Know how to monitor iPhone messages & keep your messages safe
Table of content
Securing your iPhone messages becomes paramount in this era, where smartphones store a range of personal information. This article dives into the world of iPhone message monitors. It offers an understanding of the techniques employed, identifies signs that indicate monitoring, and provides vital tips for safeguarding your messages.
Part 1. What is the iPhone text message monitor
In an era dominated by advanced technology, understanding the basics of iPhone text message monitoring is foundational. Contrary to the misconception that monitoring involves intricate processes, contemporary methods have evolved, emphasizing the need to demystify these techniques.
The iPhone text message monitor revolves around exploiting vulnerabilities within the device's messaging system, allowing unauthorized access to private conversations.
Acknowledging this shift from traditional notions of monitoring is pivotal for users to stay informed and take proactive steps to safeguard their messages. As we delve into the intricacies of iPhone message security, unraveling the simplicity of these monitors becomes paramount, empowering users to counter potential threats effectively.
It is this understanding of the fundamental concepts that lay the groundwork for a comprehensive approach to securing one's iPhone messages in the digital age.
Part 2. How does it work
There are various ways to monitor SMS. The traditional way is to implant a virus into a cell phone by the user clicking on a link. The more advanced way is to use third-party software to install the virus onto the phone, even without installing it. Therefore, we need to understand how this more advanced software works and what it can do on your phone.
2.1 Take SpyX for example
SpyX is a popular monitoring software on the market. Parents often use it to monitor their children and ensure their safety. One of its great features is that users don't need to jailbreak, root, as well as download the app. using real-time cloud synchronization, you can remotely control someone's every move on their device.
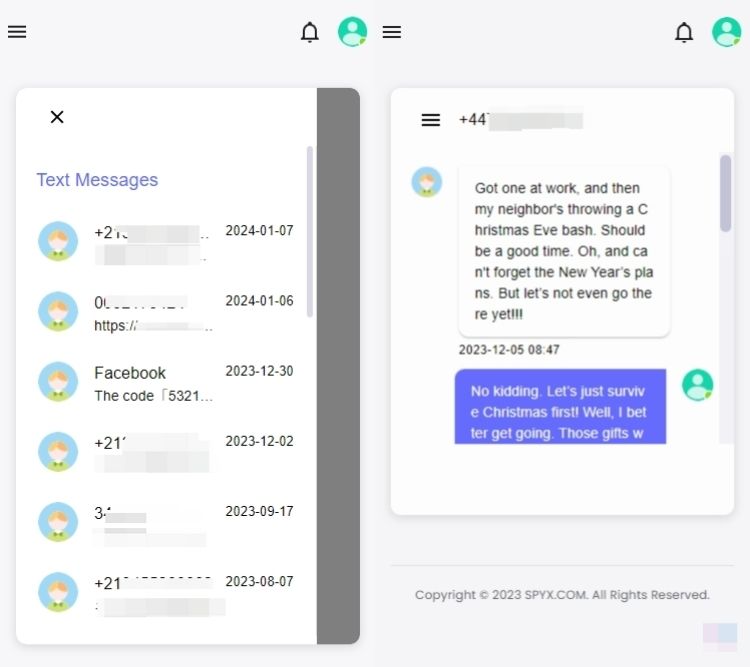
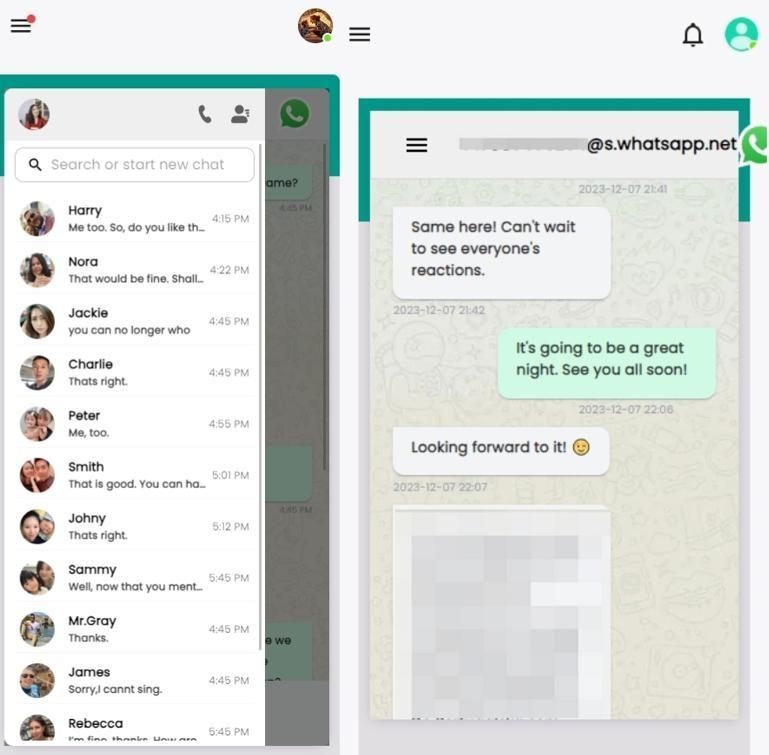
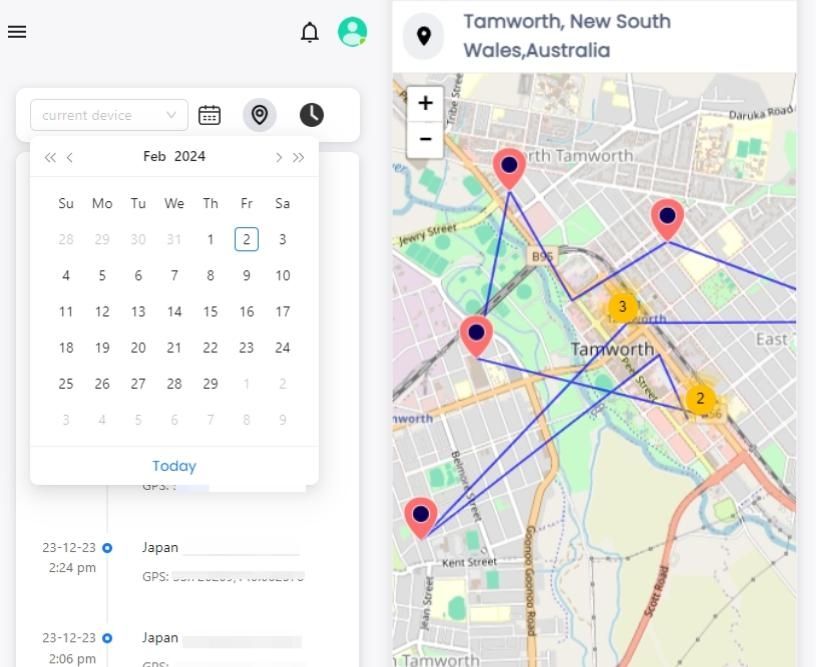
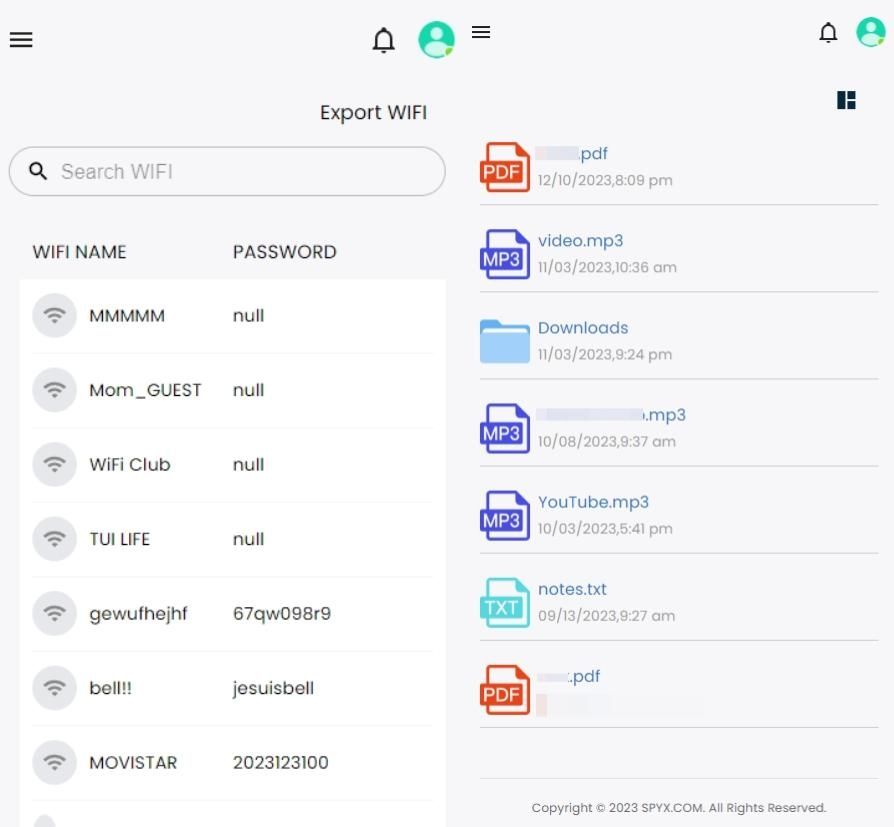
2.2 What messages can you get on iPhone with SpyX
2.3 Other features of SpyX
2.4 How to monitor iPhone messages without them knowing
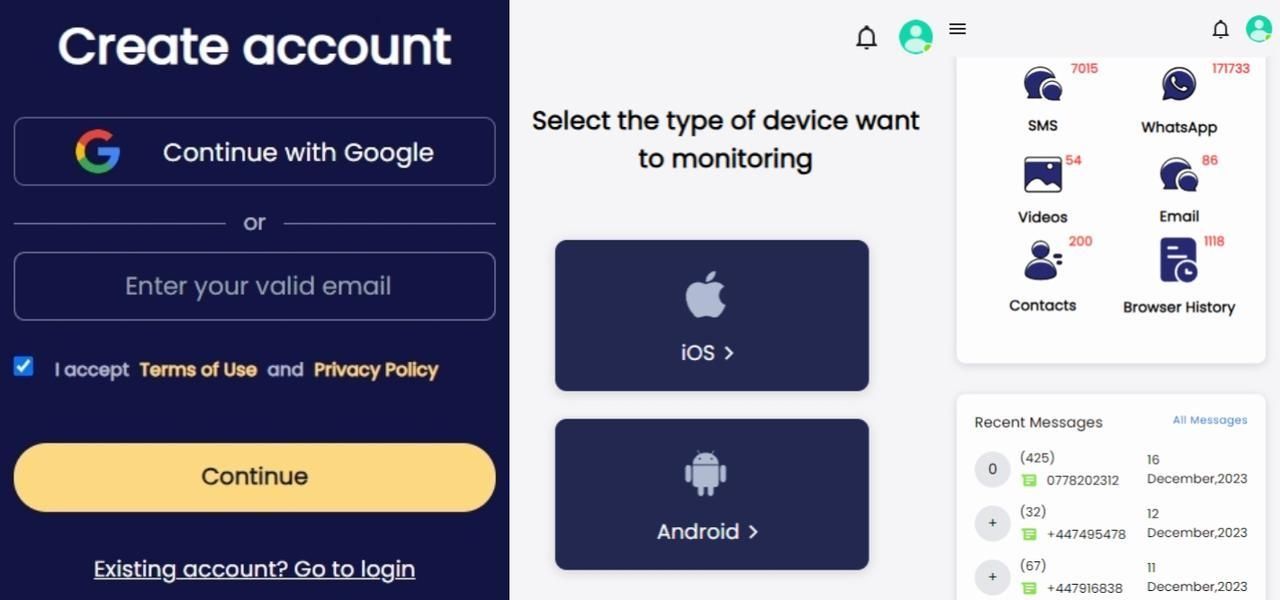
SpyX does not require any download, so it is not going to have any icon on the desktop of the target device. This also means that with SpyX you can monitor someone's phone and read messages without them knowing it. To use SpyX, you only need to complete the following steps.
Step 1. Create an account on the SpyX website with a valid email address.
Step 2. Select the target device you want to monitor: Android or iOS, and follow the instructions to bind the selected device.
Step 3. Start monitoring. Click on a specific feature in the dashboard or sidebar to view its data.
Part 3. Is there any other way to monitor iPhone messages
The simple answer is, yes. In the constantly evolving landscape of cybersecurity, monitorers deploy various tactics to breach iPhone messages beyond direct monitoring. Understanding these alternative methods is crucial for users to fortify their digital defenses.
3.1 Through iPhone's security holes
Monitorers often exploit vulnerabilities within the iPhone's security infrastructure. These security holes, if left unpatched, serve as entry points for unauthorized access to messages. Regularly updating your device's operating system and applications is pivotal, as these updates often contain security patches that address and seal these potential loopholes.
It’s essential to be aware of the evolving landscape of cybersecurity threats. Some monitorers specialize in identifying undisclosed vulnerabilities, known as zero-day exploits. These exploits target weaknesses not yet known to the device manufacturer or the public, making it crucial for users to stay informed about emerging threats and promptly apply updates to counter potential security breaches.
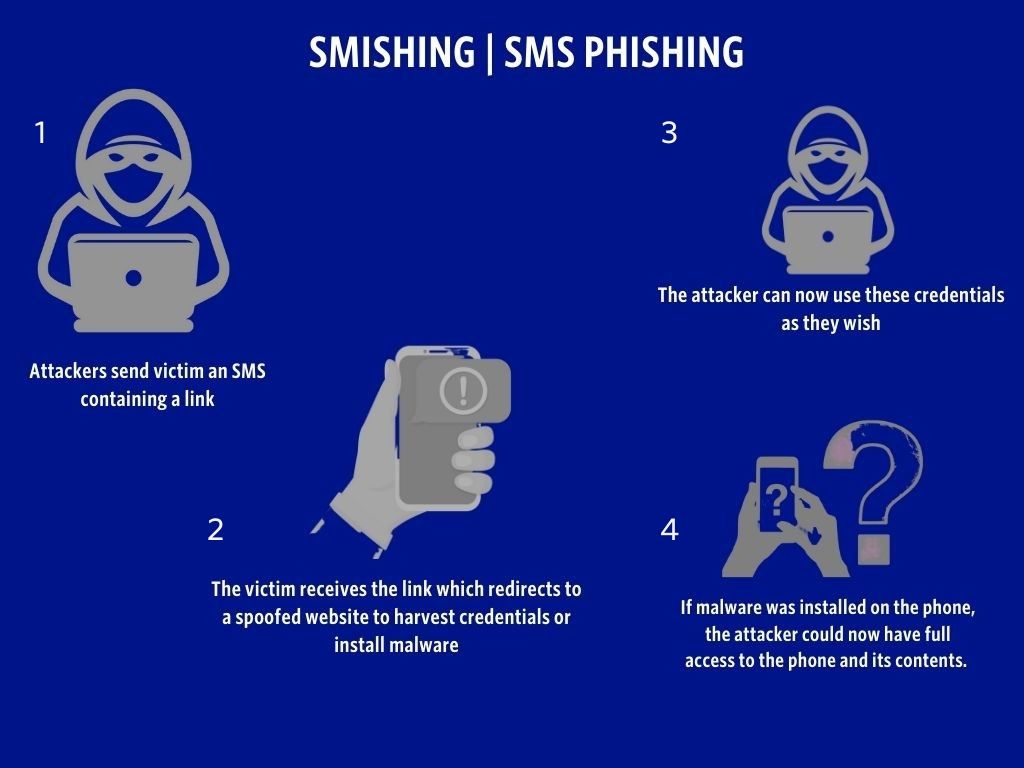
3.2 Using phishing messages - containing malicious links
Phishing messages represent a prevalent avenue for monitorers to infiltrate iPhone messages. By crafting deceptive messages containing malicious links, monitorers trick users into clicking, unwittingly granting access to their messages. Recognizing the signs of phishing, such as unexpected or suspicious messages, and avoiding clicking on unverified links are fundamental practices to thwart this method.
Users should also be cautious about the personal information they share online. Monitorers often tailor phishing messages with seemingly innocuous details obtained from social media or public profiles to increase their credibility. Being mindful of the information one shares and employing privacy settings can act as an additional layer of defense against phishing attempts.
3.3 Using web pages to plant viruses
Compromised web pages can serve as silent carriers of viruses aimed at infiltrating iPhone messages. Users may unknowingly expose their devices to these threats by visiting websites with malicious intent. Vigilance in navigating online content, avoiding suspicious websites, and installing reputable antivirus software can mitigate the risk of virus infiltration through web pages.
It’s also crucial to understand the concept of drive-by downloads, where viruses are automatically downloaded without user consent upon visiting a compromised webpage. Implementing browser security settings and regularly clearing cache and cookies can minimize the risk of unintentional downloads and enhance overall online safety. Stay informed, stay secure.
Part 4. Signs of iPhone messages monitoring
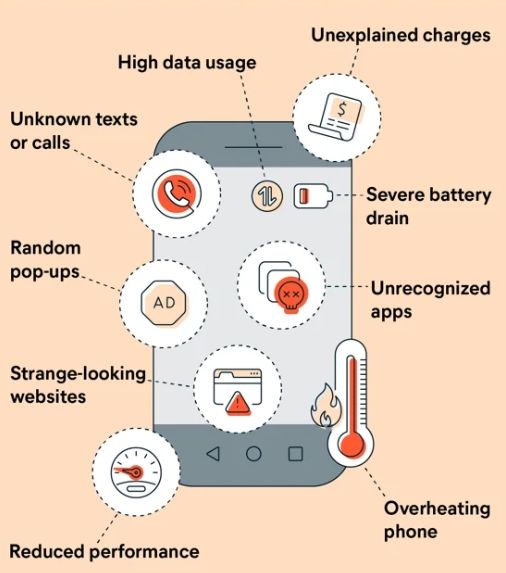
In an age where our smartphones serve as gateways to our most private conversations, knowing if someone reads your messages, recognizing the signs of potential monitoring is crucial. Here are three key indicators that your iPhone messages might be compromised:
4.1 Unusual activities
- Identifying Abnormal Behavior Within Your Messaging Apps
Monitorers often leave a digital trail of irregularities when infiltrating messaging applications. If you notice unexpected behaviors such as messages marked as read without your interaction, sudden message deletions, or unexplained changes in chat settings, these could be signs of unauthorized access. Pay close attention to any anomalies, as they may signify someone else gaining access to your private conversations.
4.2 Unrecognized messages
- Addressing Instances of Unknown or Unauthorized Messages
One of the clearest red flags of a potential iPhone message monitor is the presence of messages you didn't send or receive. If you find unfamiliar messages in your conversation threads or notice texts that seem out of character for your contacts, it's time to investigate. This could indicate a breach, with someone gaining unauthorized access to your messaging account and sending messages on your behalf.
4.3 Slow device performance
- Recognizing Performance Issues as Potential Indicators of a Breach
A compromised iPhone may experience a slowdown in performance due to the additional strain placed on its resources by malicious activities. If you notice your device becoming sluggish, unresponsive, or experiencing frequent crashes while using messaging apps, it could be a sign of a security breach. This performance degradation occurs as monitorers exploit vulnerabilities, consuming more system resources to execute their unauthorized activities.
Recognizing these signs promptly is essential for taking immediate action to secure your iPhone messages. If any of these indicators raise concerns, it's advisable to investigate further, employing additional security measures and, if necessary, seeking professional assistance to mitigate the potential risks associated with a compromised messaging system. Stay vigilant and proactive to ensure the integrity of your private conversations.
Part 5. What to do if your iPhone SMS is monitored
5.1 Immediate actions
- Identify suspicious activity: The first step in addressing a potential iPhone SMS monitor is to keenly observe any irregularities. Look for unauthorized access, unusual messages, or any unexpected changes in your messaging app.
- Change passwords: Swiftly change your Apple ID and messaging app passwords to prevent further unauthorized access. Ensure the new passwords are strong and unique to enhance your account's security.
- Log out of all devices: Use your device to log out of all active sessions. This will forcibly disconnect any unauthorized users from your account.
By taking these immediate actions, you disrupt the monitorer's access and secure your account promptly. Changing passwords and logging out of all devices create an initial barrier against further intrusion.
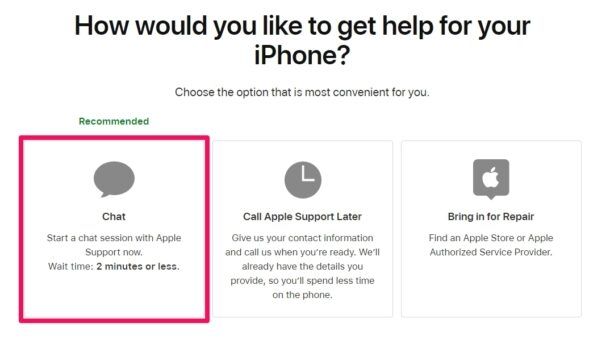
5.2 Contacting support
- Reach out to Apple support: As soon as you suspect a monitor, get in touch with Apple Support. They possess the expertise to guide you through the recovery process and can provide specific advice based on your situation.
- Provide necessary information: When contacting support, be prepared to provide details such as the nature of the suspicious activity, any unusual messages received, and the steps you've taken so far. This information aids in a more efficient resolution.
- Follow support guidance: Apple Support may recommend additional steps to secure your account and prevent future monitors. It's crucial to follow their guidance diligently to ensure a comprehensive recovery.
Utilizing the assistance of Apple Support is vital in navigating the complexities of a potential monitor. Their timely intervention can mitigate the extent of damage and help you regain control over your compromised messaging account.
In essence, the combination of immediate actions and reaching out to Apple Support forms a robust strategy for responding to an iPhone SMS monitor. Time is of the essence, and by promptly securing your account and seeking professional assistance, you can minimize the impact of the breach and regain control over your private messages.
Part 6. How to secure iPhone text messages
In today's digital landscape, securing your iPhone text messages is not just about identifying vulnerabilities but actively taking steps to fortify your device. Here are two crucial measures to ensure the confidentiality of your messages:
6.1 Update your iOS
- The importance of regular updates
Keeping your iPhone's operating system (iOS) updated is more than just a routine task; it's a fundamental aspect of maintaining a secure device. Apple consistently releases iOS updates that include essential security patches, bug fixes, and improvements. By neglecting these updates, you expose your device to potential vulnerabilities that monitorers can exploit.
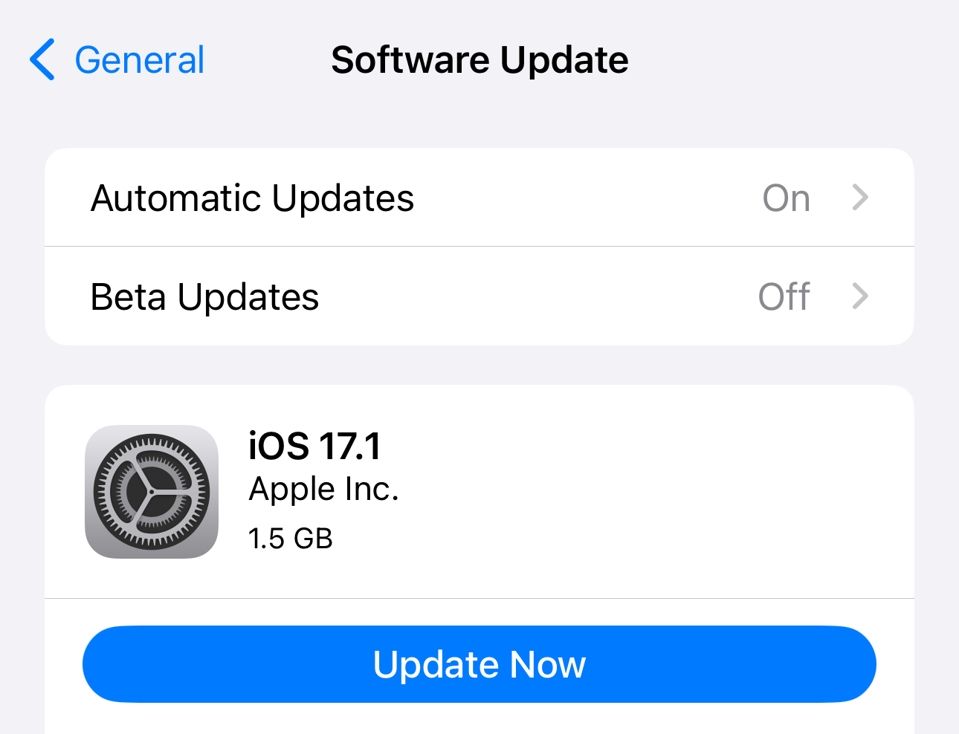
How to update iOS
- Navigate to "Settings" on your iPhone.
- Select "General" and then tap on "Software Update."
- If an update is available, click "Download and Install."
- Ensure your device is connected to Wi-Fi and has sufficient battery life to complete the update.
Automatic updates
For added convenience and security, enable automatic updates. This ensures that your iPhone installs the latest software enhancements without requiring manual intervention.
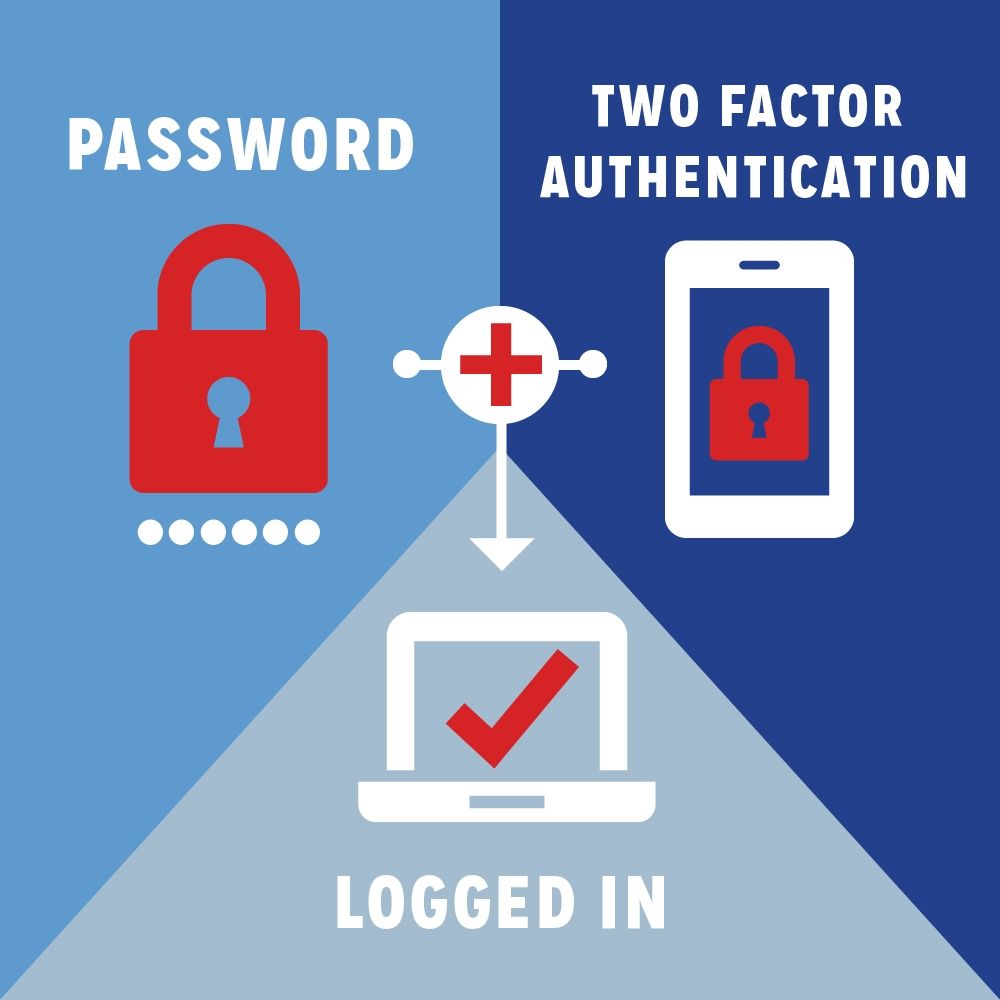
6.2 Enable Two-Factor Authentication
- Understanding Two-Factor Authentication (2FA)
Two-factor authentication adds an extra layer of security by requiring users to provide two forms of identification before accessing their accounts or sensitive information. For iPhone users, enabling 2FA is a simple yet highly effective way to bolster the security of your text messages.
How to enable Two-Factor Authentication
- Go to "Settings" on your iPhone.
- Select your name at the top and choose "Password & Security."
- Tap on "Turn on Two-Factor Authentication."
- Follow the on-screen instructions to complete the setup.
Benefits of Two-Factor Authentication
- Enhanced security: 2FA ensures that even if your password is compromised, an additional verification step is needed for access.
- Secure verification codes: With 2FA enabled, you receive verification codes on trusted devices, ensuring that only authorized users can access your messages.
6.3 Additional tips for message security
- Use strong passwords: A strong, unique password for your Apple ID adds an extra layer of protection.
- Review app permissions: Regularly review and manage app permissions, restricting unnecessary access to your messages.
- Be careful of third-party apps: Avoid downloading unverified or suspicious third-party apps that may compromise your message security.
By diligently following these steps, you not only secure your iPhone text messages but also contribute to an overall safer digital experience. Stay proactive, stay secure.
Part 7. Final summary
In short, ensuring the security of your iPhone messages has multiple factors attached to it, demanding heightened awareness, vigilance, and proactive initiatives. Grasping the tactics used by monitorers, identifying early signs of a potential breach, and adopting robust security measures are pivotal in safeguarding your private messages.
With a comprehensive understanding of these aspects, you strengthen your defenses, ensuring that your communication remains confidential and shielded from unauthorized access. Stay well-informed, stay vigilant, and stay committed to implementing the necessary security protocols.
In this ever-evolving digital landscape, your proactive approach serves as the frontline defense against potential threats. By staying one step ahead, you not only protect your messages but also contribute to a safer and more secure digital environment for all users. Stay connected, stay secure.
Part 8. FAQs
Can someone monitor your iPhone and see everything you do?
In fact, some surveillance software is able to monitor into your iPhone. Like SpyX, users can use it to remotely monitor your every move on the phone and you won't even notice.
How do you see deleted messages on iPhone?
You can recover and see deleted messages on your iPhone by backing up, using a third-party tool, contacting your carrier, and more.
Is it illegal for someone to read my text messages without my permission?
Laws and regulations vary from country to country and it depends on the situation. If you are the guardian of a minor child, then you are allowed to view their text messages without their consent. But this may damage the trust between you and your child. So, it is advisable to consult the local laws and regulations before checking, and it is best to seek your child's consent.
Can someone monitor your phone number?
Of course. If someone monitors into your phone, then all the data in your phone could be leaked, including your cell phone number.
Can someone monitor into my phone by texting me?
Normal text messages cannot monitor your cell phone. But usually, monitorers use phishing text messages with a suspicious link attached to it, and once you click it, then there is a high probability that your phone will be monitored.
More Articles Like This
SPYX'S SOFTWARE INTENDED FOR LEGAL USE ONLY. You are required to notify users of the device that they are being monitored. Failure to do so is likely to result in violation of applicable law and may result in severe monetary and criminal penalties ...







Disclaimer: SPYX'S SOFTWARE INTENDED FOR LEGAL USE ONLY. You are required to notify users of the device that they are being monitored. Failure to do so is likely to result .....