How to Spy iPhone | Remote & Secret

Last updated:Jul 15, 2024
Table of content
Ah! Someone’s searching for ways to get into someone’s phone without touching it. Haven’t gotten anywhere with your search? Don’t worry because this time you’ve landed on the right page. Whether you’re a parent, an employer, or simply someone who’s concerned about the well-being of their loved ones, this article encapsulates everything you need to know. So, if you want to know how to spy into someone’s iPhone without touching it, let’s begin.
Part 1. Is it possible to spy an iPhone
Yes, it is possible to spy an iPhone, and you can do so by going through several ways including spyware, logging into someone’s iCloud account, using malicious Wi-Fi, links, and the last resort: professional spyers. Out of all the methods, we have mentioned, the best one to get the job done would be to go with spyware technology.
Over the years, spyware technology has developed rapidly, and now it is possible to remotely monitor someone’s activities without having physical access to your target iPhone. Don’t worry, we won’t leave you hanging as we will explain everything there is to know regarding the monitoring methods, what data they can monitor, and what steps you need to take to install and utilize their perks.
Part 2. How to spy someone's iPhone without touching it-Using Spy app
2.1. What is the best iPhone spy app-SpyX
Without a doubt, SpyX is the best iPhone spying app. Its biggest advantage is that it doesn't require you to install any software on the target iPhone. This means that there will be no logo or icon on the target device, and you don't have to worry about the monitored person discovering any traces. SpyX allows you to remotely view all activities on someone's iPhone, such as text messages, photos, videos, location, WhatsApp chats, and more.
2.2. Features of SpyX
- No need to install any app on the target iPhone.
- Powerful monitoring features make SpyX the priority choice. It allows you to track phone calls, SMS, browser history, photos, GPS locations, WhatsApp, Snapchat, etc.
- Easy to use: Based on iCloud storage, you can finish the connection in 3 steps, 2 minutes.
- No need to jailbreak.
- Works in hidden mode. 100% undetectable and 100% secure.
- Track all phone activities remotely.
- Customer Support: 24/7 customer support is great. Whatever questions you have, just send through live chat.
- A free demo is available to everyone.
2.3. What data can SpyX spy
General features:
Social media:
2.4. How to use SpyX to spy someone's iPhone remotely
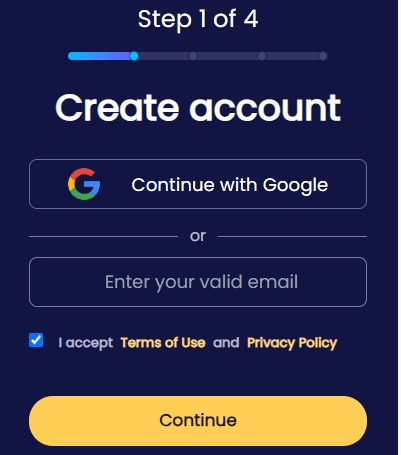
In only 3 steps, you can start spying someone's iPhone remotely.
Step 1. Create a free account with your email.
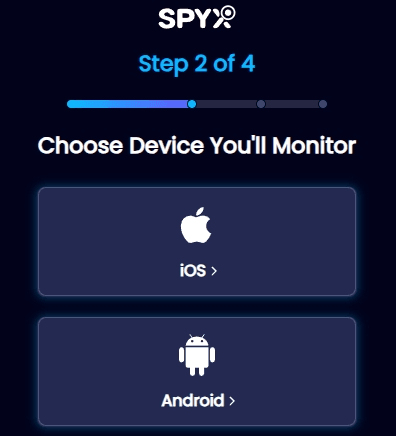
Step 2. Choose the device you want to monitor.
Choose "Android" for an Android phone and "iPhone" for monitoring an iPhone.
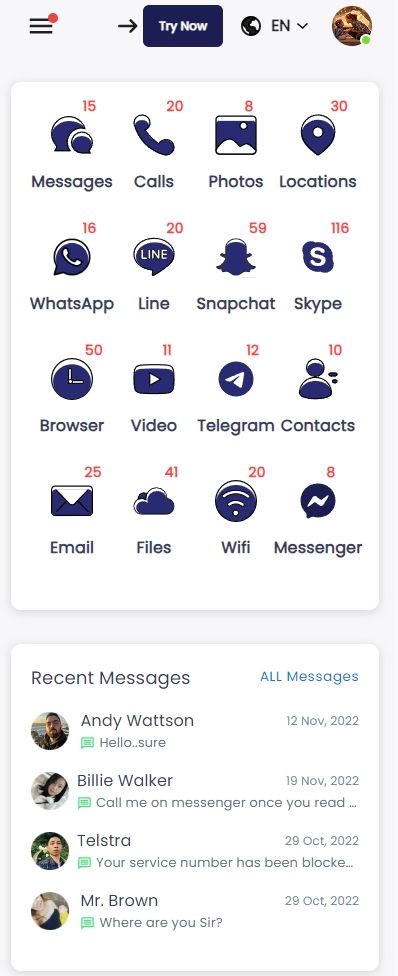
Step 3. Start spying.
Now you can remotely see 30+ types of data, such as text messages, call logs, GPS location, Instagram, LINE. Etc.
Part 3. Signs of someone is spying your iPhone remotely
Getting your cell phone spyed is not fun. It’s a little game of hide-n-seek that no one likes, and the worst part is? Some people may not even know whether their iPhone has been spyed or not. To protect your privacy, we’ve narrowed down some iPhone behaviors that can help you discover whether your iPhone has been spyed or not.
- Unexpected account logins: Your phone may have been spyed if you’re getting notifications of unrecognized logins to your social media accounts as well as your email.
- Unexplained draining of battery: If your iPhone battery is draining awfully quickly, it can be a sign that your phone might have been spyed.
- Unfamiliar apps: The premises of your iPhone may have been breached if you’re suddenly seeing unfamiliar apps on your phone.
- Abnormal usage of data: Not a single change in your phone behavior but there has been an abnormal data usage on your phone? It may be an indication that your phone might have been spyed by malicious spyers.
- Strange calls or texts: If you see unknown texts or calls in your log or if your friends are getting odd messages from your number, it may be a sign of a data breach.
Part 4. How to protect your iPhone from spying
Trackers are everywhere and their prying tactics can find you (if not already). If you haven’t been the victim of the spyers, it’s not too late. Let’s secure your phone together so no one can access your phone, apart from you. Here are some tips on how you can secure your phone.
- Set strong PIN codes/Passcodes: To lock your phone, use a complex PIN or password. Don’t just go with “1234” or “0000”.
- Turn Biometric Authentication on: Adding an extra layer of security can help you save your phone from spyers. In this case, enable facial or fingerprint recognition.
- Regularly update your software: To keep your spyers at bay, regularly update your software with up-to-date security updates and patches.
- Download your apps from a trusted source: Only download those apps, which you get from a trusted source, such as App Store on iPhone and Google Play Store on Android.
- Limit the App Permissions: The permissions you grant your apps must be limited and reviewed. Only give access to those features that are necessary.
- Stay cautious of Phishing: Be aware of unrecognized links, emails, or texts. Don’t click on any link that gives fishy vibes.
- Log out of all your accounts: Remember to log out of all your accounts once you’re done using them, especially in public places.
Part 5. What should you do if your iPhone has been spyed by someone
There might be some cases in which your iPhone gets spyed before you get the chance to do anything to protect it. In this case, there are several things you can consider to protect yourself from further harm at the hands of the spyers.
- If your iPhone has been spyed, the first thing you need to do is install the latest version of the software as this will enable the latest security patches on your iPhone.
- The problems may arise after you install some apps through a link, which is why you need to uninstall those apps immediately.
- For security purposes, you can install reputable security and antivirus apps on your phone to mitigate the threats.
- Your iPhone may be spyed after you connect to a public Wi-Fi network. If you feel this is the case, disconnect the Wi-Fi, and immediately forget that network.
- If you want to make your iPhone more secure, you can add an extra layer of protection in the form of two-factor authentication.
Part 6. FAQs
Q1. Is it possible to spy an iPhone?
While the iPhone has various security patches, it is still vulnerable to spying and can be spyed easily through spyware technology. So, yes it is possible to spy an iPhone, and if you want to keep a check and balance on the online activities of your loved ones, SpyX can be of great help.
Q2. How can I spy someone's iPhone to read text messages without their phone?
By using SpyX, you can spy into someone’s iPhone to read text messages without their phone. Once you log into the dashboard after finishing the initial steps, you can spy into someone’s remotely.
Q3. Can I spy someone's iPhone without being detected?
Yes, you can spy someone’s iPhone without being detected and this can be done through SpyX. SpyX is a software that requires no app installation, and you can easily spy someone’s iPhone without being detected.
Q4. Can I spy an iPhone by phone number?
No, you can’t spy an iPhone by a phone number. If you see any such claims, remain cautious and don’t fall into any traps.
Part 7. Conclusion
Voila! There you have it – The easiest way of spying into someone’s iPhone without giving them an indication that they are being spyed. With the help of the right tools by your side, you can become the hero of this digital world. With SpyX as your partner, you can keep an eye on your children without having their phones or without them knowing. With our tips on how to keep your phone safe, you’ll remain one step ahead of those cyber-street smarts, as you should be. Cheers to a more secure and safer future in this digital, tech-savvy world!
More Articles Like This