10 best monitoring apps for iPhone | Ultimate review of 2025

Last updated:12月 25, 2024
Table of content
What is the best monitoring app for iPhone? After reading so many reviews, it's still hard to tell which iPhone monitoring app best suits your needs? It seems like your iPhone is being tracked, what are some signs that your iPhone is being tracked? If it's really being tracked, what should you do? If you are troubled by these questions, congratulations, you have come to the right place! This article will answer all your questions about iPhone monitoring!
Part 1. Quick summary of the best monitoring app for iPhone
Here is a detailed table comparing the top-rated monitoring apps for iPhones, helping you choose the right one easily.
【Note: You can scroll left and right on this table for more information.】
| Monitoring app | Top 3 features | Free trial or demo | Supported Systems |
| SpyX |
| Free demo. | Supports all iOS systems. |
| Msafely |
| Free demo. | Supports all iOS systems. |
| Kidsguard Pro |
| Free demo. | Supports iOS 12-14. |
| mSpy |
| Free demo. | Supports all iOS systems. |
| Eyezy |
| Free demo. | Supports all iOS systems. |
| Webwatcher |
| No free trail or demo. | Supports iOS 6.0 or later. |
| Spylix |
| Free demo. | Supports all iOS systems. |
| Find My iPhone |
| Free | Supports all iOS systems. |
| Find My Friends |
| Free | Supports all iOS systems. |
| Google Maps |
| Free | Supports all iOS systems. |
Next, I will conduct detailed reviews of each iPhone monitoring software to help you gain a deeper understanding of them.
Part 2. Best iPhone monitoring app tested-Review
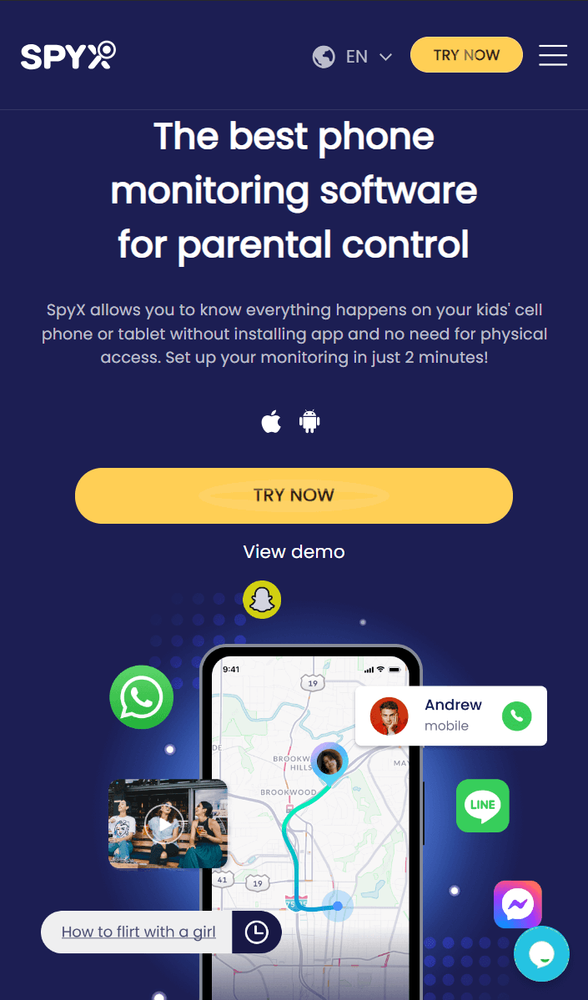
1. SpyX
As a hidden iPhone monitoring app, SpyX can help you remotely track someone's iPhone without installing any app. Because it uses the iCloud connection solution, you don't need to have physical access to the target iPhone to install software. You just need to register a free account with your email and complete two-factor authentication according to the page instructions. By the time he finishes his coffee, you will have completed all the connecting processes, and you don't have to worry about being detected.
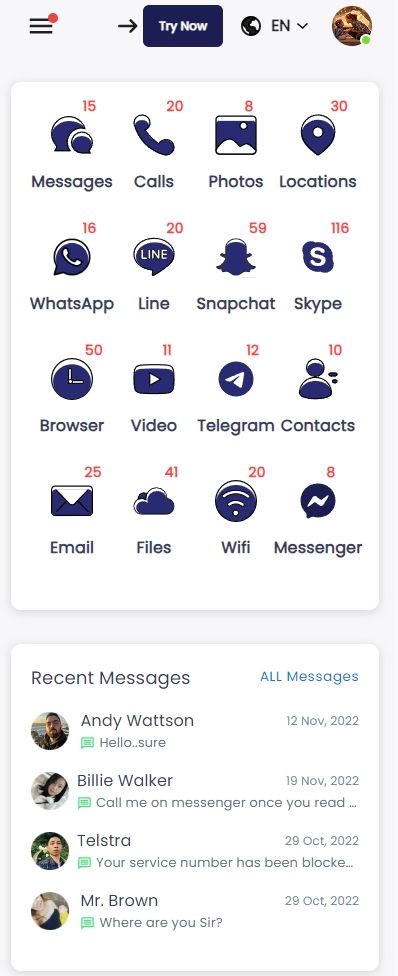
SpyX has the most comprehensive monitoring features. It can track over 30 types of data, helping you monitor the target iPhone's SMS, call logs, location, browsing history, installed apps, and more in real-time.
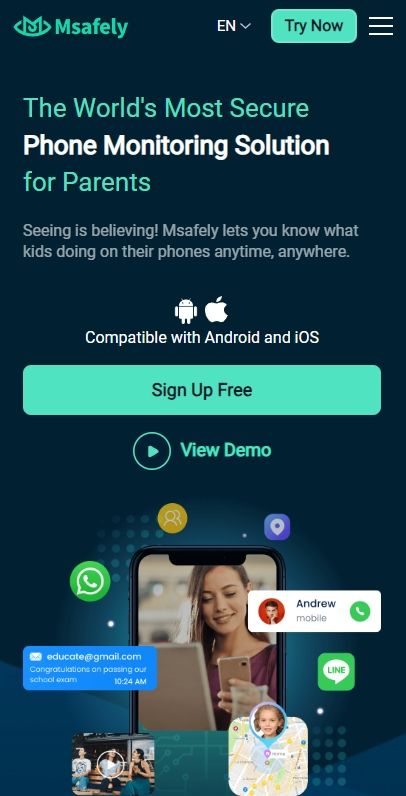
2. Msafely
Msafely is one of the best iPhone monitoring apps available, utilizing the iCloud connection solution. With Msafely, you can remotely track a target phone without the need to install any software. You can track over 20 types of data in real-time, including SMS, location, photos, emails, and more, all without jailbreaking.
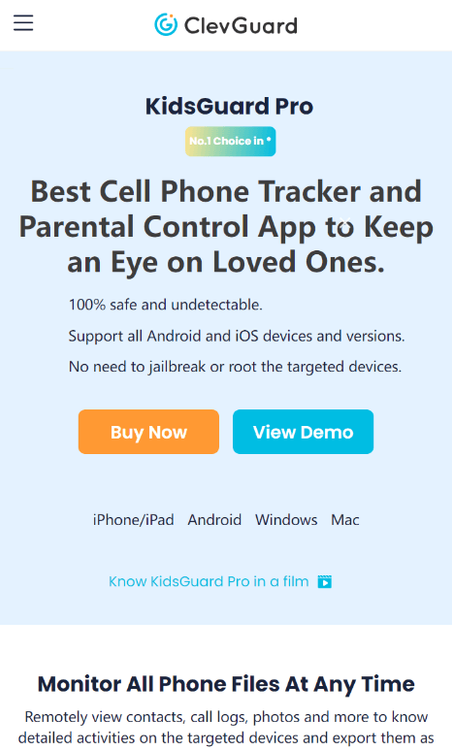
3. Kidsguard Pro
Kidsguard Pro is a professional iPhone monitoring app. It supports 3 connection methods: iCloud, USB and jailbreak. While the USB method can greatly increase the likelihood of successful connection, it requires physical access to the target iPhone, which can be challenging. As for the jailbreak method, it's too technically challenging and requires advanced computer programming skills. I don't recommend using it!
Kidsguard Pro offers powerful monitoring capabilities, allowing you to remotely track SMS, contacts, location, WhatsApp, and more.
It's important to note that different connection solutions allow for different types of data monitoring. Please refer to the table below for details on each connection solution.
Further reading: Ultimate review of Kidsguard Pro.
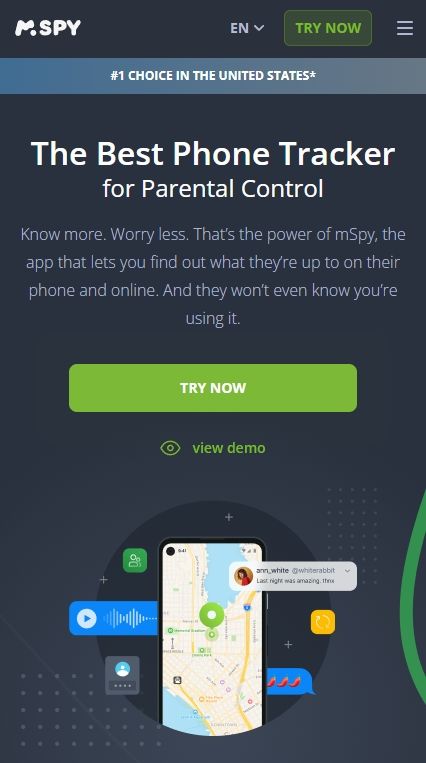
4. mSpy
mSpy is a very famous iPhone monitoring software. It can help you track activities on someone else's phone without their knowledge. The data from the target device is uploaded to mSpy's dashboard in real-time, allowing you to easily achieve your remote monitoring goals.
mSpy currently supports three connection solutions: iCloud, USB, and jailbreak. You can choose the appropriate connection solution based on the data you want to monitor.
Further reading: In-depth review of mSpy.
5. Eyezy
Eyezy is another iPhone monitoring software that supports three connection solutions. It is popular in the parental monitoring field, helping many parents remotely monitor their children's activities on their phones to better protect their online safety. Let's take a look at its monitoring features!
Further reading: Latest reviews of Eyezy.
6. Webwatcher
Webwatcher is a well-established monitoring app for iPhones that allows you to remotely track SMS, photos, videos, installed apps, and more. It enables you to view activities on someone else's phone in real-time without being detected. However, it only supports one connection solution, which is the USB.
Further reading: In-depth review of Webwatcher.
7. Spylix
Spylix, as an iPhone monitoring app, currently only supports the iCloud connection solution. This means that you do not need to install any software on the target iPhone, which greatly reduces the difficulty of connection. However, compared to the other 6 iPhone monitoring apps mentioned, its hakcing features are relatively weak.
Further reading: Comprehensive review of Spylix.
Part 3. Free iPhone monitoring apps-Apple's built-in location monitoring software
There are many built-in location monitoring apps offered by Apple that allow users to track and locate their iPhones remotely. Let's look at a few methods to track an iPhone through its built-in location-monitoring software.
Method 1. Monitoring an iPhone via "Find My iPhone".
If you’re an iPhone user, you’re probably familiar with the feature “Find My iPhone”, which is a built-in feature in all Apple devices. While this feature can help you track your iPhone, this is also one of the easiest ways of monitoring someone’s iPhone and gaining access to their digital world. Let’s see how you can use “Find My iPhone” to monitor someone’s activities.
Step 1. You will need to get the Apple ID Credentials of the target person.
If you want this method to work, you will need to get your hands on the Apple ID credentials such as the Apple ID email and password of the target person, and this job is solely in your hands.
Step 2. Use a computer or an iPhone to log in to “Find My iPhone”.
With the help of a computer or another iPhone, log in to “Find My iPhone” using the Apple ID credentials you have acquired through your own skill set.
Step 3. Start monitoring.
Once you log in to “Find My iPhone”, you will be able to see the location of your target person and see what they are doing at that precise moment. In this way, you can easily gain access to someone’s iPhone and search for whatever you’re looking for.
Method 2. Monitoring an iPhone via "Find My Friends".
Apple users flex about a lot of things, and one such thing is another built-in feature known as “Find My Friends”. While this method can be used to track the location of your target person, it can also be used as a getaway to gain entry into someone’s iPhone. Let’s see how “Find My Friends” works, and how can you use this method.
Step 1. Begin by Finding the “Find My Friends” on your personal iPhone.
The first step begins by finding the “Find My Friends” app on your iPhone, and once you find it, launch the app and then tap on “Add”, and then “+”.
Step 2. Fill the necessary information.
Once you go through the primary steps, Apple will ask you to put in the contact information of the person you want to monitor, and then tap on “Send”. Apple will automatically send a notification to your respective person, asking them to share their location with you.
Step 3. Start monitoring.
Once they grant you access, you will easily find your way into their digital itinerary, and you can safely see what places they are visiting to keep an eye on them.
Method 3. Monitoring an iPhone via "Google Maps".
We all personally love Google, and even more when it itself provides entire information whenever you’re filling out a form. Similarly, Google also saves your location, which can be used to gain entry into someone’s iPhone. However, for this method, there is one thing you need to make sure of Turn on the internet connection and enable Location on your target iPhone.
Step 1. Go to Google Maps.
In the first step, launch the official website of Google Maps with the help of a browser.
Step 2. Log into the Google Account.
Here, you need to log in to that Google account, which is associated with your target person. Once you fill in the information and sign in, a dashboard will appear in front of you, click on the dash icon, and then “Menu”.
Step 3. Start monitoring.
Once you click on Menu, you need to navigate your way through “Your Timeline”, which will provide you with a list of the places your target person has visited in the past days, weeks, or even months.
Part 4. Key factors to consider when choosing the best iPhone monitoring app
Take the following things into account while selecting the top iPhone monitoring app:
- Device Compatibility:
Check if the monitoring application is compatible with the iOS version and iPhone model.
- Tracking Features:
Go through the app's real tracking features. This includes GPS, email, social media, internet browsing, calls, and text messages, and so on.
- Dependability and Secrecy:
Select a reliable software program by viewing its accuracy, dependability, and data integrity. It should have a good performance.
- User-Friendliness:
If a choice should be made, go for the app with a simple interface. This must also guarantee ease when navigating.
- Customer Support and Reputation:
Customer service is also important. Pick an iPhone monitoring app from a dependable source that has quick customer support that happens constantly.
Taking all the above factors into consideration, we have ranked the 10 monitoring methods as follows:
Part 5. How to use the best iPhone monitoring app to track an iPhone without them knowing
SpyX as the best iPhone monitoring app, only need 3 steps, you can complete the connection.
Step 1. Sign up for a free account with your email.
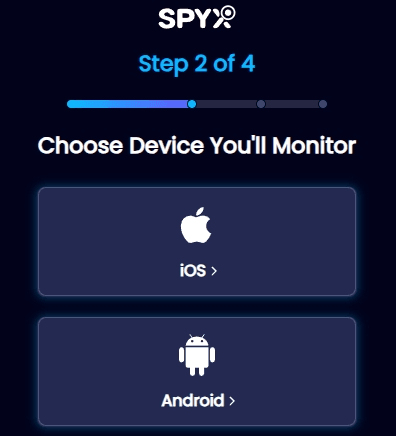
Step 2. Choose the device you want to track.
Select"Android" for an Android phone and "iOS" for monitoring an iPhone.
Step 3. Start monitoring.
Now you can see SMS, call logs, GPS location, WhatsApp, Instagram, etc remotely.
Part 6. Bonus tips for how to protect your iPhone from monitoring
6.1. Signs that someone is monitoring your iPhone remotely
The following are some warning signs. They indicate that someone is trying to track into your iPhone.
- Unexpected password changes:
Logins are remote-tracked if you find out that your accounts are locked or changed. You will realize that passwords are tracked with your connectivity rather than your fault.
- Odd notifications:
Odd notifications can be emails, texts, or notifications that pop up on your iPhone. You can easily suspect a tracker may have granted them such access.
- Slow performance or frequent crashes:
If your iPhone is infected, it can result in sluggish processes, freezes, and crashes.
- Unusual data usage or battery drain:
You will also notice battery draining at a faster rate, unwanted data usage, and a hotter phone than normal.
- Activity while in sleep mode:
Suspicious activity can be during sleep mode. It could be a sign that an outsider has remote access to your gadget.
6.2. Ways to protect your iPhone from monitoring
The digital era is more and more reliant on our iPhones to be like extra parts of us. That's why we must safeguard them against security risks.
- Please don't ever jailbreak your device.
Jailbreaking your iPhone may lead to the availability of many applications and software. However, it also risks the warranty and leaves the device prone to spyware/viruses.
- Update iOS frequently.
You should update your device's iOS to the latest version on a regular basis. This minimizes the chances of the device being exploited by trackers.
- Exercise caution while sending emails and messages.
Be aware of the threats brought by emails or messages from unfamiliar persons. It is necessary to respond wisely. By doing so, one can prevent malware or phishing scams that can threaten your device's security.
- Frequently changing your Apple ID password.
Updating the Apple ID password regularly protects against unauthorised access. This safeguards your personal information on the device and iCloud.
- Utilize safe Wi-Fi networks.
In public places, people should not rely on insecure Wi-Fi networks, as they cause serious security threats.
- Beware of using public charging stations.
Be alert when at public charging stations since trackers could be able to steal your phone data through them.
- Enable Two-Factor Authentication on your Apple ID.
Use the two-factor authentication to prevent uninviting access to your device. Only trusted devices can access your data.
- Increase the strength of your smartphone passcode.
Use a longer and unique passcode that combines letters and numbers. It would reinforce the security of your iPhone.
- Switches Siri off from the Lock Screen.
The chances of security breaches can be reduced by simply turning off the Siri feature. This prevents unwanted access to iPhone functions.
- Active the "erase data" function.
Make the "Erase Data" option work to make sure that no one would access your data mistakenly.
- Encrypting all communication from start to finish.
This can be achieved by using end-to-end encrypted services for your communication. This prevents trackers from listening to or reading your messages.
6.3. What should you do if someone has tracked your iPhone
You must take urgent action if you suspect that your device has already been tampered with.
- Use security software to conduct a scan:
Verify your iPhone document regarding the track with trustworthy software. Such a program helps to detect any viruses, malware, or future security threats.
- Alert your network about phishing messages:
Alert your friends about the issue to avoid the monitoring trickle-down. Warn them not to open any links or reply to the shady messages they'll be receiving from the tracked account.
- Modify your passwords:
So that it is not easy to access your accounts inadvertently, you should immediately update all your iCloud and Apple ID passwords.
- Eliminate suspicious apps:
Move through the apps on your iPhone, separating those that are unsafe or were downloaded from shady sources.
- Reset your iPhone:
To ensure that you have fully eliminated all spyware or illegally gained access, reset your iPhone to factory settings.
Part 7. FAQs
Q1. What's the best monitoring app for iPhone?
Through the above comprehensive review, it is easy to find that SpyX is the best iPhone monitoring app because of its simple connection process, which doesn't require you to install any software on the target device, and the second thing is that its monitoring feature is very powerful, which can remotely monitor more than 30 kinds of data such as, SMS, location, WhatsApp and so on.
Q2. Can I track someone's iPhone without detection?
Yes, it's possible. You can use specialized spy software such as SpyX. SpyX doesn't require any software to be installed on target device, no logo or icon will appear on the target device, and no alerts will pop up, so you don't have to worry about being detected at all.
Q3. Is it legal to break into an iPhone?
No, iPhones do not allow apps to be tracked unless the owner permits that and is not used for immoral or vulgar purposes.
Q4. Are there any track apps in the App Store or not?
Monitoring apps never appear in the App Store. They are mainly open source and do not belong to any particular organization.
Part 8. Conclusion
This article ends here! I believe you will have a deeper understanding of iPhone monitoring after reading this article, no matter you want to find the best iPhone monitoring app, or you want to find out how to protect your iPhone from monitoring, you should already have the answer!
More Articles Like This