10 Best Text or SMS Monitoring Apps

Last updated:mag 29, 2025
Table of content
SMS or text messages are widely used worldwide. SMS is an easy, fast and convenient communication method since it does not require data/Wi-Fi to send or receive a message. The service can be used by anyone with a mobile phone and phone number. Tracking text messages is necessary for parents looking out for their kids. The text message tracker you use determines the accuracy and legitimacy of your SMS tracking. There are thousands of SMS spy apps today, and many don't work. Knowing and choosing the right SMS spy app can be quite a challenge. This article looks at reasons for tracking text messages, the 10 best text message spy apps available, their features, and how to use them.

Part 1. 10 Best Text or SMS Spy Apps
1. SpyX- Text Spy App
SpyX is a very powerful monitoring app that can track sent messages, received messages, deleted messages, the sender/recipient, and the timestamps for sent or received. Besides SMS tracking, SpyX can track calls, emails, social media apps, and a target device's location and browser history. The app has a control panel from which you can read messages of the target device as they are received or sent without physically accessing it. An incredible feature about SpyX is the fact that it is undetectable.
To use the SpyX SMS tracker app:
Step 1. Go to the SpyX website and signup.
Step 2. Choose a subscription
Step 3. Connect target phone with SpyX
Step 4. Log into your control panel to start spying.
2. MobileSpy- Spy App for Text
The MobileSpy app is a good SMS tracker for iPhone and Android devices that can read sent and received SMS on a target's device without detection. The app enables you to read MMS and access all SMS log history. View all text messages without accessing the target's phone with MobileSpy by simply going to the MobileSpy website, registering your account, and choosing a subscription. After paying the subscription, SpyX will send installation guidelines to you via email. Log in to your dashboard after installation and start monitoring.
3. XNSPY-Text Spy App
XNSPY is a text spy app compatible with Android smartphones, tablets, iPhones, and iPads. The app requires one-time access to the target's device to set up and start monitoring. After installing the XNSPY app, a waiting period of 24-48hrs is required for initializing. To get this app, install it from the XNSPY website and follow the procedures for setup on the target device. Log in to your remote control dashboard and select text messages to read.
4. TrackMyFone- Spy App for Text
TrackMyFone is a spy app for text messages that Android and iPhone phones use to track a target person's device. With this app, you require jailbreaking to initiate a spy. The app tracks received and sent messages which you can access from your control panel. You can download the app from the TrackMyFone website.
5. Spyic- Spy App
Spyic qualifies as one of the best text spy apps for Android and iOS devices. With tis app, you can remotely monitor messages, calls, locations, and apps on a target device. With Spyic, you can view the contact number that your child, spouse, or employee is exchanging messages with alongside their timestamps and names.
6. SpyEra- Spy app
SpyEra is an efficient undetectable Spy Phone and PC Spy available for Android and iOS devices. An easy web control panel can remotely monitor a target device from anywhere. Moreover, the app provides free updates to enable you to enjoy new features on your current plan. Spy on text messages, calls, and location affordably by getting the SpyEra app.
7. Blurspy- Text Spy App
Blurspy Text Spy App is a hidden SMS tracker for android devices. This SMS spy enables you to view and read SMS conversations, block text messages and receive alerts on keyword typing. The app can also provide monitoring and tracking for calls, social media, gallery contents, and locations.
8. MobiStealth- Spy App
MobiStealth Spy App is a quick android and iOS tracking device available on the web. With the remote control of your MobiStealth, you can monitor SMS sent and received on a target device in 3 steps. Search MobiStealth on the web, register, connect your device and start monitoring your spouse, employee, or child.
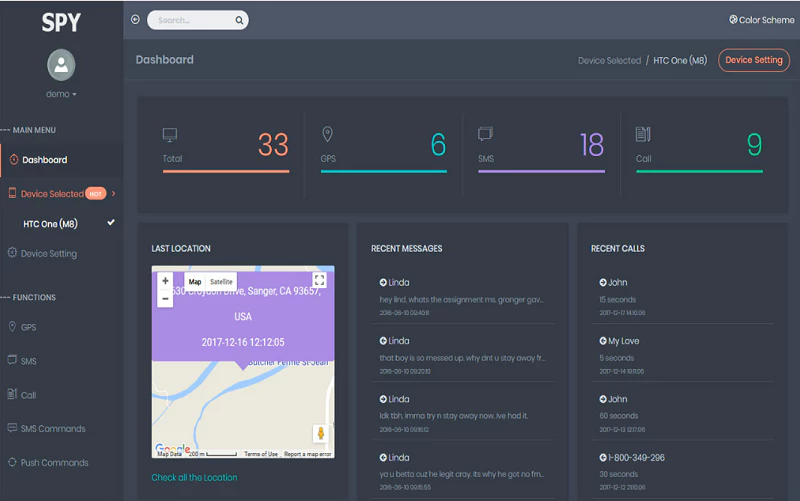
9. GuestSpy- Text Spy App
GuestSpy is an android call and SMS tracker that can track all sent, received, and deleted text messages on a target device. Other SMS details you can access with Guest Spy include sender or recipient details and the time and date the message was sent or received. The app can track all other phone details and activities.
10. The TruthSpy- Spy App
The TruthSpy Spy App is a mobile monitoring app that is compatible with Android and iOS devices and is majorly used by businesses to monitor employees. The app has a fixed plan with no free plans or free trials. The app enables employers to monitor their employees' phone activities.
Part 2. Why Track Someone's Text Messages
1. Protective Parents
A caring parent will put the safety of their children first, and since you cannot always be present to keep an eye on them, a tracking device is an important accessory for monitoring.
2. Productivity-focused employee
Time is money, and every successful business takes labor hours seriously. They have unethical and unprofessional employees who cannot work without supervision call for a call and SMS tracker to know when they are using work time to send messages or stay on calls instead of working.
3. Couples who suspect they are being cheated on
A cheating spy will exchange text messages with the other partner because it is a quick communication method. When you suspect that your partner is cheating and you can't confront them with the suspicions, an SMS tracker app will help you confirm your suspicions.
Part 3. Factors for Purchasing SMS Spy App
1. Reliability
The text message tracker should be built and updated with advanced software that works and has zero or minimal breakdowns that can hinder you're tracking. Some apps are well built, while others are full of troubleshooting errors.
2. Features
A good monitoring app should have advanced features to enhance full spying on a target device. Partial spying is unpleasant and can leave one dissatisfied. A good monitoring app should have unlimited features.
3. Stealth
A good spy app should be invisible and undetectable to the targeted spying. When a spy app is detected, it can be removed, or the target person might reduce activity on the target on their device and leave you with little or nothing.
4. User-interface
A spy app user interface should be simple, fast, and effective with no sophisticated processes to enable a user to conduct remote monitoring smoothly.
5. Price
The price of a spy app determines it is accessible to users. Prices vary from one spy to another. Some apps have fixed plan subscriptions, while others have different classes of plans to accommodate everyone. However, the price you choose to pay for spy services also influences the number of features you access on a spy app.
6. Support
A good spy app should have 24/7 customer care support to respond to customer complaints and queries. Sadly not all apps offer 24/7 customer care support. If you go for an app without 24/7 customer care attendance, you will have to wait till a customer agent gets back to your complaint or query, which might take days or weeks.
FAQs
Q1. Is there an app that lets you see someone else's texts?
SpyX is one of the best apps to spy on text messages designed to check another person's smartphone activity. It can monitor someone else's texts and social media chats remotely.
Q2. Are text message phone spy apps safe?
Most text message phone spy apps use encryption to keep data safe and secure. Only the user of the spy app can see the messages that are being sent or received from a target phone, and this data is not shared with third parties.
Q3. Can text message spy apps be detected?
Text message spy apps are designed to operate with stealth. They don’t have an app icon on the target phone and don’t show up in most places a user might look. SpyX is web-based service. You don’t need to install app on the target phone.
Q4. Why do you need a free SMS tracker?
1. You may want to track the messages sent by your children to keep them safe.
2. You may suspect that your spouse is cheating on you, and you want confirmation.
3. SMS trackers app also provides useful when you want to track the messages of your employees.
Q5. What are the best SMS tracker apps without installing on the target phone?
1. SpyX
2. mSpy
3. ClevGuard
4. XNSPY
5. Hoverwatch
6. Umobix
7. FlexiSPY
More Articles Like This