A full guide on How to Detect and Remove Spyware for Android & iPhone

Last updated:mars 25, 2025
Table of content
With the emergence of technology, spyware developers have found the latest way to infect and track user activities for their purpose. Therefore, phone users are looking for cell phone spyware detection and removal to keep their information and activities secure from spyware.
If you are a mobile phone user or service provider, this article will help you to know how to detect and remove spyware from Android & iPhone.
Part 1. Introduction of phone spyware
1.1. What is phone spyware
Cell Phone Spyware is a software application or program developed to monitor and track the actions on mobile devices without the user's consent. Smartphones and tablets are the victims of phone spyware allowing third parties to remotely monitor the activities, usage, calls, and messages. Nowadays people are also concerned about their phones having spyware.
1.2. How does phone spyware work
Phone spyware operates through the secret installation of the applications on targeted devices like cell phones or tablets. After the successful installation, spyware works in the background without user knowledge and tracks the user’s activities.
Following are ways how spyware works:
- Installation
In some cases, physical access is required for installation, while remote installation can be processed through phishing and malicious links.
- Stealth mode
After the successful installation, spyware runs discreetly without user knowledge. It does not appear in the device menu, antivirus software, or task manager to prevent detection.
- Data collection
Cell Phone Spyware collects data of various types from the device based on its capacity and instructions. Data may include calls, text messages, emails, browsing history, media file location, etc.
- Monitoring and control
The installer can monitor the real-time activities such as: listening to phone calls, viewing screen recording and sending commands to perform actions.
- Data transmission
The spyware operator transmits the data to a remote server from the devices with the help of Wi-Fi and cellular connections
1.3. Features of phone spyware
With the development of spyware technology, the monitoring features of current mobile spyware are very powerful, just like the most popular spyware on the market right now, such as SpyX, Msafely, mSpy, etc. They can monitor almost all the data on someone else's phone without being detected.
Here are some common functions of spyware:
Spyware can take down the details of calls such as contact number, duration of the call, and time stamps. The latest spyware has the capacity to intercept ongoing calls and listen to them.
Spyware can capture the text and multi-media messages of the targeted device. It may monitor the exchange of messages on WhatsApp, Facebook, Snapchat, etc.
Spyware can track the most popular social media platforms on the market, such as WhatsApp, Snapchat, Facebook, Telegram, Instagram, TikTok, etc. It can monitor the contacts, chat messages, posts, shared photos and videos, likes, followers, etc., on the target device's social media accounts.
Spyware tracks the location using GPS technology to extract location history and track movements.
Spyware comes up with the capability to track the user's website browsing details including search queries, URLs, and browsing activities on browsers like Chrome, edge, Firefox, etc.
Spyware captures copies of received and sent emails including subjects, content, attachments, and addresses.
Spyware monitors the user application usage pattern and catches data like usage duration, frequency, and interaction.
1.4. Steps of using phone spyware
Using phone spyware typically involves purchasing and downloading the software onto the target device. Once installed, the spyware can be remotely accessed and controlled by the person who installed it. The spyware operator can view, track and store the user activities and data of the targeted devices.
Part 2. Can someone spy on your Android or iPhone secretly
Yes, someone can spy on your mobile device, either an android or an iPhone, using spyware software applications. Spyware installation does not need physical access in most cases, you will be unaware of its installation. In another case, you may have installed the spyware by yourself using a URL received in your email. As a result of such activities, your phone is being monitored by the spyware operator.
Part 3. 10 common signs of someone spying on your Android or iPhone
"Is my phone being monitored?" Have you ever found yourself in such suspicion? If you are currently doubting whether your phone is being monitored, why not take a look at the top 10 common signs to help you determine if your phone is indeed being monitored!
Unusual battery drain
Your phone's battery is depleting faster than usual, possibly due to additional background processes running.
Unusual Phone Behavior during calls
Anomalies such as echoes, clicking noises, or call disruptions may suggest phone monitoring.
Suspicious Account Activities
Unrecognized logins or unusual activities in your online accounts linked to your phone.
Unknown changes in mobile settings
Settings you didn't alter may have been adjusted, indicating unauthorized access.
Background noise during calls
Unexplained noises during calls could be a sign of surveillance.
Slow performance
Sluggish operation despite no apparent reasons, possibly due to additional monitoring software.
Strange behavior or activity on the device
Unexpected actions like apps opening on their own or random screen flashes.
Unexplained data usage
Significant data consumption without your knowledge, potentially due to monitoring activities.
Suspicious pop-up messages or notifications
Unsolicited or suspicious messages or notifications appearing on your phone.
Overheating
Excessive heat, especially during idle periods, may indicate additional processes running in the background.
Part 4. How to remove spyware from your Android or iPhone
There are different methods to remove spyware from Android and iPhone devices because of the difference in their operating systems
4.1. If you are an Android user
If you are an Android user and subjected to a spyware attack, you should take the following actions:
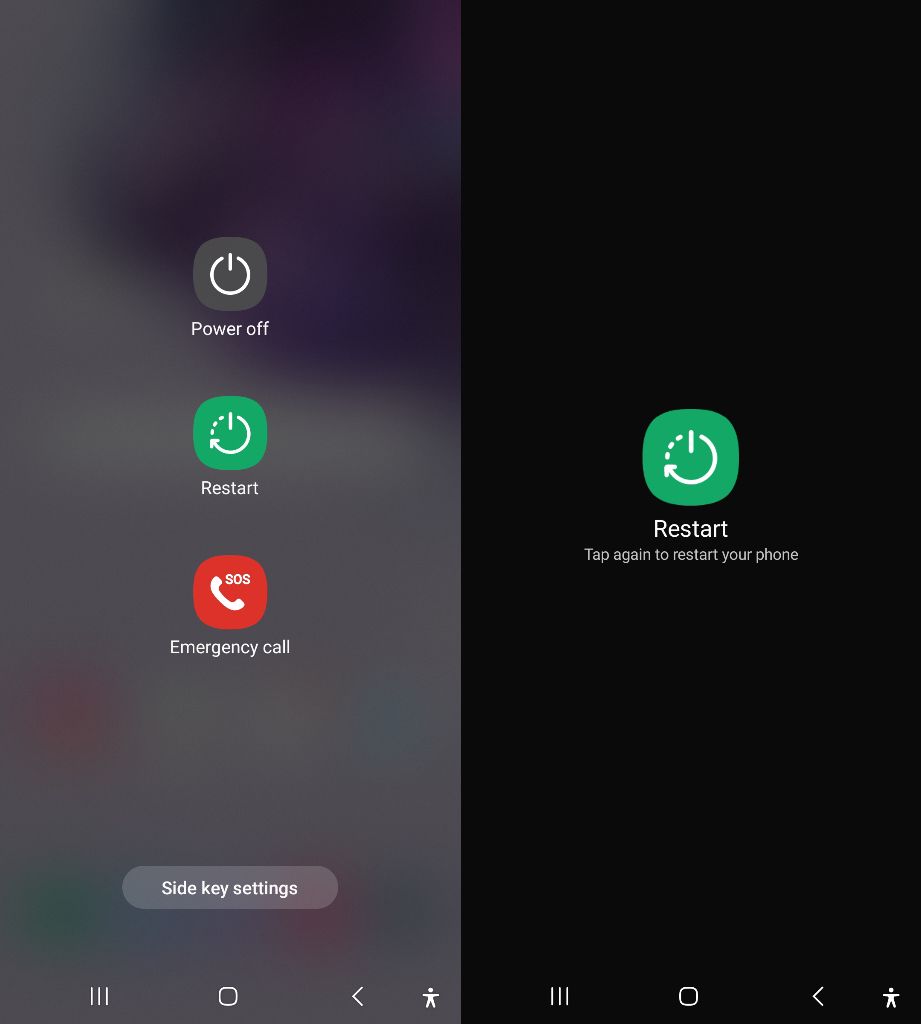
Tip 1. Restart in safe mode
Step 1. Hold down the power button until the power off menu appears.
Step 2. Long-press the "Power off" or "Restart" option until you see a prompt asking if you want to reboot into safe mode.
Step 3. Tap "OK" or "Restart in safe mode.
Once in safe mode, only essential system apps will run, allowing you to identify and uninstall suspicious third-party apps without interference from spyware.
Tip 2. Spot suspicious applications
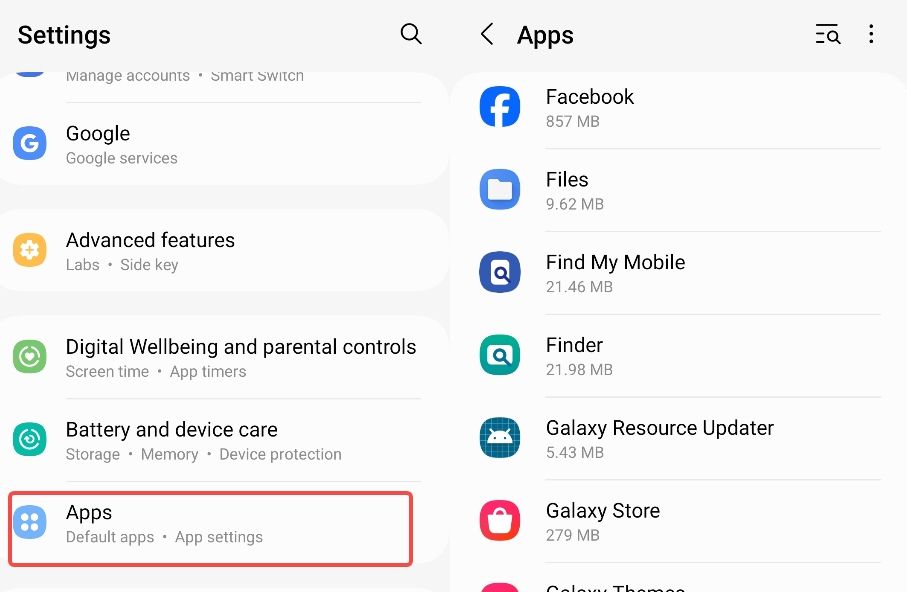
Step 1. Go to "Settings".
Step 2. Find "Apps," "Applications," or "Application Manager", and tap on it.
Step 3. Go through the list of installed apps and find the ones you're not familiar with, haven't installed, or have strange names.
Tip 3. Remove suspicious applications
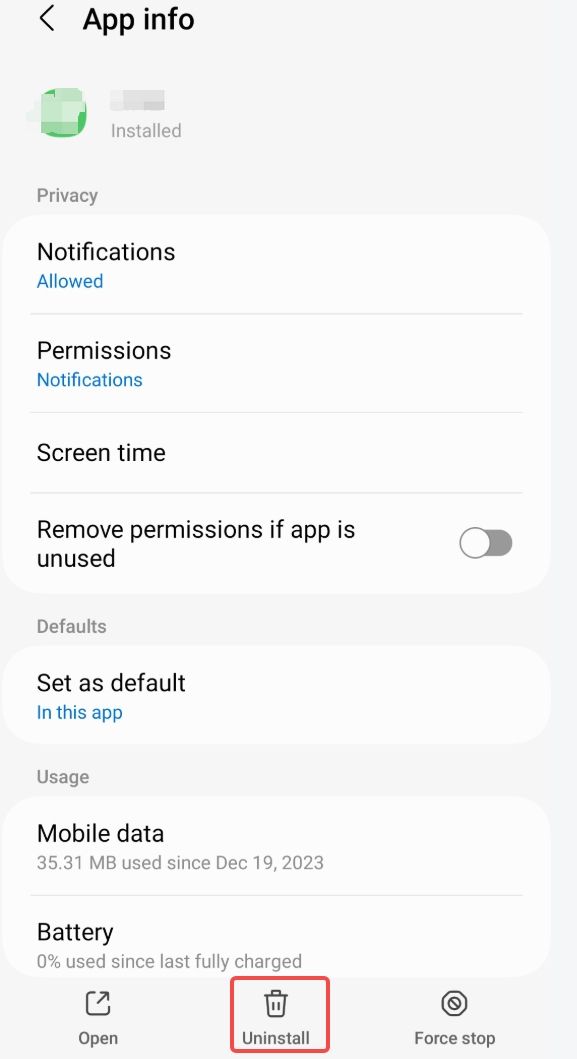
Step 1. Select the suspicious app from the list and tap on it.
Step 2. Click on the "Uninstall" or "Remove" button.
Step 3. Follow the on-screen instructions to uninstall the app.
Tip 4. Clear mobile cache
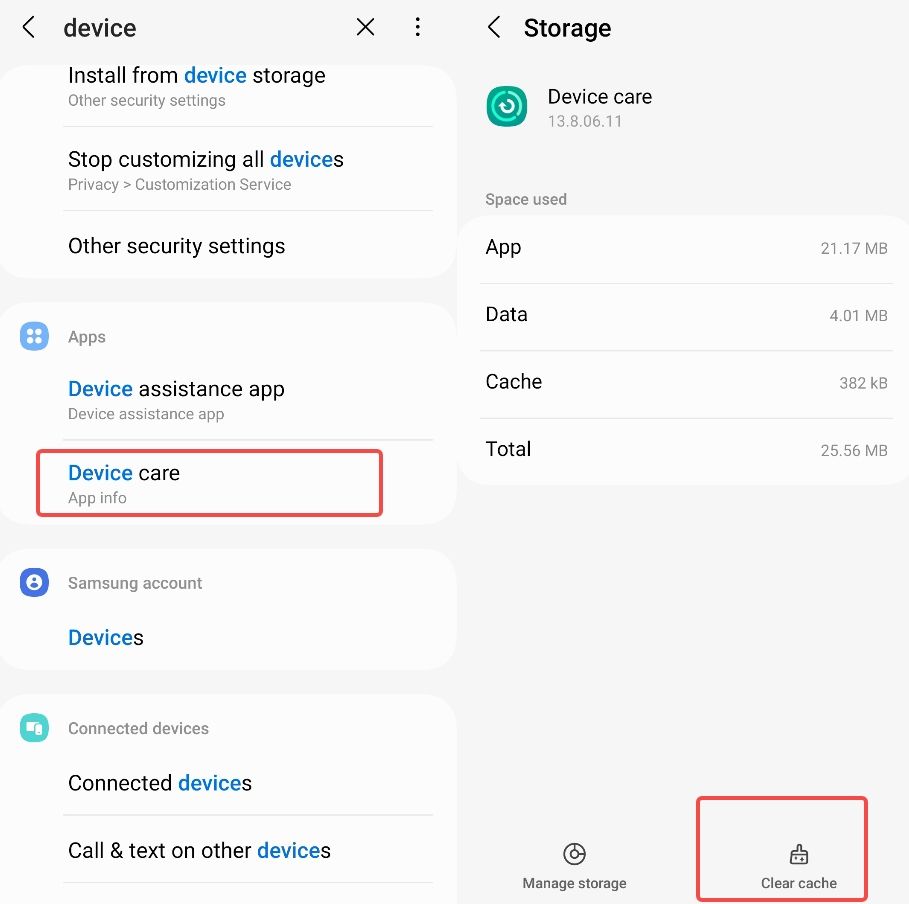
Step 1. Go to "Settings".
Step 2. Find or search the "Device Care" option (may be named differently depending on your device model and software version) and tap on it.
Step 3. Within Device Care, you should see options like "Storage" or "Storage & memory." Tap on it.
Step 4. Tap on "Storage" or "Advanced" to access more options.
Step 5. You should now see the option to "Clean Now" or "Clean Storage." Tap on it.
Clearing the cache can help remove any temporary files or data that spyware may have stored on your device.
Tip 5. Install reliable antivirus
Step 1. Find a reliable anti-spyware software.
Step 2. Install and download it inside Google play.
Step 3. Using the anti-spyware to scan your cell phone entirely.
Tip 6. Perform factory reset
If you're unable to remove the spyware or if you suspect it has deeply rooted itself in your device, performing a factory reset may be necessary.
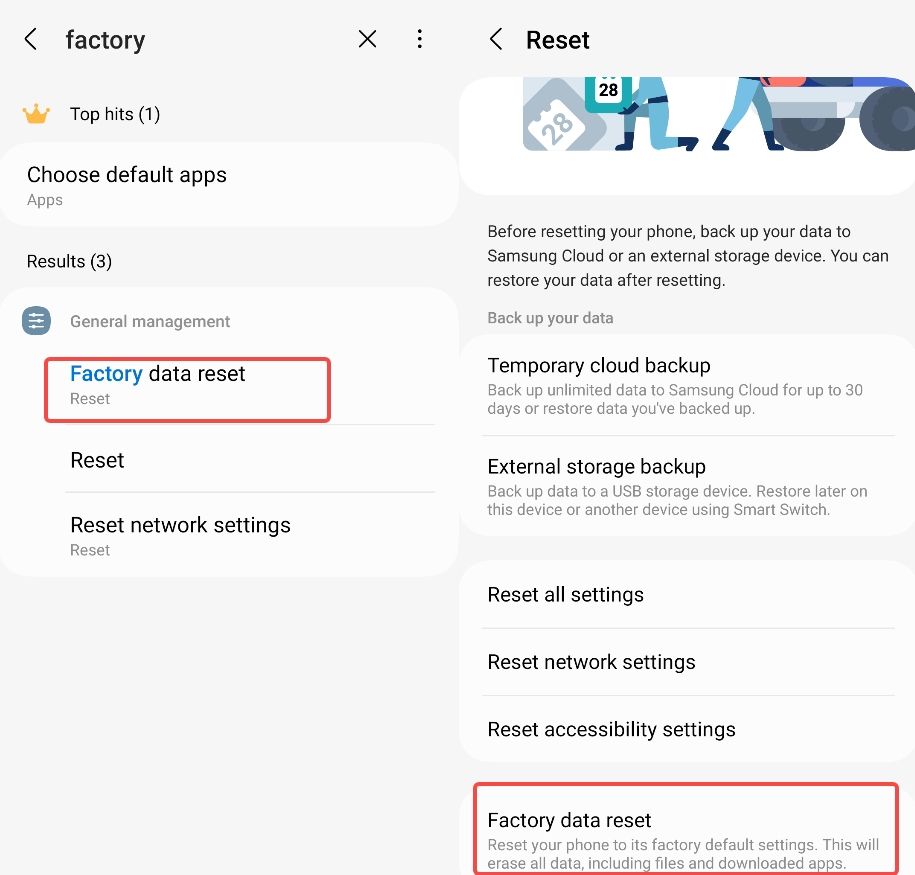
Step 1. Go to "Settings."
Step 2. Look for an option like "General management, " or "System," "Reset," or "Backup & reset."
Step 3. Select "Factory data reset" or "Reset phone."
Step 4. Follow the on-screen instructions to confirm and proceed with the factory reset.
Keep in mind that a factory reset will erase all data on your device, so make sure to back up any important files beforehand.
4.2. If you are an iPhone user
As an iPhone user to mitigate spyware detection and removal, follow the steps such as:
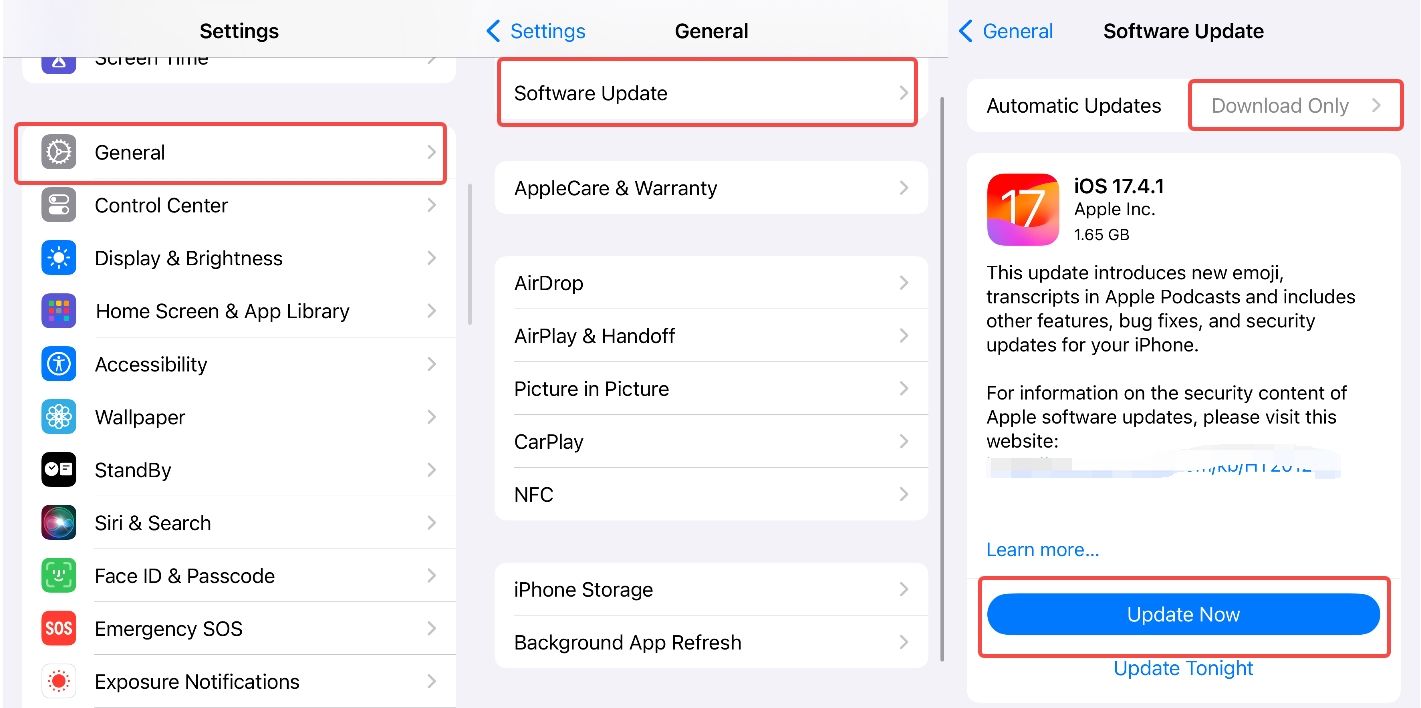
Tip 1. iOS Update
Step 1. Go to your iPhone's "Settings".
Step 2. Look for "General" and tap on it.
Step 3. Click on "Software Update."
Step 4. If an update is available, tap on "Update Now." (Of course, you can also turn on automatic updates.)
Step 5. Follow the on-screen instructions to complete the update process.
Keeping your iOS device updated ensures that you have the latest security patches and protections against spyware and other threats.
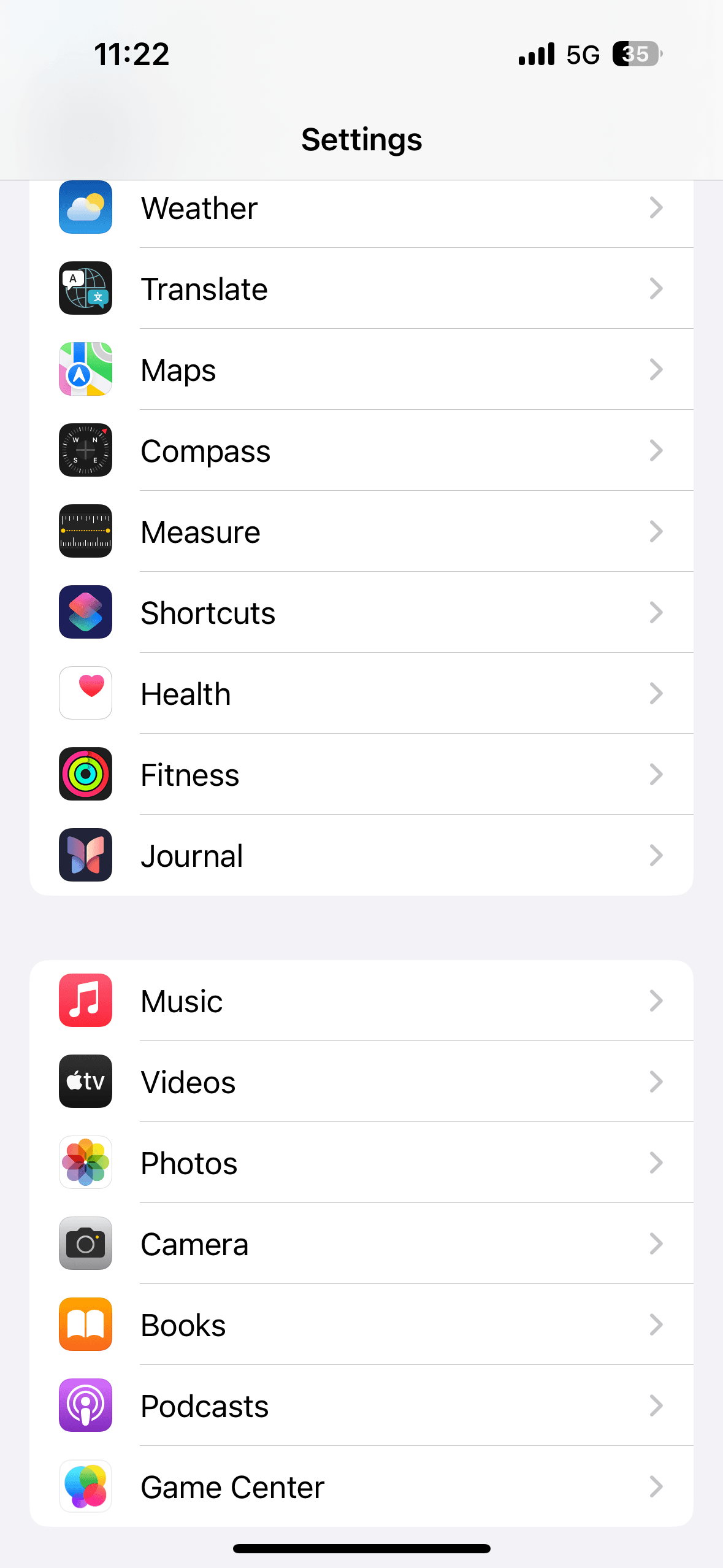
Tip 2. Figure out suspicious applications
Step 1. Go to "Settings".
Step 2. Scroll down and Look for any apps that you don't recognize or remember downloading.
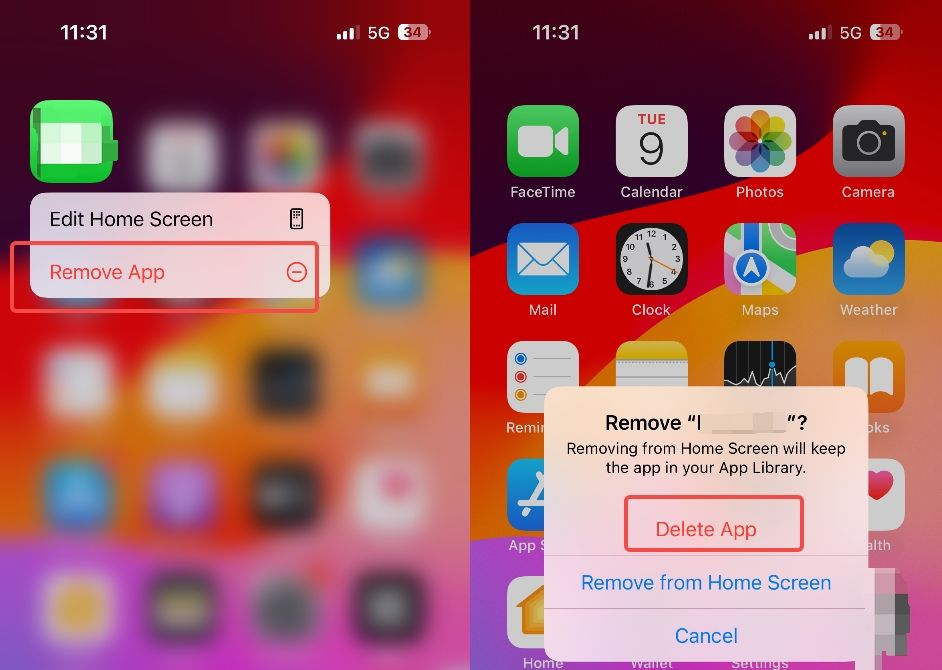
Tip 3. Uninstall suspicious applications
Step 1. Tap and hold on the suspicious app's icon until it starts to jiggle.
Step 2. Tap the "Remove App".
Step 3. Confirm that you want to delete the app by tapping "Delete App."
Step 4. Repeat this process for any other suspicious apps you find on your device.
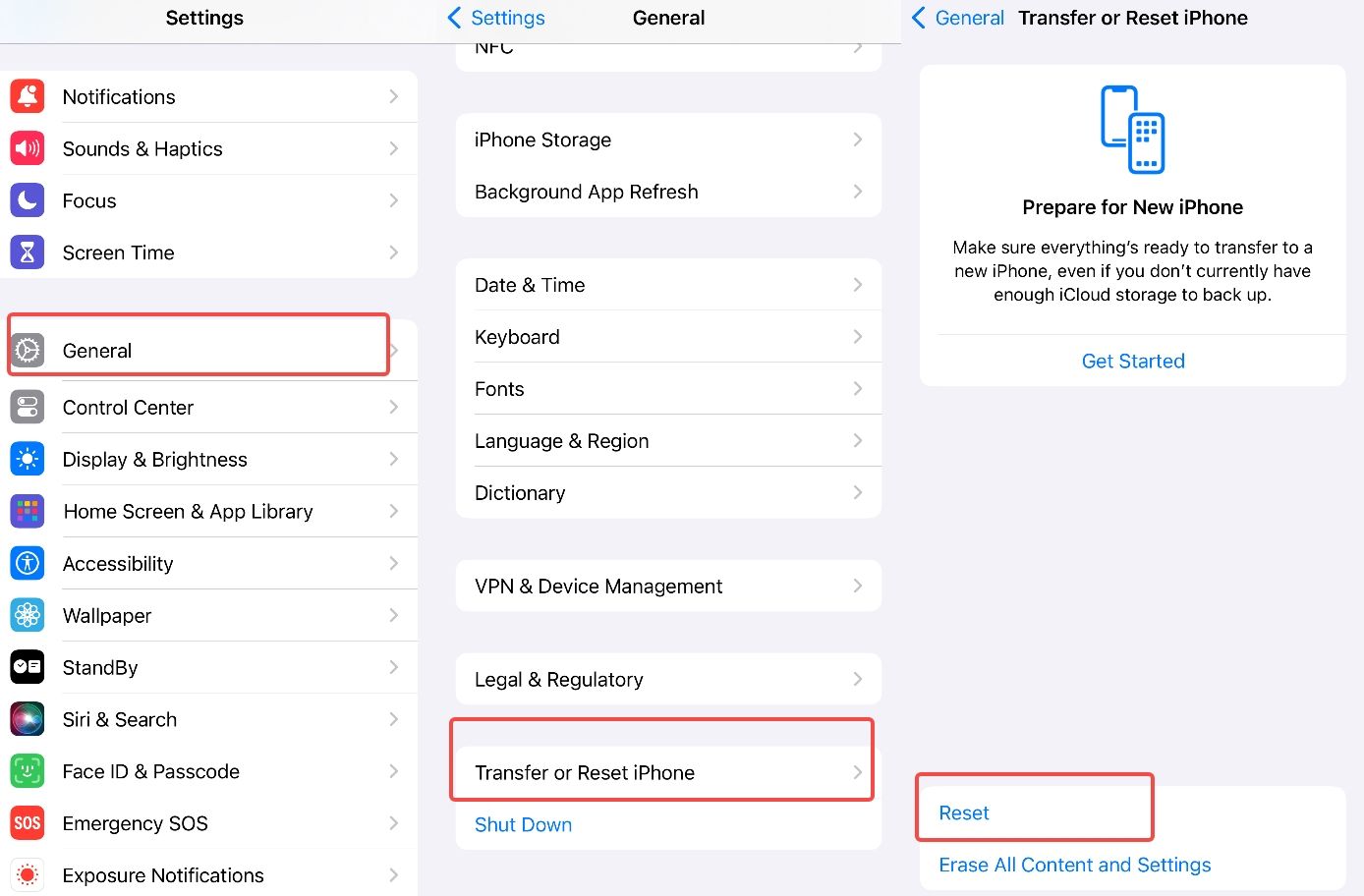
Tip 4. Reset iPhone Settings
Step 1. Go to your iPhone's Settings.
Step 2. Tap on "General."
Step 3. Scroll down and tap on "Reset." or "Transfer or Reset iPhone."
Step 4. Select "Reset All Settings."
Step 5. Enter your passcode if prompted.
Confirm that you want to reset all settings. This will revert your device's settings to their default configurations while preserving your data and media.
Keep in mind that a factory reset will erase all data on your device, so make sure to back up any important files beforehand.
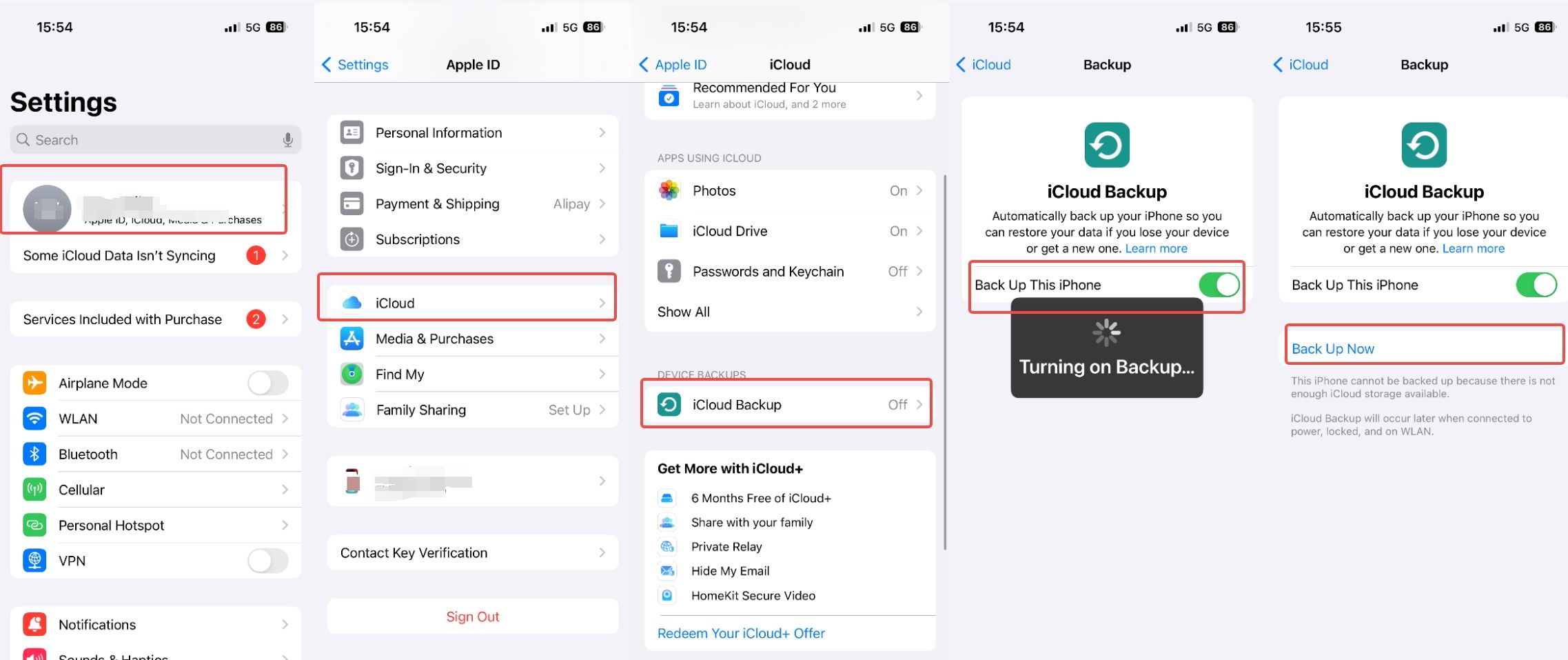
Tip 5. Restore Backup from iCloud or ITunes
Step 1. Connect your iPhone to your computer and open iTunes, or go to Settings > [your name] > iCloud > iCloud Backup and ensure that you have a recent backup available.
Step 2. Follow the on-screen instructions to restore your iPhone from the backup.
Restoring from a backup can help remove any spyware or malicious software that may have been installed on your device.
Part 5. How to protect your Android or iPhone from spyware
1. Only download apps from official app stores (Play Store for Android and App Store for iPhone).
2. Keep your device's operating system and apps updated.
3. Do not open the links that seems to be suspicious.
4. Avoid Interacting with unknown individuals through emails.
5. Use security features like passcodes and biometric authentication.
Part 6. FAQs of detection and removal spyware on your Android or iPhone
Q1. Can spyware be detected on a cell phone?
Yes, spyware can be detected using antivirus software that scans for malicious apps and files.
Q2. Can I scan my phone for spyware free?
Yes, many antivirus apps offer free versions that include spyware scanning capabilities.
Q3.How do I find and remove spyware from my phone?
You can find and remove spyware by using antivirus software to scan your device and following the instructions for removal.
Q4.Can someone install spyware on my phone without me knowing?
Yes, spyware can be installed on your phone without your knowledge if someone gains physical access to your device or tricks you into downloading malicious software.
Q5.What is the best free app to detect spyware?
Some popular free antivirus apps that include spyware detection features include Avast Mobile Security, Bitdefender Antivirus Free, and Malwarebytes Security.
Part 7. Conclusion
In the end, it's really important to know about the bad stuff like spyware that can sneak into your phone or computer.
Spyware is a sneaky program that can get into your device without you knowing, trying to steal your private stuff or mess with your phone's or computer's normal way of working. So, it's super important to keep an eye out and protect your device to keep your personal stuff safe.
More Articles Like This