How to Clone Phone Number Easily & Remotely

Last updated:3月 04, 2024
Table of content
The concept of cloning phone numbers has got attention in our digitally interconnected world, providing a solution for diverse needs. This comprehensive guide presents an exploration of the methods of cloning a phone number. It also explains associated risks and recommends an efficient tool.
Part 1. What is a clone number
At its core, mobile phone cloning engages in the complex procedure of duplicating a phone number to allow for its simultaneous use on various devices.
This process goes beyond just duplication. It involves careful replication of an entire digital identity linked with one specific phone number.
The objective is to establish an identical twin within the digital landscape and facilitate effortless communication across diverse platforms.
The complexity of mobile phone cloning lies in the nuances of its processes. The digital replication goes beyond a surface-level duplication, ensuring that the cloned number functions in every aspect like its original counterpart.
This involves replicating not just the phone number but the entire set of associated data, including call logs, text messages, and other relevant information.
The result? A cloned number that is virtually indistinguishable from the original, facilitating its use on multiple devices without any discernible difference in functionality.
Part 2. 3 Ways to clone phone number easily
In this part, we will introduce 3 methods to clone cell phone number effectively. The operating conditions and specific steps for each method are also described.
2.1. How to clone a phone number remotely through SpyX
With SpyX you can achieve remote cloning of all the data on your phone including phone number cloning. Although SpyX is a third-party tool, it is a software that can be used without jailbreaking, rooting or downloading.
And users don't have to worry about privacy leakage, SpyX adopts bank-grade data transmission technology to give you 100% data security.
Features
Conditions of operation
- Requires subscription.
Specific steps
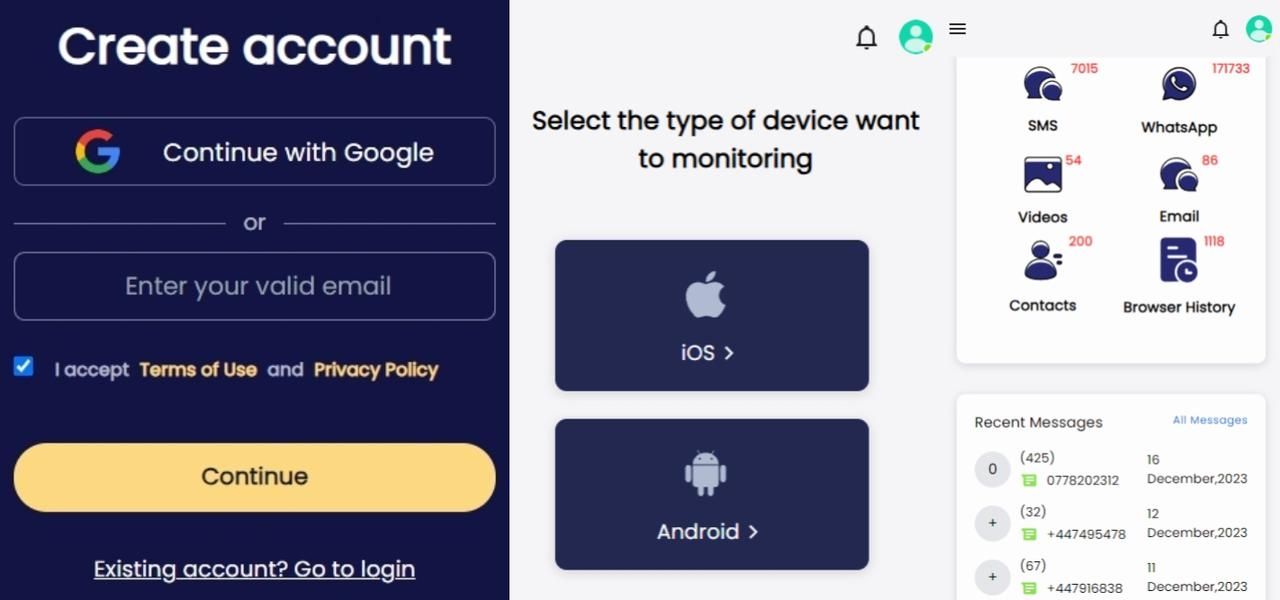
Step 1. First, you need to create an account on the SpyX website. You can use Google email or any other valid email for completing your subscription.
Step 2. Choose the target device you want to clone. If you are cloning an Android device, select Android. Otherwise, select iOS.
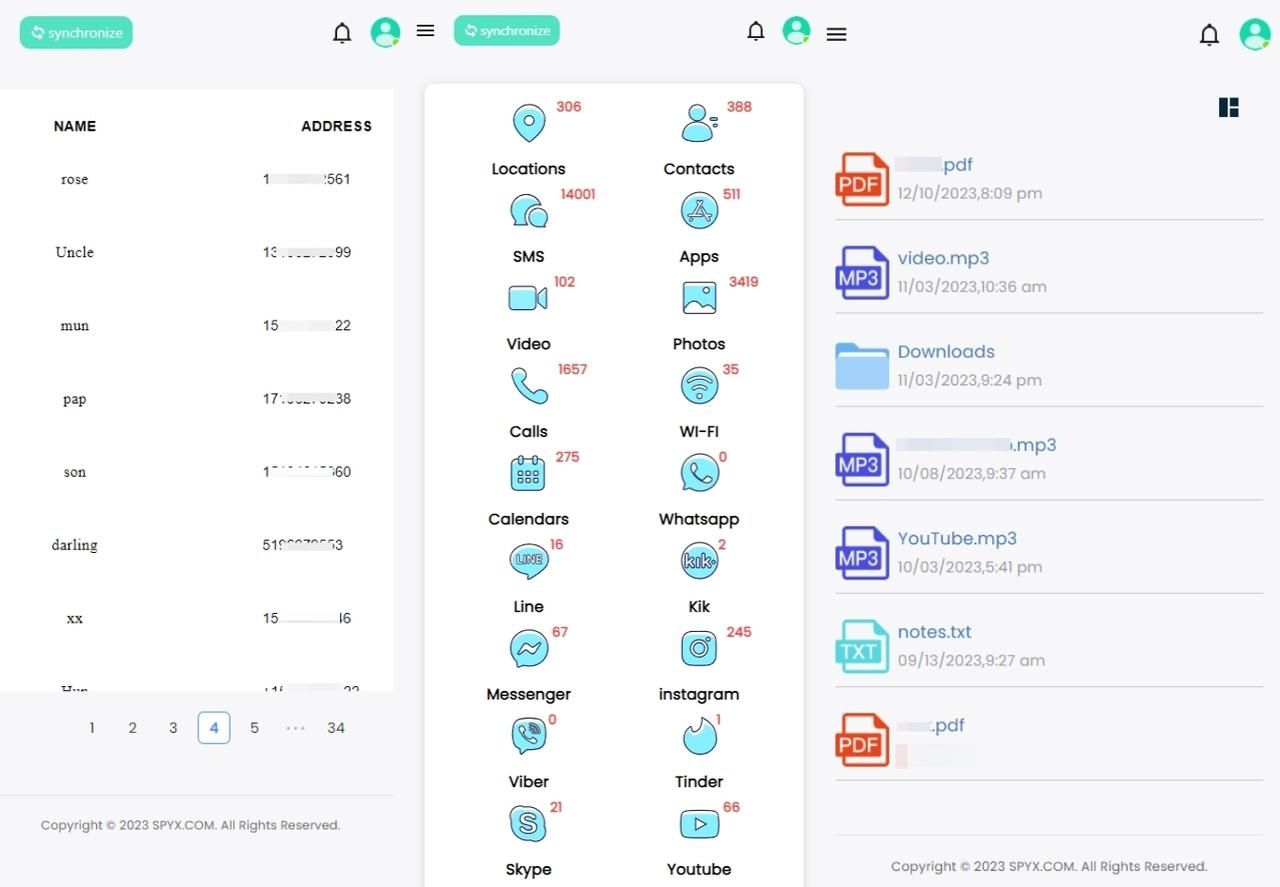
Step 3. Click synchronize data and start cloning. Find "calls/contacts" in the sidebar or dashboard. Click it, then you can see all phone numbers on the target device.
2.2. How to clone numbers via backup
Delving into the world of cloning a phone number via backup requires a deep understanding of various backup methods such as cloud backups, local computer-based backups, and third-party applications designed for data preservation. Each method offers unique advantages and considerations, catering user's diverse needs and preferences.
Modern smartphones often integrate cloud backups, enabling users to remotely store their data. This includes but is not limited to contacts, call logs, messages, and other critical information associated with a phone number. On the other hand, local backups involve the preservation of data on either a computer or an external storage device.
This offers users increased control over their information. Third-party applications designed for backup offer additional features. Users can selectively choose the data they want to store and replicate.
Conditions of operation
To clone a phone number via backup, the user must fulfill specific conditions.
- The backup should be recent.
- It should also be comprehensive and compatible with the target device.
- A recent backup guarantees the cloned number reflects the latest information, while completeness ensures replication of associated data.
- For a seamless integration into the new device, compatibility factors such as operating systems and device models must also be considered.
Meeting these conditions is essential for a successful cloning process.
Specific steps
Executing the cloning process via backup involves specific steps that users can follow seamlessly:
- Backup creation: Start the backup process on the original device, ensuring that all desired data is included.
- Transfer to target device: Transfer the backup file to the target device using preferred methods such as cloud storage, USB connection, or external storage.
- Restore from backup: On the target device, initiate the restoration process using the backup file. This step varies depending on the device and backup method used.
- Verification: Make sure the cloned number's functionality by making test calls, sending messages, and checking other associated data.
By following these specific steps, users can effectively clone a phone number via backup, creating a replicated digital identity on the target device.
2.3. How to copy phone numbers using SIM card
The use of a SIM card to copy phone number offers a straightforward and practical solution to users seeking duplication capabilities. The Subscriber Identity Module (SIM) card, functioning as your phone's connection to cellular networks through its small chip, plays an integral role in this process.
The SIM card, typically associated with activating phone services, holds vital information, including the user's identity and contact details. Understanding its potential for phone number duplication involves recognizing the significance of this unassuming chip in facilitating communication on cellular networks.
Conditions of operation
- Before starting to copy phone number with a SIM card, ensure the smooth operation of your device by verifying its compatibility with the SIM card.
- Most modern smartphones have SIM card slots, but confirming this is essential.
- Check for necessary software or apps, adjusting settings if needed.
- Ensure the SIM card is functional, correctly inserted, and recognized by the device.
Specific steps
Now that the groundwork is laid with an introduction and understanding of operational conditions, let's dive into the specific steps involved to copy phone number using a SIM card.
- Access device settings: Firstly, users should access the device's settings, where they can locate the 'SIM card' or 'Phone' settings, depending on the device's interface.
- Locate SIM card management option: Within these settings, users may find an option for managing or copying contacts from the SIM card.
- Activate copy contacts feature: Activating this feature initiates the copying process, where the device transfers selected or all contacts from the SIM card to the phone's internal storage. Users are often prompted to choose specific contacts or batches for duplication.
- Cross-verify operation success: Upon completion of the copying process, it's advisable to cross-verify the success of the operation by checking the phone's contact list.
- Seamless integration: This final step is to make sure that the copied phone numbers are seamlessly integrated into the device, and ready for use.
The specific steps provided here serve as a practical guide for users, demystifying the process and empowering them to efficiently copy phone number using a SIM card.
Part 3. What are the risks of number cloning
While the idea of phone number cloning might initially seem like a convenient solution, users need to be aware of the inherent risks associated with this practice. You may wonder how to check if your phone is cloned.
- Identity theft
Cloning numbers opens the gateway to potential identity theft for users. The cloned number could be exploited for various fraudulent activities if in the wrong hands. Such risk extends far beyond mere inconvenience.
It poses a tangible threat to the personal and financial security of the user. This is why it is paramount that individuals exercise caution when considering cloning numbers.
- Privacy invasion
The act of cloning number introduces a significant risk to user privacy. By gaining unauthorized access to personal messages and calls, malicious entities could exploit sensitive information. This invasion of privacy goes beyond the digital world. It could potentially impact the user's real-world interactions.
Understanding the potential consequences of such privacy breaches highlights the importance of evaluating the necessity and security of cloning numbers.
- Legal consequences
Engaging in phone number cloning is not without legal implications. Users should be aware that this practice may lead to serious charges related to privacy invasion, fraud, and unauthorized access. Legal consequences can be more than just personal repercussions.
Those could affect individuals both financially and reputationally. This aspect emphasizes the need for users to weigh the potential risks against the expected benefits. It’s crucial to understand that the legal ramifications of cloning numbers are not to be taken lightly.
Part 4. Conclusion
The bottom line is that navigating the intricate world of phone number cloning emphasizes the need for a method that balances efficacy and security. SpyX emerges as the optimal solution, extending beyond mere number cloning with its comprehensive functionality.
This versatility ensures a holistic digital solution, reinforcing SpyX as a reliable tool. Privacy protection further solidifies SpyX's trustworthiness in a landscape dominated by privacy concerns. The convenience of remote operation and real-time data synchronization enhances SpyX's allure, allowing users to manage data securely from a distance.
In essence, SpyX is more than just a secure, user-friendly platform for comprehensive digital data management. This makes it the recommended choice for efficiently cloning numbers.
Part 5. FAQs about cloning phone number
Which phone clone is best?
The choice of a phone clone depends on individual needs. SpyX is highlighted for its versatility, providing comprehensive features beyond merely cloning numbers.
Can two devices use the same phone number?
No, a phone number is unique to a single device. Attempting to use the same number on two devices may lead to connectivity issues and service disruptions.
What happens if your phone number is cloned?
If your cell phone number is cloned, then your call history may be monitored and the cloner may be able to access your personal information and private data, including bank account numbers, social media information, and more.
And they may use your cell phone number for fraudulent activities, resulting in financial losses. You may also be implicated in legal disputes if they use your cell phone number for illegal activities.
Why would someone clone my phone number?
Some people may want to clone your cell phone for legitimate purposes. For example, parents may want to clone their children's cell phone numbers in order to monitor their telecommunications activities to ensure their safety.
An employer may clone an employee's cell phone number in order to monitor the employee's communication activity on company devices to maintain the security of the corporate network.
A law enforcement agency or emergency response team may clone a person's cell phone number in order to track or locate his or her location in order to provide assistance in an emergency.
Is cell phone cloning software safe?
In fact, not all cell phone cloning software in the market are safe. So you should pay attention to the developers and intentions of the software. SpyX phone tracker with high safety and advanced technology, which wins the trust of customers around the world.
Can someone clone your phone without you knowing?
Yes, users can use advanced spy software with stealth mode, such as SpyX. It can run invisibly and undetectably. Users can use it to monitor the data information of the target mobile phone in real time, and the monitored person will not know.
More Articles Like This