, lots of people explore how to hack someone's Messenger without a password.
Spouses get their spouse’s Messenger hacked to discover their ‘extra-marital relationships. Because of the surge in online bullying, fake identities, and pornographic exploitation, the app poses a risk to children and teenagers. Employers are also aware of how instant messaging networks such as Facebook Messenger enable unethical employees to share firm secrets with competitors through messenger chats.
These are some reasons why individuals desire to learn how to hack into Messenger chats. Most people even try to hack Facebook accounts, but it might not help to read the messenger chats. This blog post will cover how to hack someone’s Messenger account.
5 Best Ways to Hack Messenger
Hacking, such as Facebook hacking, Snapchat hacking, Instagram hacking, and Messenger hacking, is one of the most popular and explored topics on the internet. There are various free Facebook Messenger hack methods available on the internet. The method described here is one of the most effective ways to hack Facebook's Messenger messages and other activity.
1. Reset the Password
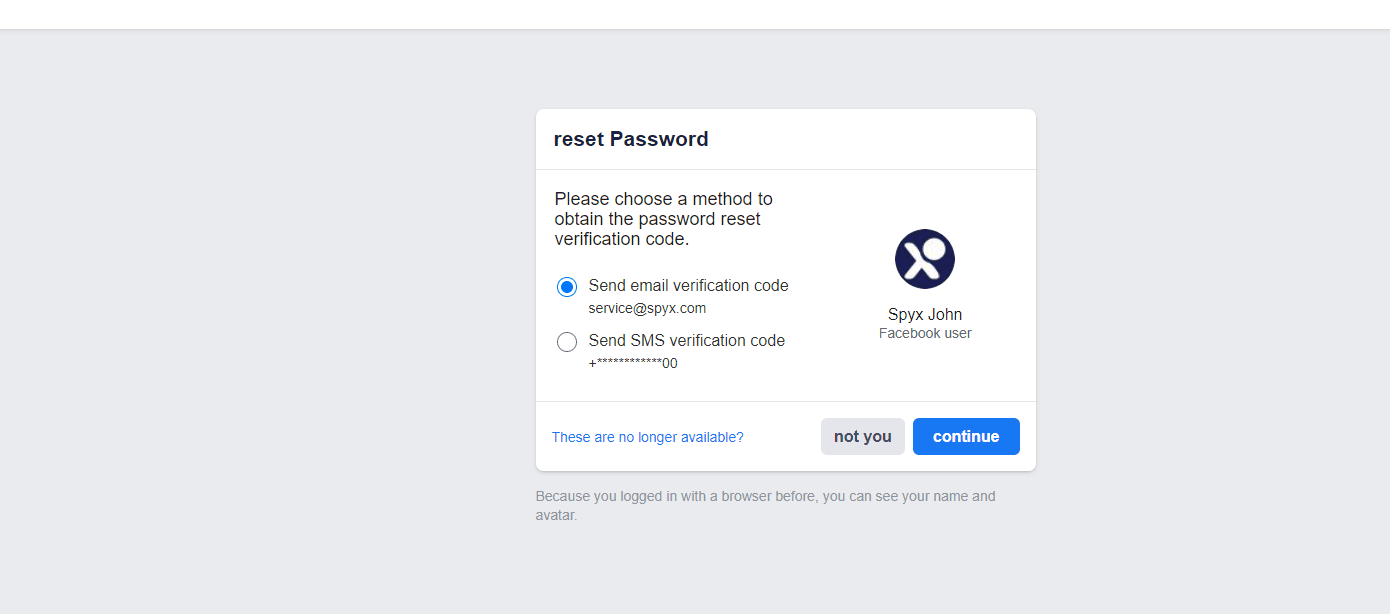
This is one of the simplest methods for hacking or breaking into someone's Facebook Messenger. However, this approach is only simple if you are friends with the person you want to hack.
1. The first step is to get your friend’s Facebook email login. That is, the email address associated with their account on Facebook. If you don't know their email address, look it up in the Contact Info section on their Facebook account. The majority of individuals provide their email addresses on their profile.
2.Next, select “Forgot your password?” and type in their email. Select the option tagged: “This is my account.”
3.Facebook will give you the option of resetting the password via your target’s email. However, this will merely tell them that someone is attempting to access their account, which you do not want. To prevent being detected, choose "No longer have access to these?" instead.
4.Once you have done this, you will see a bar titled: “How can we reach you?” Fill up the blank space with your own email address.However, you must ensure that the email address is not associated with any Facebook account. If you don’t have an email address that isn’t linked to a Facebook account, create a new one.
5.Once you have provided an email address, Facebook will ask you a secret question. If the victim is your kid, lover, or close friend, this part is simple. However, if you don't know anything about them, you may always speculate on the answer. If you correctly answer the secret question, you will be able to reset your password. However, you must wait 24 hours before logging into the account.
6.If you have no idea about the answer to the secret question, click on the option tagged: “Recover your account with help from friends.” Once you do this, Facebook will let you choose between three and five friends. After that, it gives them codes or passwords, which you can ask and enter on the next page. You might select between three and five friends who will be willing to provide you the codes. However, if you don’t trust anyone to send you the codes without snitching, you may decide to create about three fake accounts beforehand and send your victim a friend request. In this manner, you may pick fake accounts and ask Facebook to provide the codes to them.
2. Keyloggers

A keylogger is a software tool used to record keystrokes on a computer or mobile device. In turn, this records everything you enter on the keyboard and saves it for later use. Typically, keyloggers are installed as software applications in the operating system to track keystrokes, but there are also hardware keyloggers.
A hardware keylogger, also known as a physical keylogger, connects to a computer via a USB port and records everything from the keyboard before sending it to the computer. There are various mobile keyloggers that do the same thing on various operating systems.
How does keylogging work?
All keyloggers operate in the background and cannot be observed by the user unless the keylogger password and a shortcut to access it are known. It will log all keys pushed and provide you with a complete report of when and which key was used for what application - in other words, a clear report to find the password.
Anyone who reads the keylogger records will be able to view Facebook passwords, as well as any other passwords and sensitive information inputted, such as credit cards, bank usernames, passwords, and so on. When you use a public computer, you run the danger of exposing your Facebook password to others.
Many people are using mobile keyloggers these days. It can track the phone's keypad. So, any sensitive information input on a mobile keyboard can be hacked.
3: Weak Passwords

You might be surprised to know that most people use very weak passwords. The most frequent passwords are simple:
Password
123456
123456789
111111
123123
Qwerty
Qwerty123
12345
DEFAULT
654321
When you input basic, regularly used passwords like "qwerty" or "password," you have a big chance of gaining access to someone's account. Furthermore, many people utilize their personal information as passwords. It's easier to hack into someone's Facebook if you know basic information like their first and last name and date of birth.
If the individual isn't particularly smart, you'll have to utilize a robot to test alternative password combinations. These bots can process thousands of password combinations in just a few of seconds.
However, you should remember that a good password combines lower/uppercase letters, numbers and special characters. It should not have any personal information. For example, if a password has only lowercase letters, it automatically becomes easier to crack.
When it comes to hacking someone's Facebook Messenger, this hardly works because after you input the wrong password 5 times, you will be blocked.
4.Use Phishing to Hack Facebook Messenger

Another method for getting the information you need is to use a search engine. To get data, it doesn't employ any hacking techniques; instead, it relies on and works entirely on human psychology. For example, social engineers have been known to use weaknesses in human behavior to solve scams.
To do so, you simply use emails that appear like they came from Facebook and contain details on a cyber-attack attempt. Along with this email, the user will be directed to a URL where they will be required to re-enter their login information as well as reset their Facebook password to make their account safer.
These details will be given to the sender of the hoax email. As a consequence, you'll be able to acquire the information you need even if you don't have physical access to the system.
5. Use SpyX Spy Tool

SpyX is the easiest and most effective way to hack a Facebook account. It is a spyware that can be compatible with both Android&iOS. SpyX allows you to see what your kids, spouse are doing on Facebook. You'll be able to read their messages, view their downloaded pictures, and more! SpyX doesn't need to be installed on the target phone, so they won't even know you're spying on his Facebook.
SpyX can easily monitor someone's conversations on various platforms like WhatsApp, Snapchat, Instagram, Facebook Messenger and Tinder, using this feature you can even view deleted messages as it collects all social media conversations and displays them in one convenient place. SpyX can also check the real-time location of the target phone in real time, letting you know where he is.
Final Thoughts
Nowadays, it is quite possible to acquire access to anyone's Facebook Messenger. Unsure about how to access another person's Facebook messages without their knowledge or suspicion? With an impressive spy app like SpyX, you can have access to all the information you would ever need.
More Articles Like This
SPYX'S SOFTWARE INTENDED FOR LEGAL USE ONLY. You are required to notify users of the device that they are being monitored. Failure to do so is likely to result in violation of applicable law and may result in severe monetary and criminal penalties ...







Disclaimer: SPYX'S SOFTWARE INTENDED FOR LEGAL USE ONLY. You are required to notify users of the device that they are being monitored. Failure to do so is likely to result .....
Registered Address: South Bank Tower, 55 Upper Ground,, London, England, SE1 9EY
Company Name: UK GBYTE TECHNOLOGY CO., LIMITED
Wisteria Trade Limited
