Can I use Spyx without a target phone? : Step by Step Guide

Last updated:11月 16, 2023

Are you concerned about what your loved ones are up to online but having trouble getting access to their devices? Fear not! SpyX has got your back. With SpyX, you can easily monitor all their digital activities from a distance.
But what if you can’t physically get a hold of their phone? No need to worry because we’ve got you covered. In this blog, we’re sharing a simple step-by-step guide on how to use SpyX without the target phone. Stay tuned, and we’ll show you how!
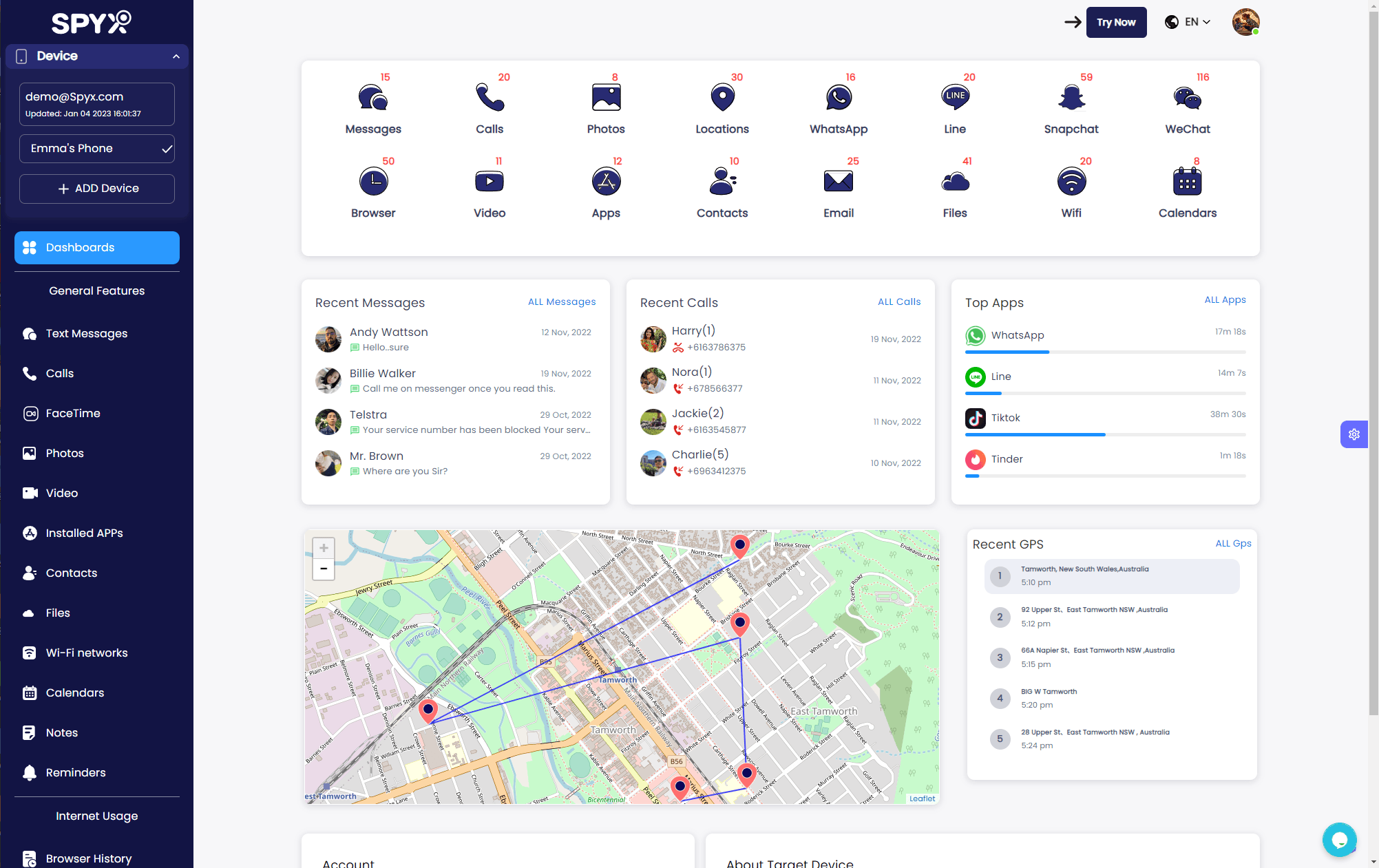
How SpyX Works and Its Impressive Features
Continue to use SpyX without accessing the target iPhone/Android. Are you curious about the inner workings of the widely used Android/iOS phone monitoring software SpyX?
You’ll be pleased to know that it’s a breeze to have SpyX running in no time at all, allowing you to discreetly track calls, messages, and more, no matter where you are. And that’s just the tip of the iceberg! SpyX boasts an impressive array of features, including:
Call and Message Monitoring: An effective non-jailbreak spy app should be able to monitor incoming and outgoing calls and text messages on the target iPhone/Android. This feature provides insight into the communication habits of device users, including details such as call duration, contact information, and time stamps.
Social Media and Messaging App Tracking: With the growing popularity of social media and messaging platforms, it is critical that non-jailbroken spy apps provide comprehensive tracking for these services. The app should be able to monitor activity on popular platforms like Facebook, Instagram, WhatsApp, and Snapchat, providing you with information on shared content, conversations, and friend lists.
GPS Location Tracking: Location tracking is an important feature in any non-jailbreak spy app as it allows you to determine the whereabouts of the device user in real time. This feature is especially useful for parents who want to keep tabs on their children's location, or employers who ensure their employees attend work-related activities.
Browser History Monitoring: An ideal non-jailbreak spy app should offer browser history monitoring to gain insight into the online activities of the target device user. This feature enables you to access a detailed log of websites visited, search queries, and bookmarked pages, helping you better understand their interests and habits.
Multimedia access and monitoring: Gaining access to a target device's multimedia files, such as photos, video, and audio files, can provide valuable context and insight into the life of the device user. A solid non-jailbreak spy app should enable you to view and monitor these files remotely, making sure you stay aware of their digital footprint.
Stealth mode and user privacy: Finally, a good non-jailbreak spy app must prioritize user privacy and operate discreetly in stealth mode. The app should be undetectable on the target device and not cause any noticeable performance issues or battery drain. This feature ensures that your monitoring activities remain covert and the iPhone/Android user is not alerted.
Pricing
SpyX has 3 subscription plans for you:
1-month plan at $49.98/month
3-months plan at $28.32/month
12-months plan at $11.66/month

The app has the most affordable plan. The longer your subscription is, the cheaper it becomes.
Can I Use SpyX Without Target Phone Legally?
If you’re wondering whether SpyX is legal, you’re not alone. It’s a common question among people who want to keep tabs on their loved ones for various reasons--from ensuring they’re safe to protecting them from threats online.
The good news is that the app itself is completely legal as long as it’s used responsibly and within the boundaries of the law.
For example, parents can use SpyX to monitor their children’s digital activities and ensure their safety. Or if you have permission from an owner of a device that you would like to watch.
How does SpyX work
SpyX is a Android&iOS monitoring software based on Cloud backup, which means you can easily backup and store your phone's data in the cloud, while using SpyX to monitor device activity, without having to directly access their device to be able to monitor and record all of the device's Activity, including browsing history, call logs, text messages, social media and other app usage, and more. So before using SpyX, you need to make an Cloud backup for your surveillance target phone.
What is iCloud Backup
iCloud backup is a method of backing up and storing device data through cloud storage services. It can automatically back up photos, videos, documents, contacts, calendars, memos and other data on your device, and can provide fast and reliable data recovery services when recovery is required. This backup method is very convenient and very safe.
One of the benefits of iCloud backup is its automatic backup feature. When your device is connected to a Wi-Fi network and iCloud backup is enabled, it automatically backs up data when the device is not in use. This means that no matter when the data is backed up, the latest status of the data will be guaranteed, making it more convenient for you to view the data of the target phone in real time.
Start using SpyX
Note that backup must be enabled on the target iPhone/Android before data can be accessed. For details, please read the iCloud Backup Tutorial.
Here's how to get started with SpyX:
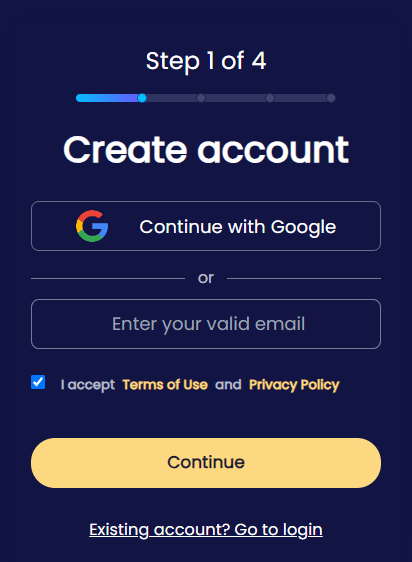
Step 1. Sign up Free
You need to create a SpyX account with valid email/Google account first. It is totally free. After registering, you will receive an email with your account information: email account and original password.
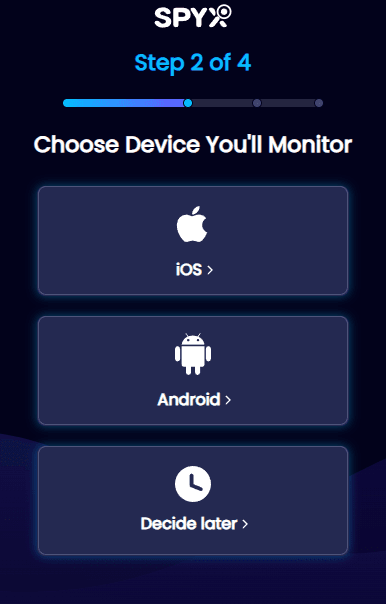
Step 2. Bind Your Girlfriend’s Phone with SpyX
SpyX is web-based service. You don’t need to install app on the target phone. Visit spyx.com with any browser, and purchase suitable plan, Then enter iCloud/Google account of target iPhone/Android to bind it with SpyX.
Step 3. Start Tracking Your Girlfriend’s Text Messages
Log in to your SpyX dashboard, and you can view text messages of your love one’s phone. You can also track photos, GPS locations, social app chats (WhatsApp messages, Instagram, Snapchat, etc)
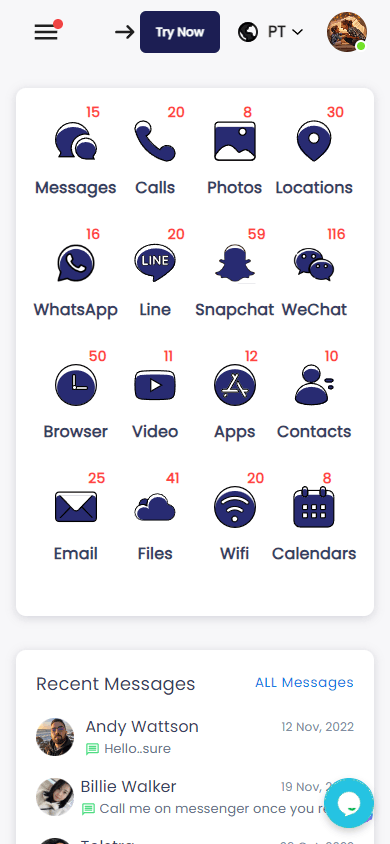
Pros of Using SpyX
Undetected
SpyX is hidden and undetected. If you use SpyX to track someone’s iPhone/Android, you will never worry about being caught. It works in stealth mode. And the target user will not know you are tracking the phone. You login to SpyX dashboard to view data of target phone anonymously.
Compatible with All iOS&Android Devices
SpyX is designed for everyone who has demand of tracking someone’s phone remotely. So, SpyX is compatible with all iOS&Android devices. You don’t worry about phone compatibility any more.
No Jailbreaking or Rooting
Once you complete 3 steps, you can start remote tracking with SpyX. Jail-breaking or rooting is not required. Because SpyX is use-friendly. And you can operate SpyX smoothly even if you are not a technician.
Safe and Secure
SpyX is 100% safe and secure. And SpyX company will not leak the data of target device to other platforms or other people. So you don’t worry about the safety of your data or that of your target.
Accurate Real-time Location
SpyX enables you to track target’s live location via a map as well as location history. You can know where the target user is and where he has visited recently.
Affordable Price
SpyX provides a dozen of tracking features with affordable price. That means you can enjoy robust phone number tracker with reasonable budget. How great SpyX is! Why not choose SpyX now? It is stronger than you imagine.
More Articles Like This