How to check if phone is cloned

Last updated:févr. 28, 2024
Table of content
Hi, smartphone friends! Imagine yourself minding your business, emailing adorable cat videos to friends or planning your next journey on your phone. But then strange things start happening—calls from strangers, unexpected charges on your bill, or your phone acting up bit weird. In real life, your phone may be the main character of this mystery movie situation.
Phone cloning is a threat. Don't be afraid of the phrase. Cloning your phone is like a sneaky someone spying on your personal data without your knowledge.
What can you do? Consider this blog your superhero phone safety guide. Phone cloning will be discussed using simple tricks. Let's solve the mystery!
Part 1. How phone cloning works
Phone cloning is the transfer of data from one device to another. There are many methods of cloning. People most often need to clone the data of the old phone to the new phone when they change their phones. At this time, it is safest for users to choose to use the official method.
However, when someone wants to clone your phone and doesn't want you to know, they usually choose to use a third-party cloning tool. So with so much cloning software on the market, how do they work?
Next, we will take SpyX, one of the most popular cloning software on the market, as an example to see how it operates and what data it can clone.
Related read: How to Mirror Someone's Phone
1.1. Take SpyX as an example
SpyX is an all-in-one mobile phone clone software. It uses a variety of connectivity solutions to make cloning more convenient for users. For iOS users, they only need to bind the iCloud account of the target device to achieve cloning. For Android users, they can either choose to bind a Google account to clone data, or they can choose to download an APK.
No matter what kind of user you are, as long as you use SpyX, the data will be synchronized in real time. There is no need to rebind the device to clone the data, and the data can be synchronized every day.
Moreover, it runs in completely stealth mode, that is, no icon will appear on the target device, which means that if you use SpyX to clone someone else's phone, he will not know at all. SpyX encrypts the data transferred on the phone, making it difficult to detect.
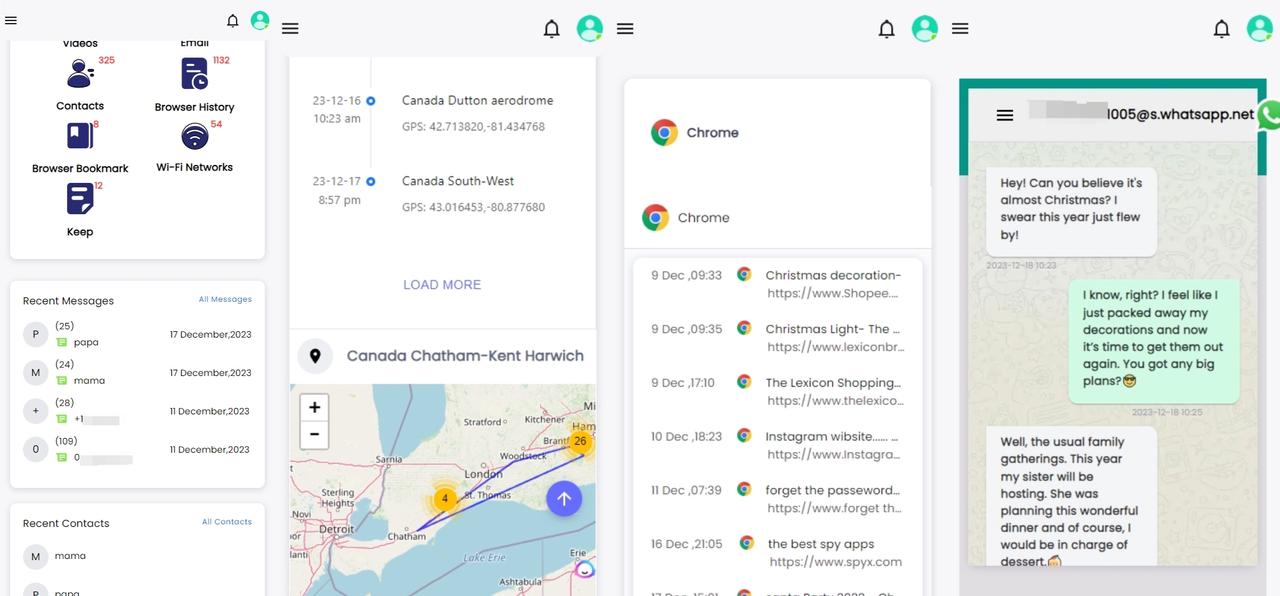
1.2. Which data can you clone using SpyX
SpyX is very powerful, capable of cloning 30+ software, and can clone almost all software contents. I divide it into several categories:
1.3. How to use SpyX to clone a phone
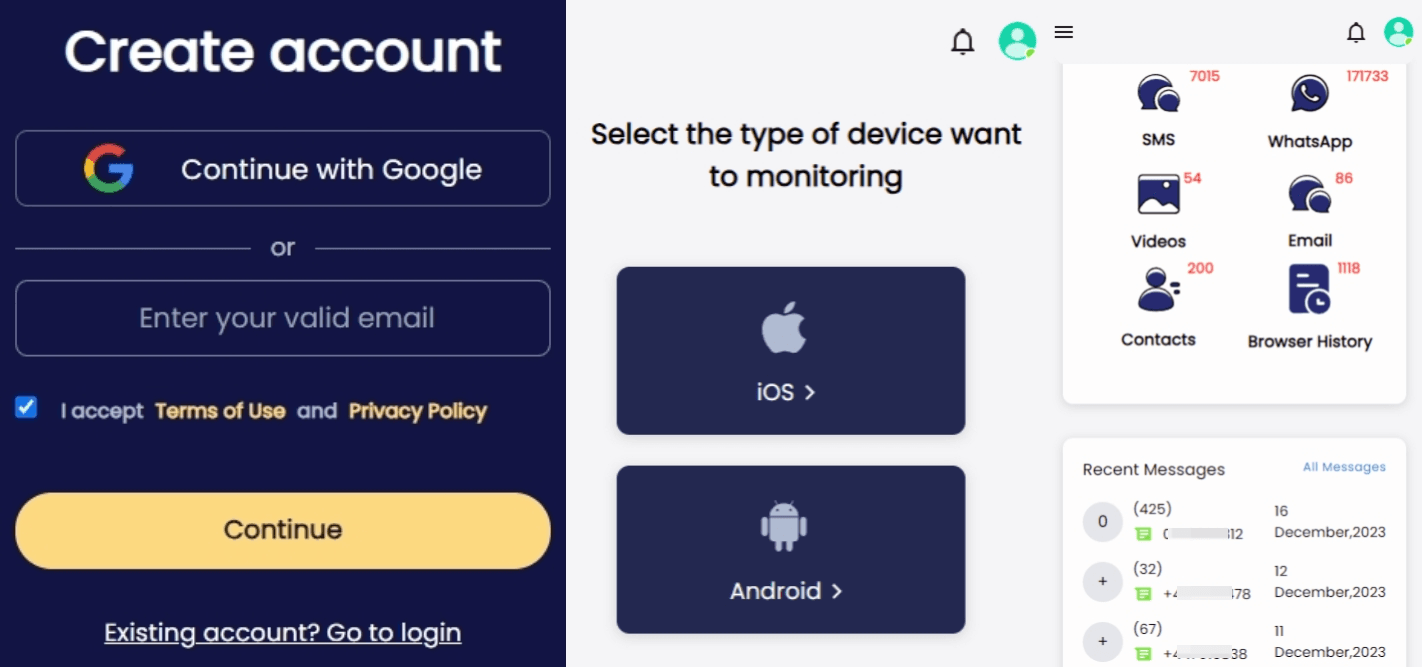
The operation steps of SpyX are also very simple. It only takes 3 steps to achieve remote cloning.
Step 1. Create a free account.
Step 2. Choose an iOS/Android device that you want to clone.
Step 3. Start cloning.
Further reading: How to clone a phone without touching it
Part 2. How to know if your phone is cloned
Have you ever felt like someone's been reading your digital diary? Your assumption may be right. Let's solve the mystery in our digital detective series: How can you detect a cloned phone?
- Mystery battery drains
Imagine your phone battery partying and draining faster than "tech trouble." This is a major red flag. If your battery seems to be racing against time, your phone may be cloned. Cloning makes your phone perform double shifts, draining its battery.
- Increased Data Use
Monitoring data usage is important online. Imagine your data plan acting like a superhero but running a marathon while walking. A sudden increase in data use may indicate a clone on your phone. Inspect your device if your data is disappearing faster than usual.
- Mysterious Calls or Texts
Ever had a friend mention a call or text from you, but you have not made it? Unfamiliar phone numbers often appear in your call history? Clones can make your phone talk and text without your awareness. Look at your call and text history, it may show a digital cloner.
- Overheating
Monitor your phone's temperature, especially if it's hotter than usual. Imagine your phone getting a fever without notice. Overheating generally indicates cloning. Clones work silently in the background, generating heat while committing crimes.
- Text message delays and failures
Communication is crucial, but what if your texts disappear? Imagine sending a message anticipating a quick response, but your friend responds hours later. Phone cloning could cause this disappearance. Clones can delay or disappear messages, making conversations confusing.
- Higher phone bills
Phone bills are financial diaries, but what if they become fiction novels with surprising plot twists? If your phone costs are rising unexpectedly, the phone clone may be responsible. Examine those bills—they may reveal if the phone if cloned.
Part 3. What are the dangers if your phone is cloned
Cloning your phone by a "stranger" may put your private information and property in an unsafe state, and may even harm the interests of others.
- Personal information leakage
If your phone is cloned, your personal information may be stolen, including sensitive information such as contacts, call records, text messages, and social media accounts.
- Property losses
By cloning a phone number, criminals can obtain sensitive personal information, such as bank account information, ID numbers, etc., causing property losses.
- Identity theft
Using a cloned phone number to impersonate your identity, perform false identity authentication or commit fraud, harming the interests of others and causing serious losses to the victim.
- Security Vulnerabilities
Having your phone cloned may also expose your device to additional security vulnerabilities, making you more vulnerable to malware or cyberattacks.
Part 4. How to stop someone from cloning your phone
4.1. Stop phone cloning on iPhone
Hi iPhone users! A stranger entering our personal space but how can we know? If you suspect your iPhone is being watched by spyware due to cloning, we'll help you find and stop it.
- Checking your phone's IMEI number
Your phone's IMEI number is like a fingerprint in the digital world. Compare the IMEI number on your iPhone to the one registered with your network provider to check for cloning. To find your iPhone's IMEI, go to Settings > General > About or dial *#06#. These numbers mismatch, suggesting cloning.
- Understanding Phone Behaviour: Red Flags
Strange device activity may indicate a problem. Beware of strange texts or calls from unknown numbers, which may indicate phone cloning. Detecting these minor indications requires vigilance.
- Phone Inaccessibility
An unexpected inability to make or receive calls or texts, excluding emergency numbers, can be concerning. If you clone and activate your SIM card in another device, the network may assign your number to that device, making your phone services inoperable.
- Unexpected Device Restart Requests
Attackers may send unsolicited texts asking you to restart your phone to acquire more control over your cloned phone or SIM card.
- Unusual Phone Bill Activity
Unknown numbers dialled or charges on your phone account are cause for concern. Attackers may use your number for fraud or impersonation, causing irregular charges.
- Suspect Cloning
4.2. Stop phone cloning on Android
Cloning an Android device isn't easy, but it leaves traces. Key indicators that your Android may have been cloned are listed below.
- Call and text reception disruptions
Cloned Androids become puppets on someone else's strings, breaking communication. A rapid drop in calls and messages may indicate unauthorised cloning.
How to Check
Ask friends and family to call you to test.
Increasing calls and texts from unfamiliar numbers may indicate cloning.
- Phone Location Duplicates Unmasking
A simple IMEI cloning trick might make your phone appear in two places. Use Find My Phone (Android) to examine this phenomenon.
How to Check
Use locator apps like Find My Phone (Android).
The map may show several pings, indicating a cloned device.
- Unexpected Phone Bill Charges
Check your phone statement for unusual expenditures like international roaming or subscriptions. Billing irregularities may indicate cloning.
How to Check
Check your phone bill for unauthorised charges.
Verify unusual charges with your carrier.
- Recurring Account Hacks Show Intrusion
Consistent Gmail, bank account, or other account intrusions may indicate a cloned phone. Phone cloning may enable recurring intrusions, even if you've strengthened your accounts with new passwords and 2FA.
How to Check
Despite security updates, check accounts for unauthorised access.
Keep in mind Android cloning if your accounts are compromised.
- SIM Update Messages: Unexpected Alert
The presence of a "SIM Updated" notice without any phone or account changes is suspicious. Certain cloning methods may result in this message, indicating unauthorised device activity.
How to Check
Watch for unexpected "SIM Updated" messages.
Cloning may occur if there have been no recent alterations.
- Text restart requests: A Secret Activation
Unexpected texts prompting you to restart your Android may be a trick by criminals to activate a cloned SIM card. You may unintentionally activate by responding.
How to Check
Watch out for unexpected restarts.
If you've answered such inquiries, contact your carrier about SIM card replacement.
Part 5. How can you protect yourself from cloning
In a digital age where phones are essential, protecting them against cloning is crucial. Here are Six steps to protect your phone from unauthorised access.
- Use Strong Passwords
Use strong passwords and fingerprint or face recognition to unlock. This prevents attackers and improves protection to prevent unauthorised access.
- Enable 2FA: Double Defence
Two-factor authentication is essential for accounts like Apple ID and email. This extra step ensures that even if someone has your password, they need a supplementary verification, boosting security.
- Check phone bills regularly: Financial Vigilance
Check your phone bills for odd expenses or activity. Early discrepancy discovery can prevent cloned device financial exploitation.
- Avoid clicking suspicious links: Digital Firewall
Be cautious online. Avoid clicking on dodgy links and downloading programmes from unknown sources. These may allow phone cloning attacks.
- Update Phone Software to Prevent Vulnerabilities
Update your phone's OS regularly. These upgrades usually include security patches to protect your device from cloning.
- Encrypt sensitive data
Encrypt crucial phone data. Encrypted data makes unauthorised access or cloning difficult, adding a layer of defence.
- Beware Unexpected Messages or Restart Requests
Receive unexpected messages or phone restart requests with caution. Attackers may employ such methods to clone. Before acting, verify such messages' veracity.
- Regularly Check Duplicate Locations
Regularly check your phone's location settings and Find My Phone for duplicate locations. This may indicate cloning attempts, allowing you to intervene quickly.
Part 6. Conclusion
The potential of phone cloning becomes a major concern as we handle smartphones and our personal and digital lives. Understanding the subtle aspects of potential cloning is crucial in an age when our devices hold our most private data.
This exhaustive digital detective guide understands the complex signals that could suggest phone cloning, from abrupt battery depletions that indicate a device's secret workload to mysterious text message delays that make users doubt their digital communication. The guide goes beyond detection, giving iPhone and Android users comprehensive cloning prevention measures.
In this article, we clarify the potential harm caused by the cloning of phones and phone numbers, and propose protective measures against phone cloning. For this, it is recommended to use strong passwords, two-factor authentication, and careful phone bill monitoring for signs of unauthorised access.
By playing the role of digital detectives with knowledge and preventative actions, you can firmly protect your digital identity and keep their cellphones safe from hidden threats and mysteries.
Part 7. FAQs
Why would someone clone a phone?
Phone cloning is often done for malicious motives, giving unauthorised access to personal data, messages, and call histories. Cloners may steal identities, exploit financial data, or perpetrate fraud. It may be done for espionage or secretly monitoring the target's conversations.
Does phone clone transfer all data?
Yes, phone cloning includes copying the target phone and transferring all data to it. This includes call history, text messages, phone numbers, photographs, apps, and other device data. It copies every phone's content.
Does clone phone need wifi?
Most phone cloning does not require Wi-Fi. SIM card cloning or physical access can clone a device. However, complex cloning methods may require an internet connection to download and install software.
How long does phone clone take?
Phone cloning time depends on method and complexity. More complex software-based solutions may take longer than SIM card cloning. Cloning takes a few minutes to several hours, depending on the amount of data sent.
What is the code to check if phone is cloned?
There is no universal code to detect cloned phones. Users can check for strange activity like high battery draining, unexpected text messages, or unfamiliar calls to detect cloning. Monitor your phone bill for unauthorised charges or irregularities to indirectly discover cloning efforts. Contact your mobile service provider if unusual activity is detected.
More Articles Like This