How to see someone else's text messages on iPhone
Table of content
In an era of heightened digital communication, knowing how to access someone else's text messages on an iPhone has become a common concern. This article will guide you through legitimate methods which are simple yet effective. Explore the motivations behind this need and discover trustworthy ways to achieve it.
Part 1. How to see someone else's iphone messages for free
1.1 iTunes backup
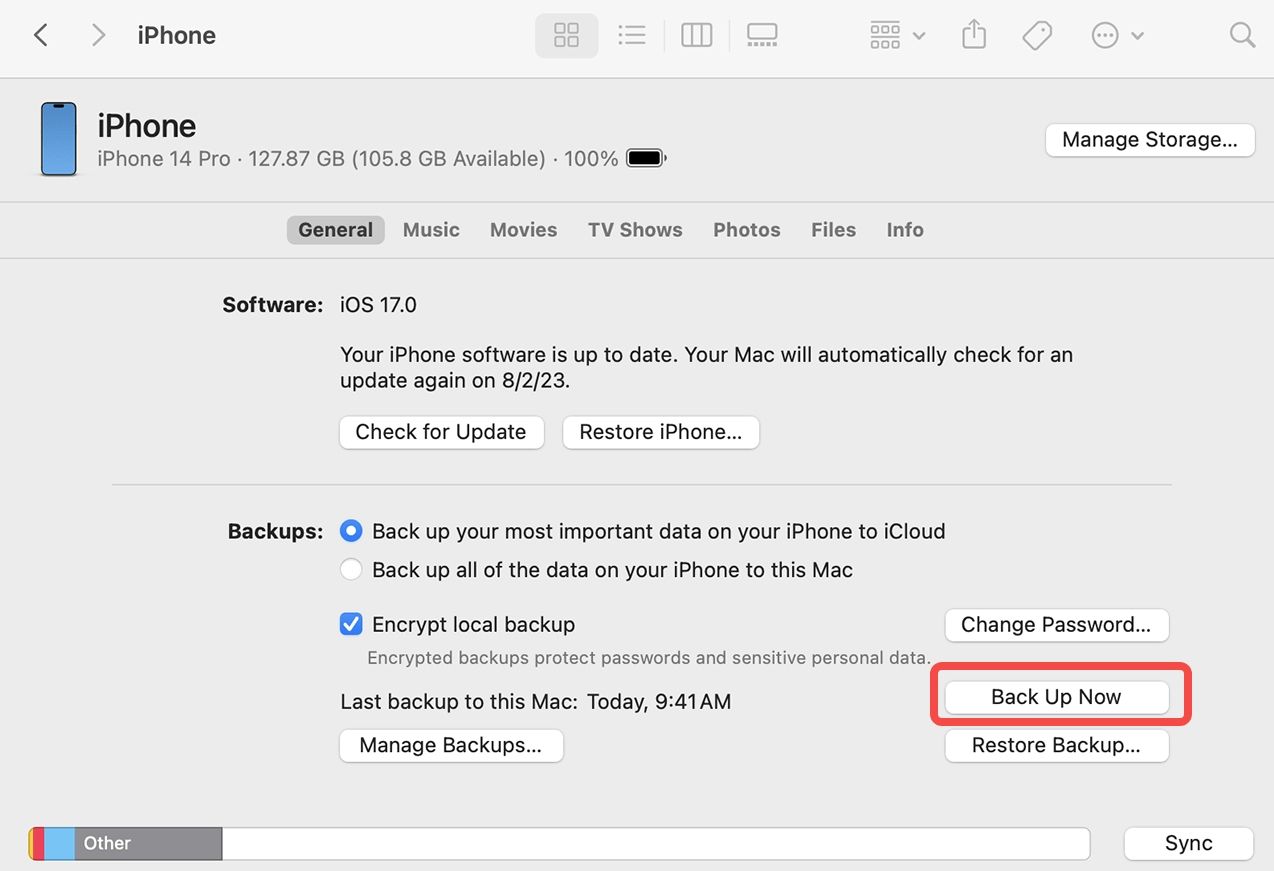
Utilizing iTunes backups is a straightforward method to access someone else's iPhone messages. When iPhones are connected to iTunes for regular backups, a wealth of data, including text messages, is stored. This method taps into this stored information for viewing text messages.
Features - what SMS data can be viewed
Steps
- Connect the target iPhone to the computer with the associated USB cable.
- Open iTunes and select the device.
- Navigate to the "Summary" tab and click "Restore Backup."
- Choose the relevant backup file, preferably the most recent one.
- Click "Restore" and wait for the process to complete.
- After restoration, explore the text messages by opening the Messages app on the computer.
1.2 Using iCloud
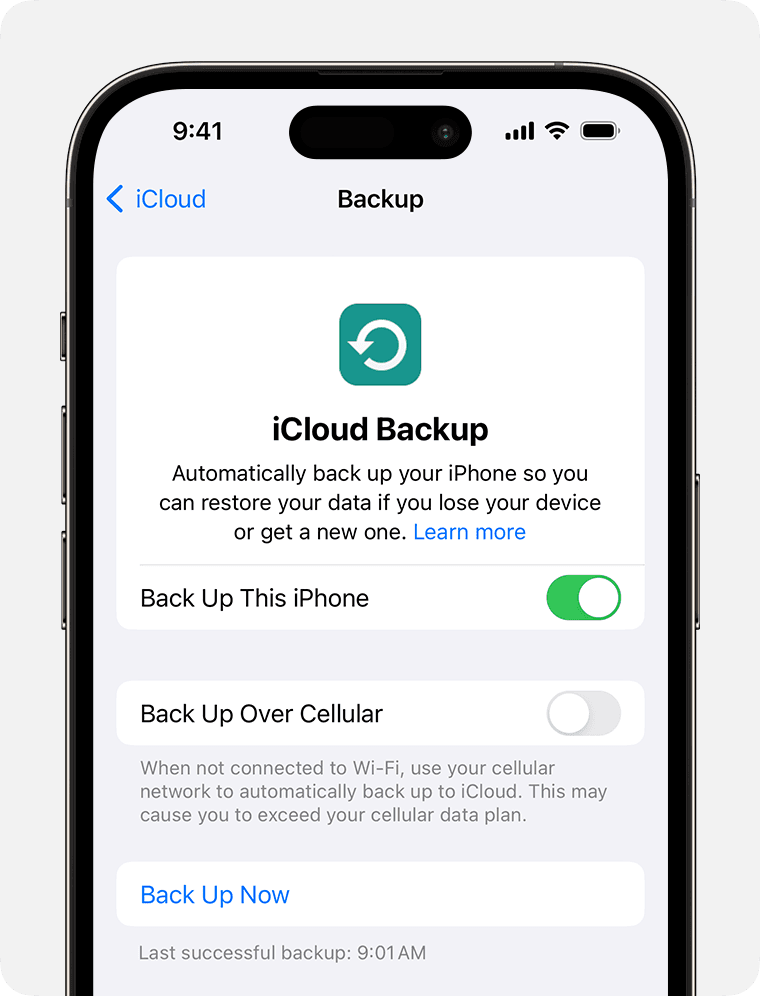
iCloud, Apple's cloud-based storage service, is another avenue to access iPhone messages. By leveraging iCloud backups, users can remotely view text messages without physically accessing the target device.
Features - what SMS data can be viewed
Steps
- Ensure the target iPhone is set up with iCloud backup enabled.
- Access the iCloud website or use another iOS device.
- Sign in with the Apple ID associated with the target iPhone.
- Navigate to "Settings," click on the Apple ID, and select "iCloud."
- Choose "Text Messages" to enable synchronization.
- Open the Messages app on the iCloud website to view text messages.
1.3 Forward text messages to your iPhone
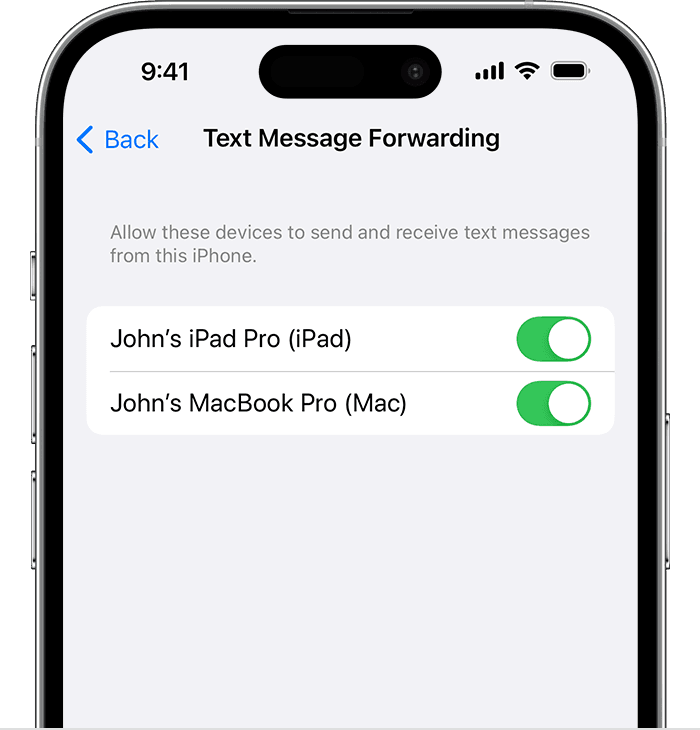
Forwarding text messages to your iPhone is a more direct method, involving the forwarding of messages from the target device to your own. This method is suitable for those who have permission to access the target device momentarily.
Features - what SMS data can be viewed
Steps
- Open the Messages app on the target iPhone.
- Locate the specific message or conversation to be forwarded.
- Tap and hold the desired message, then select "More."
- Choose the "Forward" option.
- Enter the recipient's contact information, which is your phone number.
- Send the forwarded message to your iPhone.
- Open the forwarded message on your iPhone to view the content.
These methods provide various options for users seeking to access someone else's iPhone messages, each with its own set of features, advantages, and considerations.
Part 2. How to read someone's text messages without having their phone
In the previous part, we introduced ways to view iPhone messages for free, but these methods require physical access to the target device, even with the help of other devices. Therefore, in this part, we will introduce ways to view someone's phone SMS without physically entering their device.
Using monitoring software is the best way to do monitoring without having to go into the target device. I'm sure you can find a lot of such software in the monitoring software market. But with so much software, how to choose? Don't worry, we have helped you pick the most functional and cost-effective one among many apps.
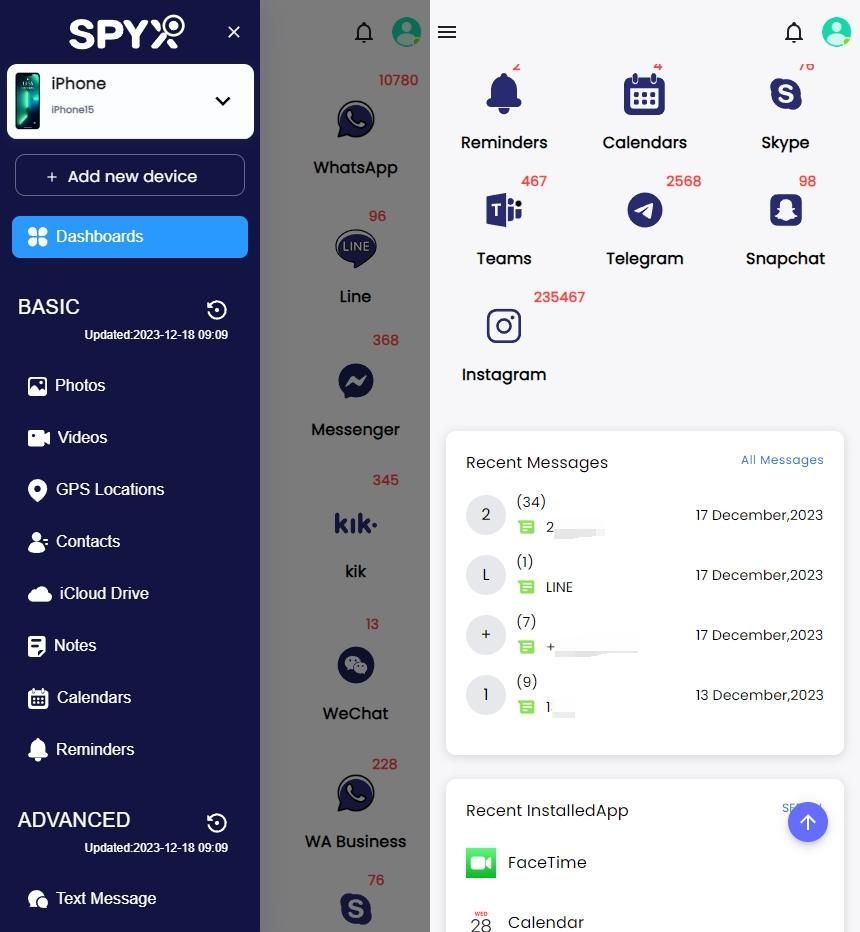
SpyX is an all-in-one cell phone monitoring software. It is well compatible with Android and iOS. In addition to real-time SMS monitoring, it can also remotely track data from 40+ apps: social media, photos, videos, calls, location and more.
Compared to other iPhone monitoring apps on the market, it has a super convenient connection: no jailbreak, no rooting, even no download, no physical access to the target device.
Moreover, it's also excellent in terms of customer service, offering 24/7 customer service to help users solve their problems the first time they need it.
Features - what SMS data can be viewed using SpyX
Steps
- Go to the SpyX official website to register an account.
- Bind the target device you want to monitor.
- Click Synchronize data in real time and start monitoring.
Part 3. Why Want to See Someone's Messages
Understanding the motivations behind wanting to view someone's messages is crucial. Whether it's concerned parents, employers, or individuals in relationships, this section categorizes the reasons.
3.1 Parents Concerned About Children’s Communication
In today's digitally connected world, parents face the challenge of ensuring their children's online safety. Monitoring text messages becomes a tool for parents to protect their kids from potential threats, cyberbullying, or inappropriate content.
By being aware of the content exchanged through text messages, parents can play an active role in creating a secure online environment for their children.
Parents monitoring children's phone text messages can prevent children from becoming Internet scammers and scammers, and can also be used to comprehend their emotional well-being and social interactions.
Beyond safeguarding against external threats, understanding the tone and context of conversations provides valuable insights into a child's mental state. This proactive approach allows parents to address any emotional challenges promptly, fostering open communication and support within the family.
3.2 Employers Keeping Tabs on Employees
In certain professional contexts, employers may have legitimate reasons to monitor employees' messages. This could be driven by concerns related to productivity, confidentiality, or ensuring that company resources are being used appropriately.
Exploring this avenue responsibly and within legal boundaries is crucial to maintaining a balance between workplace security and individual privacy. This section aims to shed light on the considerations that employers may have and the ethical implications of such monitoring practices.
Monitoring employee messages is not just about surveillance but can also be a strategic measure for enhancing communication within the workplace. Employers may use insights gained from message monitoring to identify communication gaps, streamline workflows, and foster a more collaborative and productive work environment.
This dual focus on security and communication improvement underscores the nuanced nature of employer monitoring practices.
3.3 Checking on Significant Others
In relationships, there may be instances where individuals feel the need to view each other's messages. Such as a wife who wants to secretly check her husband’s phone messages, while this might arise from concerns about trust or suspicion.
Discussing the boundaries of privacy within a relationship and understanding the implications of accessing someone else's messages is crucial for maintaining trust and healthy communication.
This part aims to provide insights into why couples may find themselves in such situations and encourage thoughtful reflection on the ethical implications involved.
This may be common, but the desire to check on significant others' messages can also stem from a genuine wish to strengthen emotional connections. Couples may engage in this practice to share in each other's experiences, fostering mutual understanding and empathy.
It becomes a way for partners to be more attuned to each other's lives, enriching their emotional connection and reinforcing the foundation of a trusting and supportive relationship.
Part 4. Conclusion
Navigating the complexities of accessing someone else's iPhone text messages necessitates an understanding of the diverse methods outlined in this guide. Each method discussed has its advantages and disadvantages, catering to varying needs. iTunes Backup offers accessibility and detailed insights but suits those with consistent access to the target device.
iCloud Backup provides remote accessibility and a comprehensive history but may face challenges in real-time information retrieval. Forwarding Text Messages offers focused, real-time access but requires physical access to the target device.
SpyX emerges is a recommended choice, providing an intuitive solution for SMS monitoring. Consider the pros and cons, ensuring usage aligns with legal and ethical boundaries. Ultimately, the your choice depends on individual needs, permissions, and ethical considerations.
Understanding the reasons behind access is crucial, with users urged to prioritize trust, privacy, and legality. In the ever-evolving tech landscape, responsible and ethical usage is the most important.
Part 5. FAQs
Can someone forward your text messages without you knowing?
Yes, someone can secretly forward your text messages using the third-party monitoring app. It is hidden on the target device and it can forward your SMS automatically to his/her device.
Can I recover deleted text messages?
If it's an iPhone phone, you can recover it by looking at the recently deleted text messages, or you can use iCloud backup or iTunes backup method to recover it. If it's an Android phone, you can try to find it in the phone's built-in backup or Google cloud.
How can I get my boyfriend's text messages sent to my iPhone?
If your boyfriend is also using an iPhone, then you can access his Apple ID, sign in to his iCloud account and then sync the data to your phone. If your boyfriend is using an Android phone, then you can use the third-party tool SpyX, which is compatible with both Android and iOS, and SpyX is applicable no matter what type of device the user is using.
How do I look up text messages on my iPhone?
You can search through your iPhone's text messages to find the ones you want to see.
- In the Messages app, open the conversation list.
- Swipe down from the list of conversations in the Messages app to display the search bar.
- Enter what you're looking for, then tap Search.
More Articles Like This
SPYX'S SOFTWARE INTENDED FOR LEGAL USE ONLY. You are required to notify users of the device that they are being monitored. Failure to do so is likely to result in violation of applicable law and may result in severe monetary and criminal penalties ...







Disclaimer: SPYX'S SOFTWARE INTENDED FOR LEGAL USE ONLY. You are required to notify users of the device that they are being monitored. Failure to do so is likely to result .....