How to Track Your Children's Email

Last updated:janv. 13, 2025
Tracking your children's email can be allowable if the devices are connected. First, on your child's device, open Settings. Then click Google and proceed to parental controls. Get started, select your child's account to connect them to your device, and set up the supervision on the child's account.
There isn't a problem if your child is willing to show you their email, but the issue emerges when you covertly monitor your child's email. In such circumstances, you would need the best mobile spy app or email monitoring program to track or gain access to someone's email account. Monitoring software makes access to every incoming and outgoing message, every email's date and time, and recipient information.

Part 1. How to Track Your Children's Email Remotely
1. Track Children's Email with SpyX
You can track your children's email with SpyX. Your digital parental assistance can help you monitor your children's email and keep them safe from different activities circulating on the internet that will cause them a negative impact.
2. How to Use SpyX for Email Tracking
A smartphone espionage program called SpyX was introduced. You can see what is happening on a target device remotely. Spy on your children's or employees' phones will allow you to monitor their whereabouts and prevent them from acting in a way that is inappropriate or unacceptable. And you can follow the steps to track your children's email remotely:
Step 1. Sign up free with your valid email.
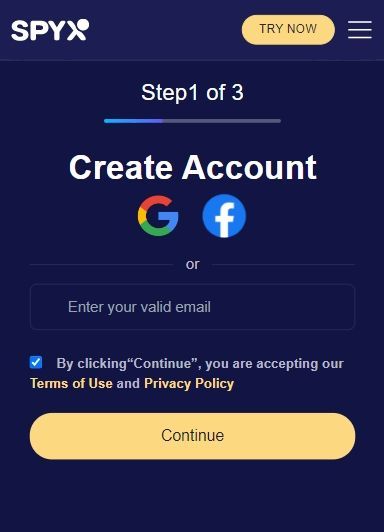
Step 2. Purchase suitable plan based on your needs.
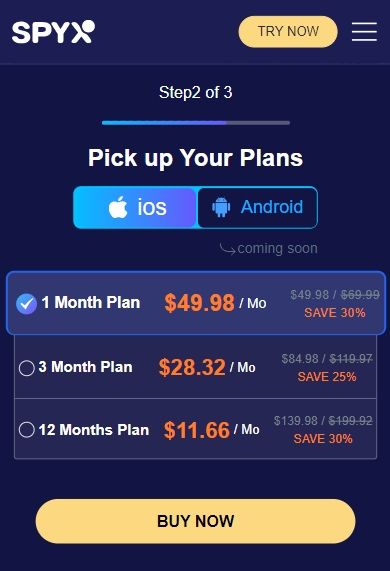
Step 3. Connect target phone with SpyX
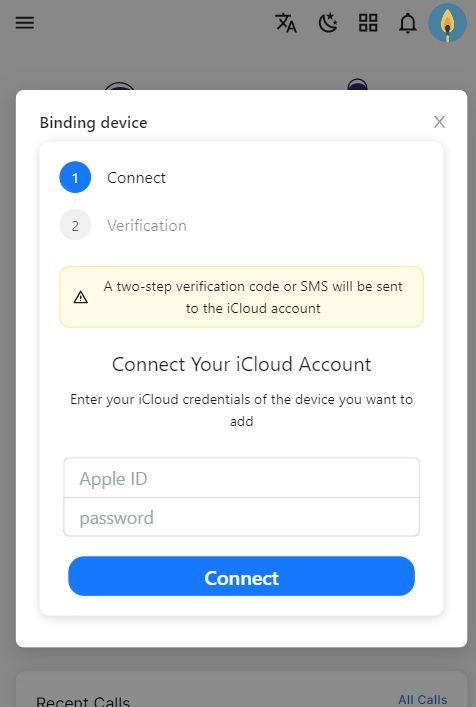
Step 4. Login to SpyX Dashboard and start tracking child's email.
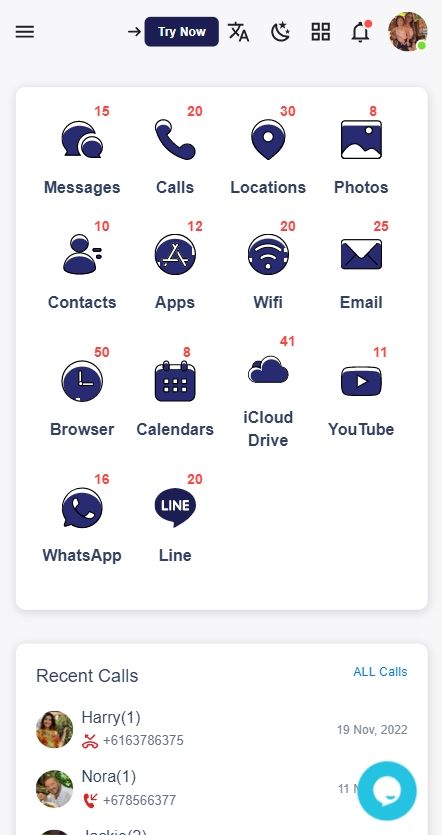
Part 2. Why Spy on Someone's Email with Tracking App
1. Email Tracking for Parents
Email tracking app allows parents to see what their child is doing and to whom they connect. This allows the parents to check their children and secure them. They might feel more at ease knowing where they are. Teenagers can assist their parents by informing them of their whereabouts so that they only need to check-in if they get concerned.
2. Email Tracking for Employers
Email monitoring is crucial to safeguarding your business from unfortunate incidents arising from lousy employee behavior or external threats like phishing, spam, etc. As long as there is a legitimate business justification, employers are free to monitor these messages. Many businesses support this right by informing staff members in writing—for instance, in an employee handbook—that company email is not private and is being monitored.
3. Email Tracking for Spouse
Email tracking adds background. You can learn a lot about your spouse's email exchanges with contacts and networks by using email tracking. This will strengthen the relationship between both, and if any case, this tracking email application will allow them to know the whereabouts of each other. Thus necessary activities in terms of social relationships will be tracked down.
Part 3. What Makes SpyX the King of Phone Tracking Apps
1. Easy Use
It is easy to navigate and use effectively following different steps provided. A user can use it effectively without worrying about a protracted due process.
2. 100% Safe
It is proven safe and allows the user to track an email without doubt of getting unsafely by the application.
3. Monitor Remotely
You can monitor a device wherever they are on their email, no matter how long the distance is.
4. Monitor Discreetly
You can easily monitor your child on their email without being noticed.
5. Track Deleted Content
You can also track deleted content using SpyX and save them to your device.
6. Reasonable Price
The price is reasonable for its quality. It provides a feature that is easy to navigate and provides an effective result.
7. No Need to Jailbreak or Root
Jailbreaking is not required for SpyX to use. Now you can watch over iOS devices that aren't jailbroken! You can keep an eye on your child's iPhone usage without jailbreaking.
8. 24/7 Customer Support
It offers 24/7 customer support. In unrequired situations, SpyX is willing to provide you with a hand anytime.
9. Powerful Tracking Features
SpyX is excellent at tracking texts, instant messaging, and phone usage. SpyX is a competent phone monitoring program that can track practically all of your child's email activity.
10. Professional Technical Team
It is handled by a professional technical team knowledgeable about tracking devices. Assuring the safety of users, the technical team updates its features for a stronger connection and practical use.
FAQs
Q1. Can I track someone's email?
Looking at the entire email header will allow you to identify the sender of any given email address. You usually ignore the routing details and metadata in the email header. However, that data is essential to determining the email's origin. You may spy on someone's email without their knowledge with the SpyX Email spying tool and view the contents of the email. It is usable with compatible gadgets.
Q2. How can I track the location of an email sender?
Installing a spy app covertly on the target person's phone allows you to track their location without them being aware. Through their emails, these phone spying apps keep tabs on practically all activities on the targeted phone. Google mail will display the sender's IP address, which can be used to determine where they are physically located. Open the sender's message in Gmail and select "Show Original" to learn more.
Q3. Can a Gmail account be traced?
TLS encryption during data transfers and industry-standard 128-bit encryption at other times safeguard Gmail users from hackers. But as the saying goes, you are usually the product when a good or service is offered for free. Gmail can be tracked because Google utilizes your data, making you vulnerable to ad tracking.
Q4. Can an email be traced to a cell phone?
If you are using a wi-fi connection with your cell phone and are sending emails from your computer, it is both conceivable and straightforward to determine your geographical location. Your cell phone is less location-specific, making it more challenging to pinpoint your exact location.
Q5. Do emails have an IP address?
There are no IP addresses in emails. The DNS system is queried for the name of a mail exchange that services a domain using the domain section of an email. The IP address is part of the message header and, if available, can be used by the recipient to determine the sender's general location. The sender's IP address is not always included in outgoing email messages from all email providers.
More Articles Like This