Learn how to track LINE and prevent LINE from being tracked

Last updated:7月 10, 2024
Table of content
Tracking LINE, a chat app that a lot of people use, is very dangerous because it can expose private information and put users at risk.
There are several ways that trackers might try to get into LINE accounts, no matter how popular the app is.
This article is about how to keep your LINE account safe from being tracked. It looks at popular ways to track LINE, such as SpyX crack and undetectable browser crack.
Part 1. What is LINE track
A "LINE track" is when someone changes or takes over your LINE account without your permission. Most of the time, they break the law to do this.
There are several ways for trackers to get into LINE accounts: spy apps like SpyX crack, brute-force attacks, phishing schemes, or malware to get in.
Once someone gets into your LINE account, they can read your texts, steal your private information, and do other bad things.
Part 2. How LINE trackers work-taking SpyX as an example
SpyX is a phone spy app that lets you listen in on and record conversations on phones. Some good things can be done with SpyX, like keeping an eye on workers or kids.
But it has also been used to track into LINE accounts and other places. It works without being seen, so the user can get to different kinds of information without the target knowing.
The LINE function of SpyX
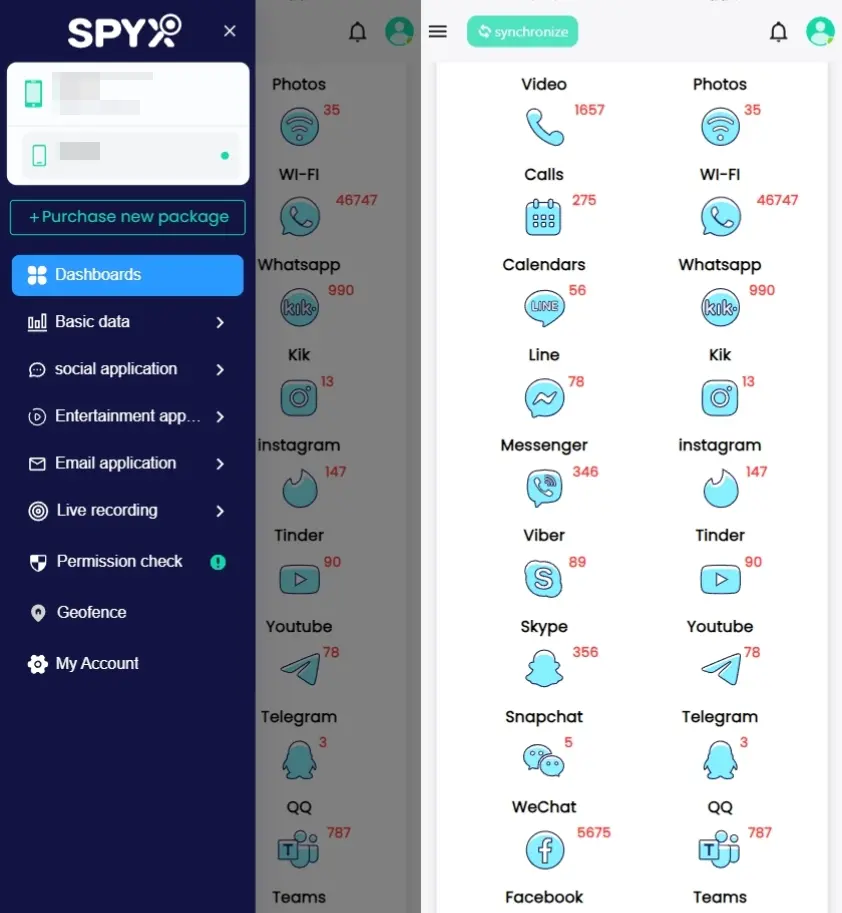
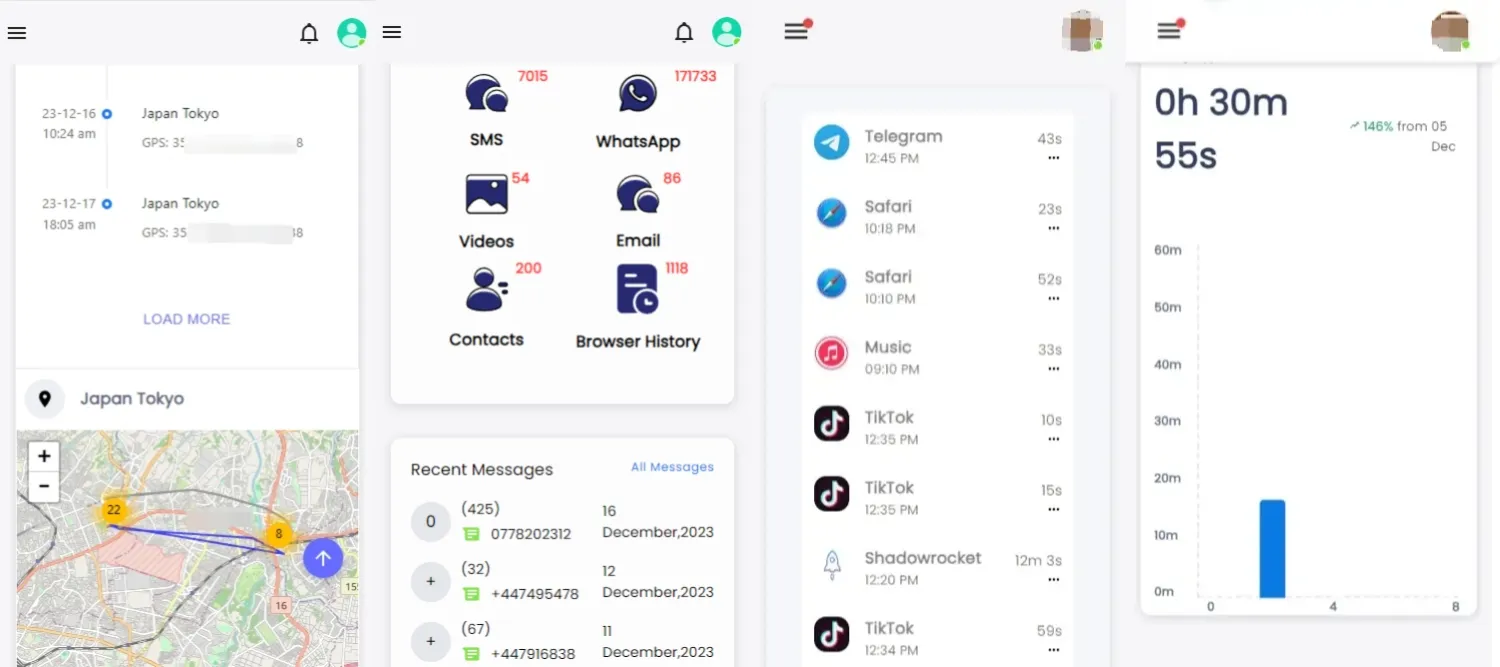
SpyX offers specific functions designed to monitor LINE activity. You can track LINE messages, call logs, contacts, and media files shared within the app.
This functionality makes SpyX an effective tool for those seeking to track LINE or keep track of someone's communications on the platform.
How to track someone’s LINE using SpyX
To use SpyX to attack LINE, you don't need to download and install the app. SpyX is a program that does not require jailbreaking, so it becomes easier to track LINE with it.
Its steps are as follows:
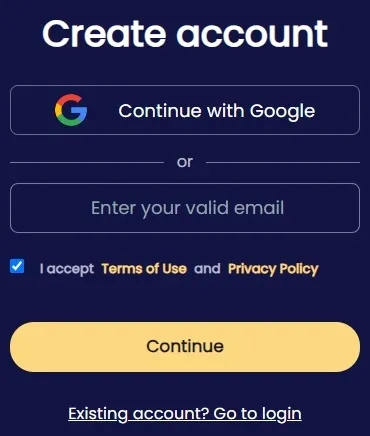
Step 1. To use SpyX to track someone’s LINE, you first need to register an account on its website.
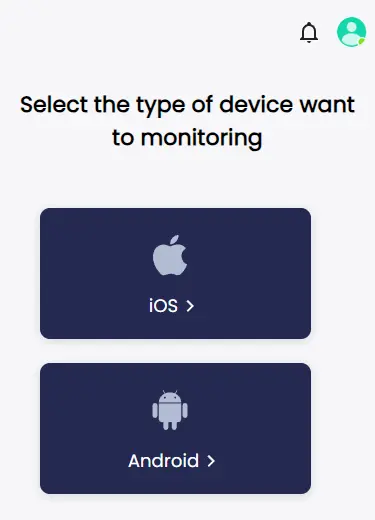
Step 2. Bind the mobile phone you want to track LINE. You can choose to bind it through a cloud account, which eliminates the need to install an app on someone’s phone.
It won't show up on the home screen or app list, so the person being monitored won't notice.
Step 3. Once SpyX is set up, it will start syncing information from the device. LINE chats, call logs, contact information, and media you share are all part of it. The data is then transferred to your phone via encryption.
Other functions of SpyX
Most of the time, SpyX is used to track LINE, but it can also be used to spy on other data! The following are some of these extra benefits:
The biggest advantages of using SpyX LINE tracker
Remote Monitoring: As long as there is an Internet connection, you can use SpyX to view someone's phone data anytime and anywhere.
Undetected: It's not possible for the target to find SpyX. Because it doesn't require downloading and installation, it doesn't leave any messages or app icons, so it's not likely to be found and won't be detected by detection software.
No Need to Jailbreak or Root: Some other spy apps need the device to be tracked or rooted to work. SpyX doesn't however. If you jailbreak or root an iPhone, it often opens it up to other security risks and can cancel your warranty.
Part 3. Other ways for trackers to crack LINE
Multiple methods exist for trackers to get into LINE accounts. Brute-force attacks on passwords are an example of an easy method.
Social engineering plans are an example of a hard method. You need to know about these ways to stop trackers and the risks that come with them.
This is what trackers usually do to get into LINE. I'll quickly explain each one. Remember that you should only use these methods to learn more about security or make people more aware of something.
Attempting to guess or brute-force a user's password
Trackers often try to guess LINE users' passwords because it's easy for them to get in. To do this, one way is to use brute force.
In these types of tracks, computers try as many as a million or a thousand different passwords until they find the right one. Password dictionaries have lists of common passwords that trackers could use.
They could also use algorithms to look at information about users and guess possible passwords. It might take a while, but brute-force attempts can work if the user's password is weak or based on patterns that are simple to figure out.
Insecure passwords, like "123456" or "password," make it easier for trackers to get into accounts. People who want to protect themselves from brute-force attacks should make strong passwords that include capital and lowercase letters, symbols, and both capital and lowercase letters.
Phishing
People often use accounts that have been tracked to get into LINE accounts. Part of this plan is to send fake emails, texts, or social media posts that look like the real ones.
The person behind the attack wants people to give away their login information or click on dangerous links. Bad guys want people to tell them something secret that will let them get into your LINE account.
People should be careful not to give out personal information in messages they didn't ask for or click on links from sources they don't trust.
Malware
Trackers can use viruses, Trojans, and other harmful software that users' devices get to get into their LINE account.
Malware can get into your device and log you in, record what you type, or get private information you've saved on it. The person who does this could see the user's LINE account and private information.
Malware can be spread by a lot of things, like infected email files, dangerous websites, and apps that have been tracked.
It can gather data in the background and send it to the thief once it's been set up. Follow these safety tips and also use security tools.
Social engineering attacks
Tricks or threats are used to get private information from people. This is known as "social engineering."
Trackers could pose as real people, like customer service reps, LINE admins, or technical staff, to get people to give them their login information or other personal data.
By claiming to be someone else, social engineers try to get people to reveal private details.
Exploiting system vulnerabilities
Trackers can also get into LINE accounts through known bugs in the app or operating system. To do it this way, you need to find bugs in the tool that lets people change data or get in without permission.
Trackers sometimes use hard-to-understand tools to find these holes and get into LINE systems or users' phones. You have to be skilled and have certain tools to use flaws in a system against someone else.
Users should always make sure that their apps and operating systems are up to date to protect themselves from this type of attack.
Part 4. How to know if your LINE has been tracked
When people track into LINE, bad things can happen, like data and identity theft. As soon as someone breaks in without permission, you need to stop more damage right away.
These are the most likely signs that someone has gotten into your LINE account. You can protect your account faster with these signs, and bad things are less likely to happen.
Unusual activity
A lot of the time, the first sign of a track is strange behavior in your LINE account. This can include messages sent to your friends out of the blue, changes to your profile, or strange behavior in group chats.
If you see conversations or actions that you didn't start, it's a clear sign that someone else may be able to get into your account.
Unauthorized access and unrecognized devices
While using LINE, you can see what devices are linked to your account. Someone might be breaking in if you find gadgets that aren't recognised or if you can get in from places you aren't used to.
Trackers often read accounts in this way, and the users don't even know it. Keeping an eye on your connected gadgets can help you notice any strange behaviour.
Password change
Someone probably tracked your account if you get a message saying that your LINE password was changed without your permission.
This might happen if someone got your login information and changed it so you can't get into your account. It's a big problem that your password was changed without your permission. It needs to be fixed right away.
Strange messages or calls, suspicious Emails
If you get a message saying that your LINE password was changed without your permission, it's likely that someone tracked your account.
This could happen if someone got your login information and changed it so you can't get into your account. It is very bad that someone changed your password without your permission. It should be fixed right away.
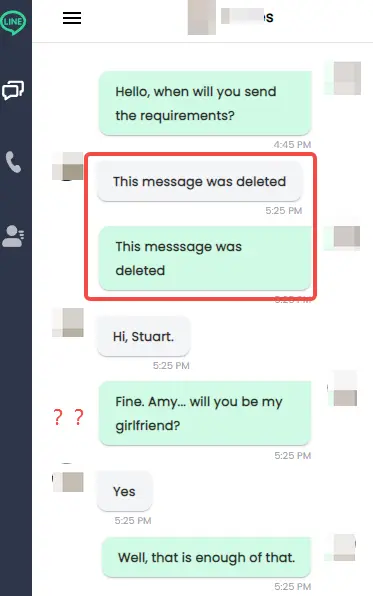
Missing or deleted data
If you lose chats, friends, or media files from your LINE account, someone may have changed a few things in it.
For privacy reasons, trackers often delete evidence of their actions, which can lead to data loss. It's worth doing more research if you find that important files or letters have been lost.
Additional signs of tracking
Besides the above points, there are other indicators that can suggest a LINE track:
Unusual App Behavior: The LINE app may have been tracked or got malware if it acts strangely, slows down, or stops a lot.
Increased Data Usage: An abrupt rise in data use could mean that spyware or a tracking app is active and sending data to a tracker.
Unexpected Logouts: If your LINE account logs you out without warning, it could mean that someone else is trying to take over.
Part 5. How to protect your LINE account from being tracked
You should keep your LINE account safe so that no one can get into your personal information or listen in on your chats.
They can get into your LINE account in a number of ways, but you can protect it and make it less likely that someone will track it. To keep your LINE account safe, do these key things.
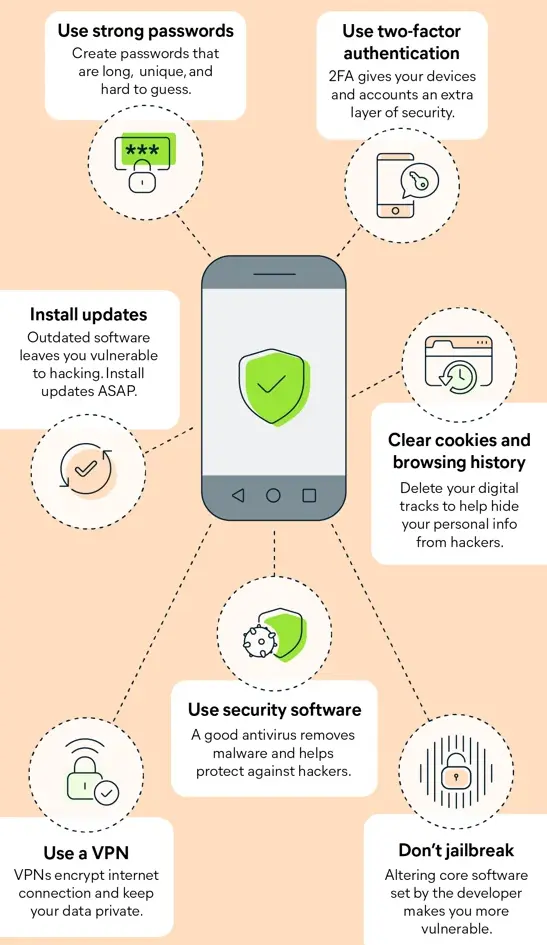
Use a strong password
People who want to track will try, but a strong password will stop them first. Make sure that your password is big, hard to guess, and unique.
It needs to have big letters, numbers, symbols, letters (upper and lowercase), and letters. Don't use things that are simple to figure out, like birthdays, well-known words, or short strings of numbers like "12345."
You might want to use a password generator to make long passwords and keep them safe.
Enable two-step verification
Adding two-step verification to your LINE account makes it even safer. In this case, you need to enter both your password and a verification code that was sent to your phone or email to get into your account.
After this step, it will be much harder for people who know your password to get in. Then, go to LINE's security settings and follow the steps given there.
Keep software updated
To stay safe, it's best to keep your tools up to date. Trackers could use security holes and bugs that users can get fixed.
Always make sure that both the LINE app and the system on your device are the most recent versions. Keep an eye out for changes and make them right away. This is what will keep your business safe.
Beware of phishing attempts
Tricks are often used by people who want to get into your LINE account. Be wary of emails, texts, or links that seem fishy or ask for personal information.
People often give trackers their login information or click on links that are bad for them when they phish them. Don't click on links that people you don't know or trust send you in texts.
Download the LINE app and any updates from official sources
Tracks are often used by people who want to get into your LINE account. Be wary of emails, texts, or links that seem fishy or ask for personal information.
Trackers can easily get people to give them their login information or click on links that could be harmful by scamming them. Don't click on links from people you don't know or trust.
Periodically review your LINE account activity
Regularly going over your LINE account activity can help you find logins that you didn't make or that don't make sense. Check the list of devices that are linked to see if any of them are new to you.
Take anything out of the room that shouldn't be there and change your password right away. Being careful in this way can help you find possible security holes early on.
Logout from unused devices
LINE can be used on more than one device, but make sure you log out of the ones you're not using. No one else should be able to get in if you leave your account open on computers that aren't being used.
LINE should be off on all of them except the one you're using now. Someone is less likely to use your phone to get into your account without your permission when it's not being used.
Additional tips to protect your LINE account
Before you take the main steps above, you might also want to think about these other ideas to make your LINE account safer:
Avoid Sharing Personal Information: Before posting something online, think about what you want to say. This is especially important if it's in a public place like a web page or group. Thieves can use these to try to figure out your passwords or security questions.
Use Security Software: Put security or antivirus software on your devices to detect spyware and get rid of any malware or bugs that might be trying to get into your LINE account.
Secure Your Devices: Keeping your electronics safe will keep others from getting to them without your permission. Intruders can't get into your phone if you use screen locks, fingerprint readers, or face recognition.
Part 6. FAQs about tracking LINE
Q1: How do trackers track a LINE account?
Tracks can get into a LINE account in several ways. They could use SpyX or another program that needs to be physically put on the device they want to spy on.
Once it's installed, the software can keep track of texts, call logs, and other private information in stealth mode. They also use brute-force tactics and phishing to get people to give up their login information.
Phishing is the act of sending fake emails to people to get them to give up their login information. Trackers often get into LINE accounts by using malware and tricking people into giving them information.
Q2: How can I tell if my LINE account has been tracked?
There are a few clues that someone has gotten into your LINE account. Your account may have been tracked if you notice strange activity, such as messages being sent from your account that you didn't send.
Some other signs are changes to your password that you didn't expect, devices that aren't mentioned in your login history, data that goes away or is deleted, and calls or texts from friends that don't make sense.
Q3: What should I do if my LINE account has been tracked?
It is important to change your LINE password right away to a strong, unique one if you think your account has been tracked.
To make things even safer, turn on two-step verification. Look at your past logins to your account and get rid of any gadgets that aren't recognised.
Check your account information for changes that were not made by you, like changed profile information or friends.
Do not click on links that look sketchy or give out personal information if you think it might be phishing.
Part 7. Conclusion
There are many ways for trackers to get into LINE accounts, such as using SpyX LINE tracker, through brute force, phishing, malware, social engineering, or system flaws.
In daily life, pay attention to regularly checking the usage of your software to ensure data security.
More Articles Like This