How to log into someone’s Gmail without password

Last updated:apr 28, 2024
Table of content
In today's interconnected world, there are numerous reasons why one might find themselves in a situation where they feel the need to access someone's Gmail account.
For concerned parents, monitoring their child's online activity is paramount in ensuring their safety and well-being in the digital realm.
Similarly, employers may need to safeguard company interests by monitoring employee communications and detecting potential security threats.
In cases of suspected infidelity or dishonesty, individuals may seek to uncover evidence hidden within email correspondences.
Additionally, retrieving access to a deceased loved one's Gmail account can be necessary for settling estate matters or retrieving sentimental information.
Whether for personal protection, professional security, or legal obligations, the ability to spy on and log into someone's Gmail can provide crucial insights and peace of mind in an increasingly digitized society.
Part 1. Can you get into someone’s Gmail
Yes, it's possible to gain access to someone's Gmail account through various methods, albeit with certain conditions and considerations.
Techniques such as exploiting browser cookies, utilizing keyloggers, or employing monitoring apps offer avenues for accessing Gmail accounts without passwords.
It's essential to note the legality and ethics surrounding such actions. While accessing one's account or with explicit consent is permissible, unauthorized access may breach privacy laws and terms of service agreements.
Understanding the implications and potential consequences is crucial before attempting to gain entry into someone else's Gmail account. Below, we'll discuss three effective methods to log into someone's Gmail without their password.
Part 2. How to log into someone’s Gmail: 3 ways
This part will introduce 3 ways to log in to someone's Gmail. From browser cookies to keylogger to monitoring apps, there is always a method that suits you.
Method 1. Log into Gmail using browser’s cookie
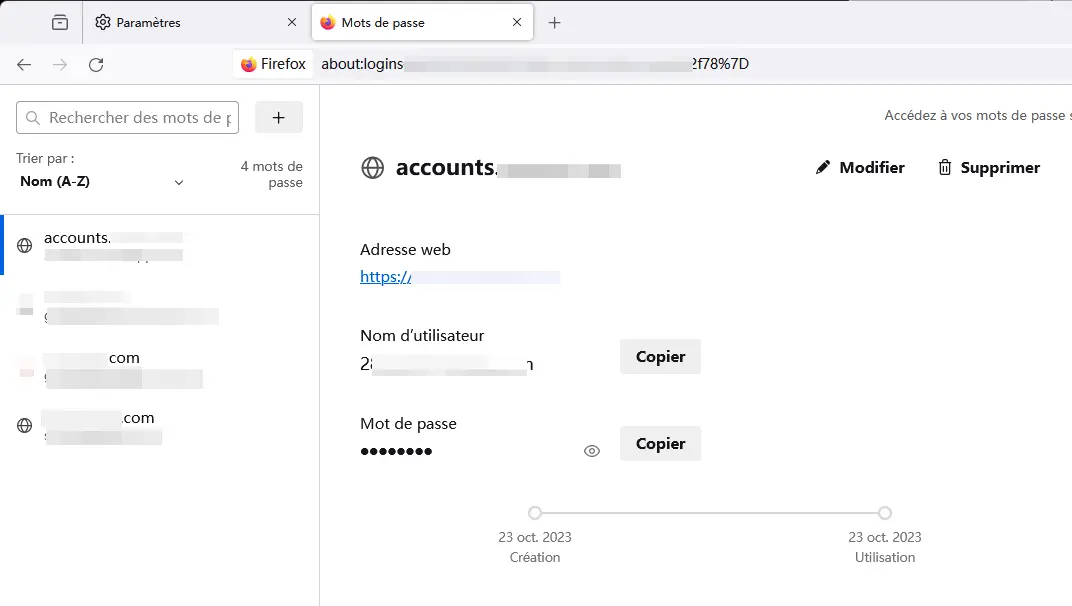
If someone's Gmail account has been previously logged in on your mobile phone or computer browser, and the password is saved, you can access it through the browser's cookie. Here's how:
Step 1. Open the web browser used by target person on their computer.
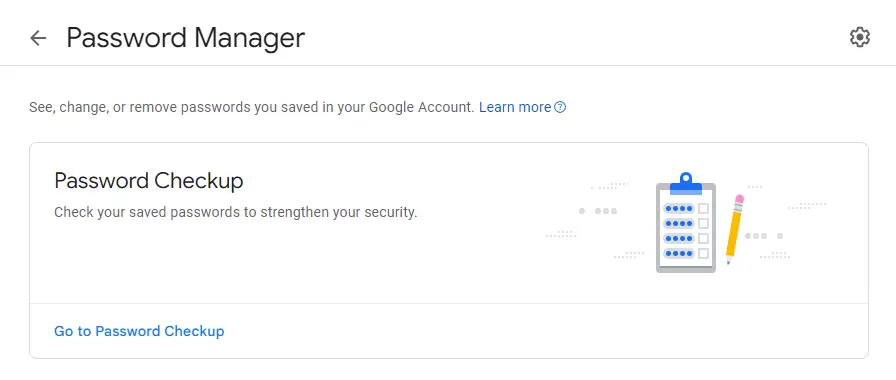
Step 2. Access the password manager:
For Internet Explorer: Click the Gear or Tools menu, select "Internet Options," then navigate to the "Content" tab and click "Settings" in the AutoComplete section. Choose "Manage Passwords."
For Chrome: Click the Chrome Menu button, select "Settings," then "Show advanced settings," and scroll to "Passwords and forms." Click "Manage passwords."
For Firefox: Click the Firefox Menu button, select "Options," go to the "Security" tab, and click "Saved Passwords."
For Safari: Click the Safari menu, select "Preferences," then click the "Passwords" tab.
Step 3. Locate the password for the target's Google account by searching for "Google" in the password manager.
Step 4. Display the password, write it down, and close the password manager to cover your tracks.
Step 5. Test the password from another computer. If two-factor authentication is enabled, you'll need the verification code sent to their mobile device.
Method 2. Access someone’s Gmail with Keylogger
Installing a keylogger software on the target device, typically a computer, is another method to gain access to someone's Gmail account.
A keylogger is a type of surveillance software designed to record every keystroke made on the device where it is installed.
This means that every password, message, or search entered by the user is captured and logged by the keylogger, including Gmail passwords.
Step 1. Install keylogger: Install keylogger software on the target device, typically a computer. We provide different guidance for different types of devices:keylogger an Android phone, keylogger for iPhone.
Step 2. Record keystrokes: The keylogger silently records every keystroke made on the device, including Gmail login credentials.
Step 3. Retrieve password: Review the keylogger log to retrieve the target's Gmail password.
Step 4. Access Gmail account: Use the obtained password to gain unauthorized access to the target's Gmail account.
It's important to note that using keyloggers to access someone's Gmail account without their consent is unethical and potentially illegal. Always consider the legal and ethical implications before resorting to such methods.
Method 3. Get into someone's Gmail by monitoring app
SpyX offers a convenient solution to access someone’s Gmail without needing their password, eliminating the need to download and install an app on the target device.
As long as the target device is bound, you can directly view all records of the target user on Gmail without logging in to their Gmail account.
How to get into someone’s Gmail without a password
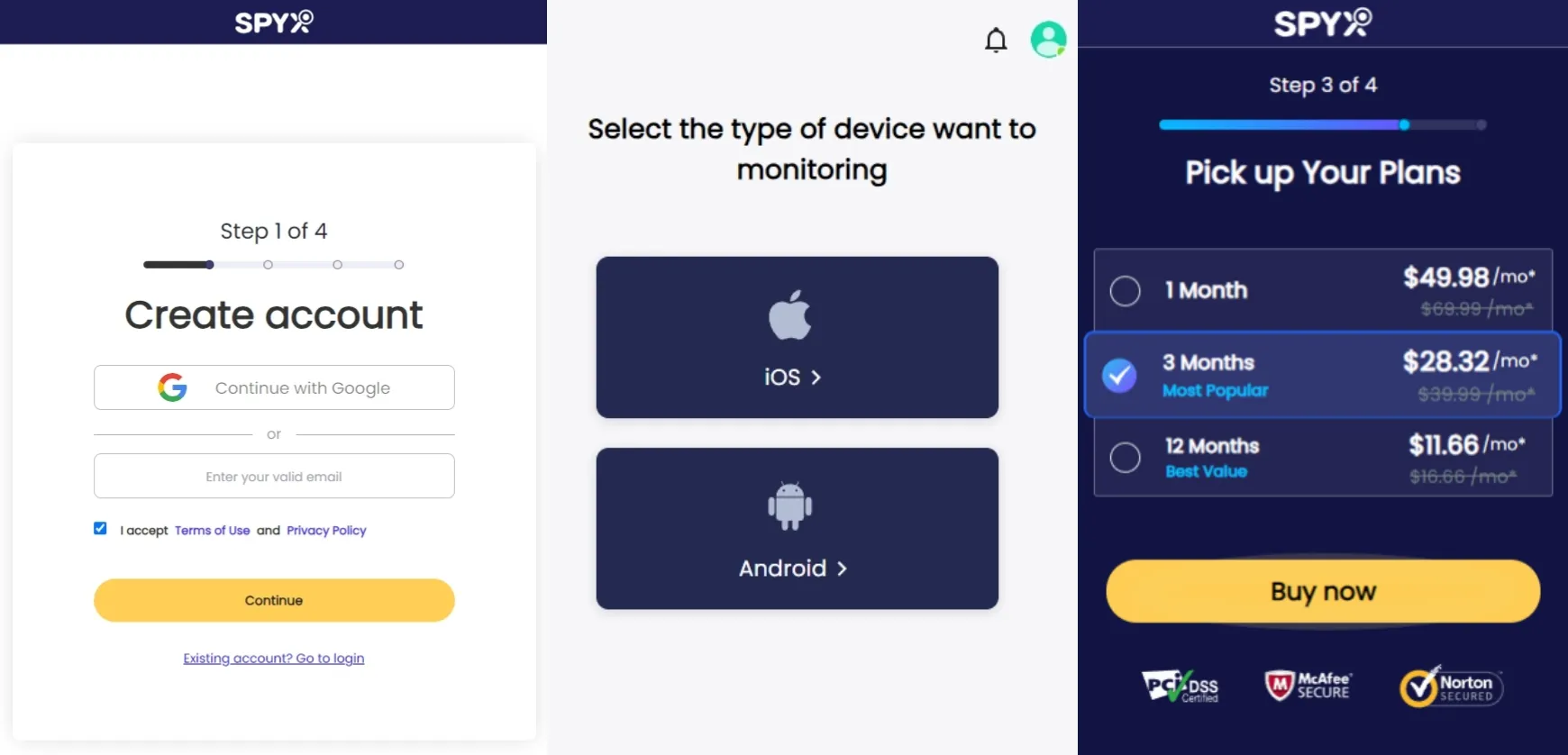
Step 1. Create an account with a valid email on SpyX.
Step 2. Select the type of device you want to bind (Android or iOS) based on the type of phone used by the target person.
Step 3. Choose the plan that's right for you, then follow the guidance to bind the target devices.
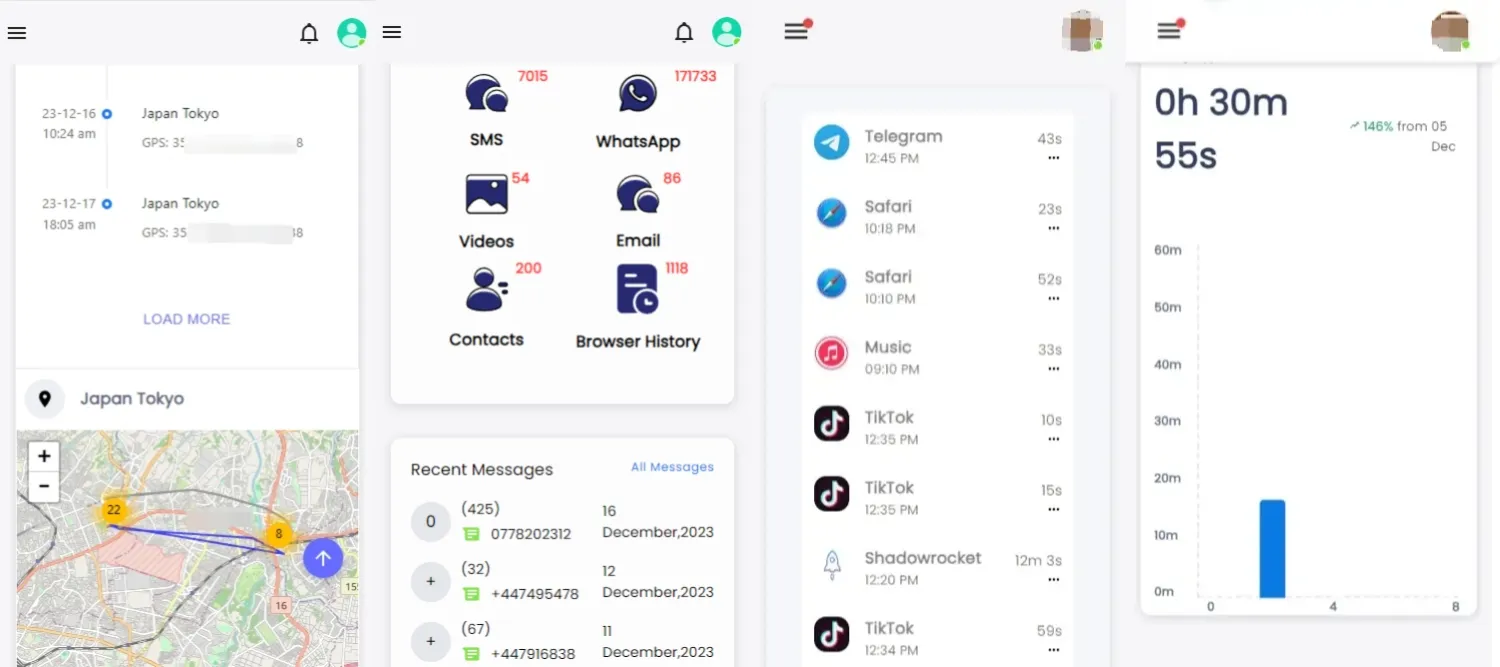
Step 4. Enter SpyX, click on the Gmail function, and you can read all received and sent emails in someone's Gmail account, including time, date, and name.
SpyX's advanced monitoring features
In addition to Gmail monitoring, SpyX boasts a wide range of monitoring capabilities, making it a powerful tool for keeping track of a target device's activity:
SMS and call logs: Monitor incoming and outgoing text messages and phone calls, including timestamps and contact details.
Social media apps: Keep tabs on activity across various social media platforms, including WhatsApp, Instagram, and Facebook, among others.
GPS positioning: Track the location of the target device in real-time using GPS positioning, ideal for monitoring the device's whereabouts.
Geofencing: Set up virtual boundaries and receive alerts when the target device enters or exits predefined locations, providing added security and control.
More features: Such as viewing photos & videos, notes, calendar, app installation and usage, and more.
With its comprehensive suite of features, SpyX offers unparalleled insight into a target device's activity, making it an invaluable tool for monitoring and surveillance purposes.
Part 3. Is it illegal to log into someone's Gmail without their permission
In many jurisdictions, accessing someone's Gmail account without their permission is considered illegal and may violate privacy laws and regulations.
Unauthorized access to another person's online accounts, including Gmail, is typically viewed as a violation of privacy rights and may lead to severe legal consequences, including criminal charges and civil lawsuits.
Furthermore, platforms like Gmail have strict terms of service agreements that prohibit unauthorized access to accounts.
Violating these terms can result in the suspension or termination of the account and may lead to legal action by the service provider.
It's essential to respect individuals' privacy rights and adhere to legal and ethical standards when accessing online accounts.
Always obtain proper authorization before accessing someone's Gmail account, and consider alternative methods of communication or resolution to avoid potential legal issues.
Part 4. FAQs
Is it possible to access someone's Gmail without their knowledge?
Yes, it's possible to access someone's Gmail without their knowledge through methods like exploiting browser cookies, using keyloggers, or employing monitoring apps.
What are the legal implications of accessing someone's Gmail account without permission?
The legal implications of accessing someone's Gmail without permission can vary depending on jurisdiction, but generally, unauthorized access violates privacy laws and terms of service agreements, potentially leading to legal consequences.
Are there any ethical considerations to keep in mind when attempting to log into someone's Gmail?
Ethical considerations when attempting to log into someone's Gmail include respecting privacy, obtaining consent, and considering the potential impact on the individual's trust and security.
How can I ensure the security of my own Gmail account to prevent unauthorized access?
To ensure the security of your own Gmail account and prevent unauthorized access, use strong, unique passwords, enable two-factor authentication, regularly review account activity, and avoid sharing login credentials.
Part 5. Final summary
In conclusion, learning how to log into someone's Gmail can be a valuable tool in various scenarios, from parental monitoring to ensuring company security.
By exploring methods such as browser cookies, keyloggers, and monitoring apps like SpyX, individuals can gain access to Gmail accounts discreetly and efficiently.
However, it's crucial to approach these methods ethically and legally, considering the potential consequences of unauthorized access.
With proper discretion and adherence to ethical standards, these methods can provide valuable insights while respecting privacy and legal boundaries.
More Articles Like This