How to monitor phone calls [3 proven ways]

Last updated:jul 16, 2024
Table of content
With everything being connected these days, people argue a lot about how safe phone calls are. You may "monitor a phone by calling" or even "monitor someone's phone calls secretly." A lot of people want to know this.
There are also a lot of online myths about how easy it is to get to phone data.
In this article, we will talk about these issues and help you secretly monitor someone's phone calls.
Part 1. Is it possible to monitor someone's phone calls
Despite the difficulties involved, it is possible to achieve this with the advancement of technology. The following section will present three effective methods for monitoring into someone's cell phone calls.
Part 2. How to monitor someone's phone calls [3 proven ways]
Way 1. Using SpyX
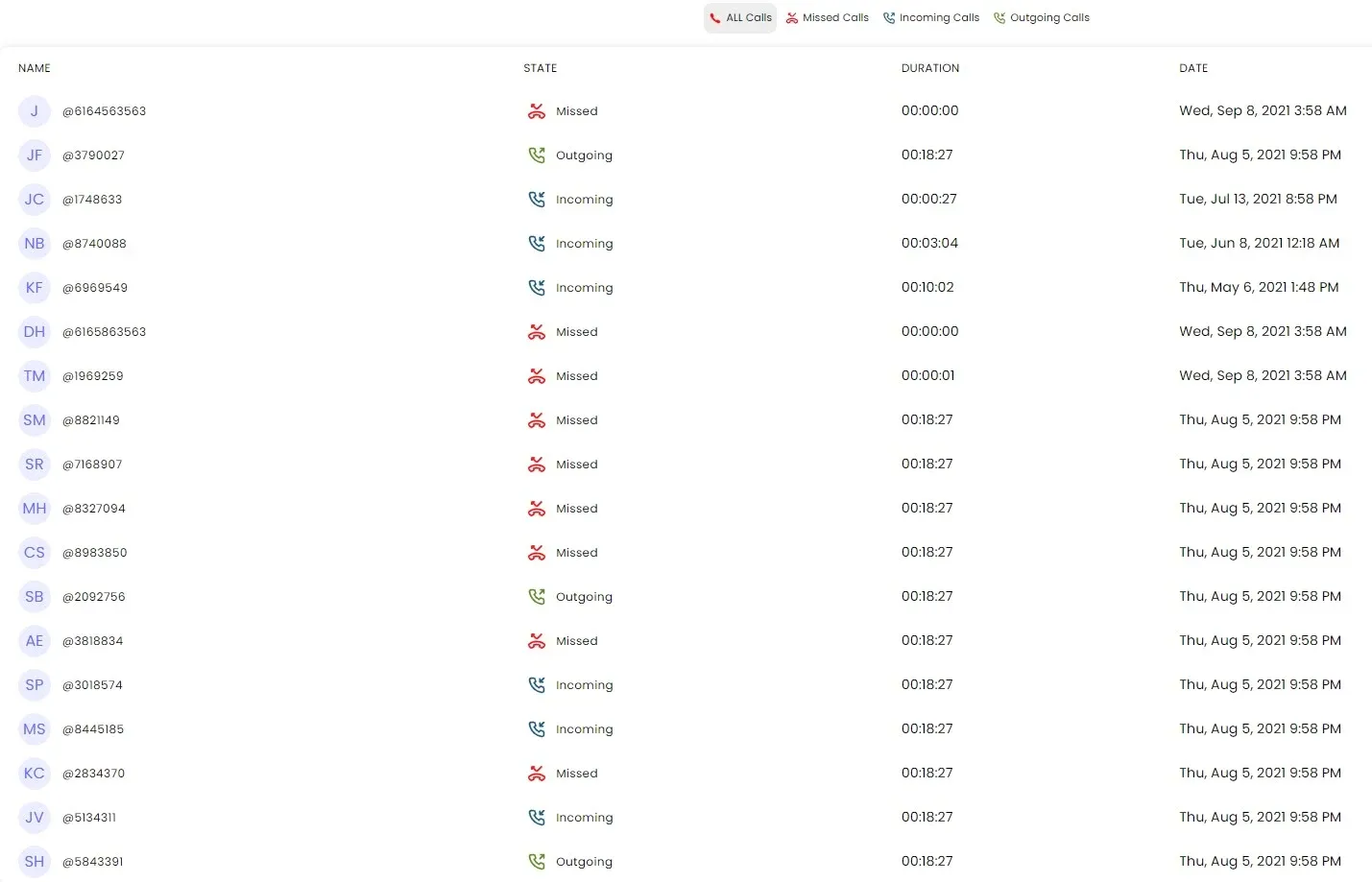
SpyX is a great program for listening to and recording phone talks. People can listen to live calls and see full call logs that show the time, length, and numbers that were called or received.
Strengths of SpyX in monitoring phone calls:
? Spy on incoming and outgoing calls.
With SpyX, you can easily to spy on all phone call history including incoming and outcoming calls.
? Track missed or canceled calls.
Even calls that have been missed or canceled can be tracked remotely.
? Check call details.
With SpyX, you can see full call logs that show the time, length, and numbers that were called or received.
What other phone activities can SpyX monitor:
SpyX can do more than just listen in on conversations. Not only that, but it can also keep track of web data, text messages, GPS location, social media use, and more.
This table presents a comprehensive overview of the phone activities that SpyX is capable of remotely monitoring. It should be noted that slight variations in the data that can be monitored may occur depending on whether the target phone is an Android or iPhone.
You can scroll left and right on this table to view more information.
How to use SpyX to monitor someone's phone calls:
Step 1. Sign up for a SpyX account that works for you.
Step 2. Select the type of device you want to monitor (whether iOS or Android).
Step 3. For an iOS device, fill in the Apple ID and password of the iOS device to be monitored. For Android device , there are two connection options. One is to install the SpyX software on the target phone directly and follow the on-screen prompts to complete the connection. The other option is to fill in the Google account and password of the target device. You can choose either of these two options.
Step 4. Start monitor phone activities remotely.
Way 2. Using Google Drive [Android]
Setting up Google Drive will automatically back up all of your data from your Android phone. This includes call logs.
Steps to use Google Drive for accessing call history:
Step 1. Ensure the target device is set up to back up call logs to Google Drive (found under "Settings" > "System" > "Backup").
Step 2. Gain access to the Google account credentials associated with the target device.
Step 3. Sign in to Google Drive with these credentials.
Step 4. Locate and download the backup file containing the call logs.
Step 5. You can view these call logs using a suitable database viewer.
Way 3. Using iCloud backup [iPhone]
Apple has a service called iCloud Backup that backs up your info from your iOS devices right away to iCloud. Call logs are part of this.
Steps to use iCloud backup for accessing call history:
Step 1. Confirm that the target iPhone is configured to back up to iCloud (settings are under "Settings" > [user name] > "iCloud" > "iCloud Backup").
Step 2. Obtain the iCloud credentials of the associated account.
Step 3. Log in to the iCloud account at icloud.com or use forensic tools to access the backup directly.
Step 4. Download the backup files from iCloud.
Step 5. Extract the call history from the backup using third-party tools designed for data extraction.
Part 3. Beware of common scams of monitoring phone
Many fake stories spread about how easy it is to monitor phones these days, which causes many people to fall for scams. A lot of people have false ideas about monitoring phones. We first thought that if you call, text, or have someone's phone number, you could get into their phone.
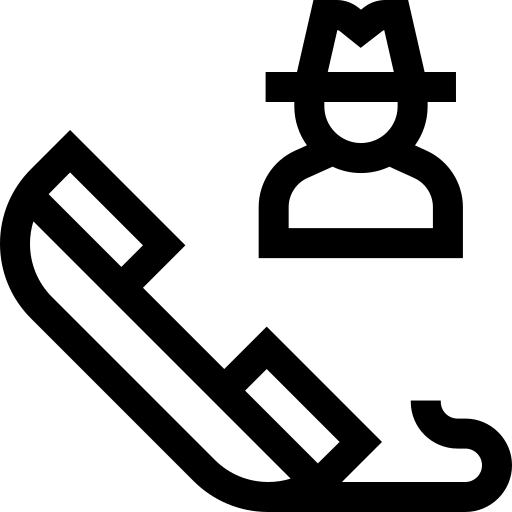
(1) Monitor someone's phone just by calling
A lot of people fall for the scam that says calling someone will let you use their phone. People likely believe this myth because they don't know how cell phone networks and security work. Smartphones today have high-tech safety features that keep people who shouldn't be there from getting in.
How the scam works:
Scammers may claim that by using special software or by performing a unique sequence of call actions, they can install spyware on the target's device. They often ask for money to perform this service or attempt to get the victim to engage in behaviours that compromise their security.
Why it doesn’t work:
- Technical safeguards: Mobile operating systems like Android and iOS have strict permissions and sandboxing policies that isolate applications and their data from the rest of the system.
- Carrier protections: Mobile carriers have systems in place to detect and prevent unusual network activities, which would include any malicious actions attempted through a voice call.
Real risks involved:
Vishing is a complicated way for scammers to get people to give up personal information that could be used for fraud or identity theft. Calling a phone doesn't monitor it, but scammers do use voice phishing to do it.
(2) Monitor someone's phone just by texting
A different common scam says that you can take over someone else's phone by sending them a text message. Most of the time, these are messages that try to get people to download harmful software or visit websites that might be dangerous.
How the scam works:
Con artists might text you links to sketchy websites or directions on how to get apps that don't work. It's possible that the people in these texts are scared and feel like they need to move quickly to get something for free or give out their information.
Why it doesn’t work:
- Malware usually starts when a user does something, like opening an app, giving permission, or clicking on a link.
- Better safety: tools are always getting updated with fixes for known security holes. For this reason, you should keep an eye out for software that could be harmful and make changes that make things safer.
Real risks involved:
If people do what the texts say, SMS phishing, also called "smishing," is a real threat. People may be able to run software, get personal information out, or make sales without permission.
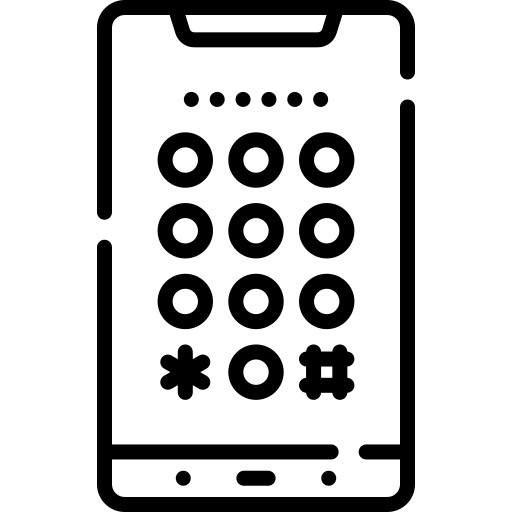
(3) Monitor someone's phone just by phone number
You can't monitor someone's phone just because you know their number. This scam is often spread in sketchy online groups and sites that say they can monitor your computer.
How the scam works:
Service scammers say they can use someone's phone number to monitor into their phone for a fee. Most of the time, this means making up long stories about holes in the network or using carrier bugs to your advantage.
Why it doesn’t work:
- There isn't a straight link: Just because you can't directly access the hardware or software of someone else's device doesn't mean you have their phone number.
- Telecommunications security: Carriers protect their networks and customer data with strong security measures. One thing they do to do this is to watch out for strange behaviour.
Real risks involved:
Finance is the biggest risk here. People give con artists money thinking they can get into their phones, but they lose it all.
Part 4. FAQs about monitoring someone's phone calls
A lot of the time, people listen in on other people's talks because they are curious, afraid for their safety, or want to learn more about technology. People often ask these three questions about monitoring phone calls. Here are the full answers to help clear things up.
Q1. How to get into someone's phone calls for free?
If your target device is an Android, you can use Google Drive backup to help you access someone else's call history. If your target device is an iPhone, you can use Apple's built-in iCloud backup. Please note that both methods require you to know the target device's Google account/iCloud account and password, so there's a risk of being discovered!
Q2. What are the signs that my phone calls might be monitored?
Several signs might suggest your phone is compromised, though none conclusively indicate a phone call monitor:
- There shouldn't be any music or other sounds that don't belong when people are talking.
- It gets too hot or dies too quickly.
- Going back to the beginning or going slowly for no reason.
- It's possible that you're not making the most of your data or adding useful apps to your phone.
If you see any of these signs, you should check your computer with protection software and, if needed, get help from a professional.
Q3. How can I protect my phone calls from being monitored?
To protect your phone calls and overall phone security, consider the following measures:
- Updating your OS and apps will fix bugs that have already been found.
- Use safe apps like Signal or WhatsApp that offer end-to-end protection to talk and write.
- When you call or text someone who isn't secured, don't give out private information.
- Watch out for emails you didn't ask for and don't click on links you don't understand.
Part 5. Conclusion
This article introduces three methods to help you monitor someone's phone calls: Google Drive, iCloud backup, and SpyX. You can choose the most suitable method according to your needs. It also exposes some common online scams claiming that a certain method can easily monitor someone's phone. Hope it helps you!
More Articles Like This