Track iPhone with Tech Expert | A Comprehensive Guide
Table of content
This article serves as a complete guide to hiring a tracker for an iPhone. The iPhone is considered near perfect as a security tool with its strong encryption. However, access to its content or a deep knowledge of its system is important.
This article focuses on what a tracker is, why you might need to hire one, what data trackers can help you obtain, what preparations you need to make when hiring a tracker, and a more cost-effective way to track an iPhone compared to hiring a tracker.
Part 1. What is a tracker
Cybersecurity is a field involving ethical tracking. They perform this duty through their ability to navigate through the digital world. They are the ones ensuring secure and trusted systems. This is done by actively hunting for vulnerabilities which can be fixed before a criminal attack.
Their mission is to secure the data of people and businesses. These gatemen stand for honesty and decidability. By showing the actual usage of technological abilities and their moral-related dreams. In the process of reducing the number of risks, these companies create higher boundaries of trust. They add confidence in the World Wide Web and also assure users that online business is harmless and secure.
Part 2. Why hire a tracker for iPhone
Nowadays, cell phones have emerged as one of the most used gadgets. Hence, ensuring security is also important for our phones. iPhone tracking is often associated with the idea of illegitimate work. However, ethical tracking is a security technique too. It is when iOS devices are in the hands of good trackers.
The idea of hiring a tracker might disturb some people. Ethical trackers, known as "white hat" trackers, are just like any other trackers. They have one thing different from other trackers. This is their ability to help you prevent security threats.
There are several reasons why it is worth considering hiring a tracker for iPhone security:
(1) Preemptive protection:
Resourceful computer professionals perform the task of spotting errors on iPhones. By using detailed scans and methods of penetration, vulnerabilities can be found. This helps prevent theft. This will protect your digital security system from the current risks.
(2) Account recovery:
In the case of lost access to the iPhone due to tracking, ethical trackers can help. By using the extensive skills, criminals can easily be detected. This helps minimise damage and restore your accounts. By this the security of your essential data is guaranteed.
(3) Customised security solutions:
Ethical trackers strive to create security protocols that specifically target the problems.
Whether you are an employer or a device user, you have the knowledge and skills to develop individualised plans. This can indeed save the life of not only your iPhone but also your digital assets.
(4) Conformity and rules:
So, data protection regulations do not allow deviation, and they should be followed. Ethical trackers can serve the company through compliance audits.
They can review the security standards of the organizations. By doing so, they can detect any vulnerability in the data security network. They also provide the necessary corrections for the shortcoming.
Part 3. What can a tracker do for your iPhone
An iPhone tracker can help individuals and organisations in many ways:
(1) Device unlocking:
It is a common scenario that we all have at least once in our lives. You forget your iPhone password and cannot get into your smartphone. When such a crisis exists, it is better to be in touch with an iOS or iPhone tracker.
By using particular methods and sophisticated programs, they can get past password protection. Thus, you can update the device's information again and get back to normal operations.
(2) Data recovery:
There is always trauma when you accidentally delete or misplace important information on your iPhone.
A tracker who has a command of the iPhone can track down and recover valuable images, vital papers, or important text that were removed.
Employing advanced data recovery methods helps them to recover the missing data.
(3) Security testing:
Today, the importance of cybersecurity must be considered. This is due to the rising cyber threats. So, enterprises seek solutions that would safeguard their data.
By implementing an environment that is like cyber crimes, weak security points in an organization can be detected. This is where ethical trackers do their work. They help in keeping valuable information secure from dangerous people.
(4) Customization:
Apple offers various customization options for iPhone users. However, individuals want more features. Apple may provide the iPhone with specified features by modification of the smartphone's settings.
To discover the hidden functions, custom themes are installed and system settings are changed. By doing so, experts can make your smartphone match your needs and particular demands.
Part 4. How to hire a tracker for iPhone
Hiring a tracker can be a hectic task. Below, you can find the best way to hire a tracker for an iPhone.
Step 1. Conduct in-depth research and comprehensive screening and selection.
Start by conducting a comprehensive study. Identify reputable cyber companies and exceptional white hat trackers.
Always look for those with certificates such as Certified Ethical Tracker (CEH) or Certified Information Systems Security Professional (CISSP).
You can also view their good reviews and feedback. Their previous clients confirm the service provider as legitimate and reliable.
Step 2. Preliminary meeting.
Following the list of possible candidates, compose an email or give a call to clarify the possible arrangements. You need to address the security threats, goals, and requirements.
Be clear with what you want. Always provide the needed information about the current security configuration of your iPhone. This will ease your troubleshooting.
These consulting sessions are a great way to reassure yourself. It allows the tracker to know your needs correctly. Hence, necessary measures can easily be taken.
Step 3. Examination and reference.
Soon after the first meeting starts, an ethical tracker will conduct a complete audit of the virtual security iPhone.
Employing the data collected, they will develop a comprehensive plan. This indicates the level of the project, measures, schedule, and expenses.
Scrutinize the proposal to make sure that it fits with your goals and the resources that are available to you.
If there are any confusions, please do not hesitate to clear them.
Step 4. Execution.
The next step will be accepting the submitted proposal. The ethical tracker will start the implementation phase after this step.
They will install security tools. This explores your iPhone's software and network, demonstrating the existence of vulnerabilities.
Maintaining relations with the tracker is crucial throughout this period. It helps in obtaining information on the developments. By doing so, you can get a quick solution of any emerging issues.
Learn that you are prepared to give the necessary work systems and the resources needed to carry out the process.
Step 5. Continuous surveillance.
In an era of strong cybersecurity, there needs to be continuous alertness and capacity to cope with future problems.
A group of ethical trackers delivers you ongoing security services. You can be sure that your device will be safe from threats all the time.
Have a continuous interaction with the tracker. Report any shady activity or strange discrepancies that you see on your device.
Keep in touch with the tracker. By getting involved, you can ensure long-term protection of your iPhone's security settings.
Part 5. Risks and considerations
To trespass upon another individual's device or data storage is a violation of their privacy and dignity rights. There are many risks and considerations when dealing with tracking. Let's have a look at a few:
(1) Legal consequences:
Apart from the ethical dismissals, the legal limitations should also be taken into account.
The intrusion of a digital device or data by typing the wrong password is an act that is considered unlawful in the Computer Fraud and Abuse Act in the US.
Joining in attacks by third parties can come with particularly dire negative outcomes. It can lead to imposition of heavy fines, and even criminal prosecution.
(2) Unintended consequences:
The peril of iPhone tracking could involve unimagined prospects. The device can be compromised by software manipulation or exploitation of vulnerabilities. It might cause harm. Besides that, unauthorized access to the device and its data may cause undesirable issues. These can be infringement of confidentiality or improper use. This can have more serious ethical and legal consequences.
(3) Ethical quandaries:
In addition, there are ethical problems that are not necessarily tied to legal and reputation concerns.
For this purpose, the process should give importance to security and asset protection. However, at the same time, privacy and liberty are protected.
Part 6. A better alternative-Using SpyX
6.1. What is SpyX
SpyX is the best stealth iPhone tracking software that allows you to remotely monitor all activities on someone's iPhone without being detected. It does not require you to get the target device to install any software, nor do you need to know the target iPhone's account and password to view their SMS, call logs, location, browsing history, installed apps, WhatsApp chats, and more than 30 other types of data in real-time.
Sounds impossible, right? That's because SpyX uses the most advanced cloud-based connection solution, making remote tracking a reality.
6.2. Features of SpyX
- No need to install any app on the target iPhone.
- No jailbreak required.
- Works in hidden mode. No icon or logo appears on the target iPhone.
- Tracking the target iPhone undetectable.
- Supports all iOS systems.
- Powerful monitoring features: spy on text messages, installed apps, FaceTime, Snapchat and 30+ types of data.
- Tracking the target mobile phone remotely.
6.3. What data can SpyX track
SpyX allows you to track into the following data on the target iPhone without installing any app.
General features:
Social media:
6.4. Steps of using SpyX to track someone's iPhone without them knowing
In only 3 steps, you can track someone's iPhone without them knowing.
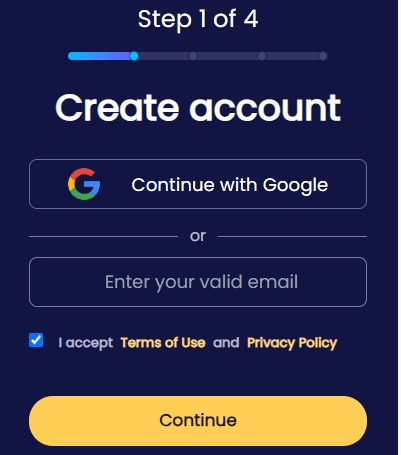
Step 1. Sign up for a free account with your email.
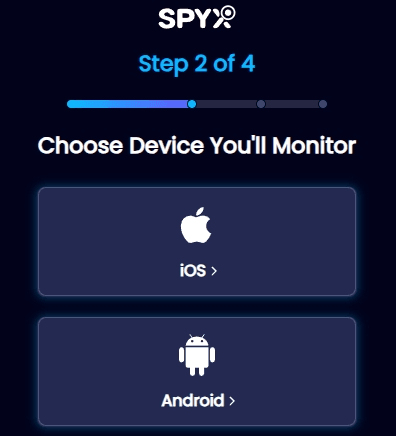
Step 2. Choose the device you want to track.
If you want to track an iPhone, select the "iOS" option. If you want to track an Android, such as Samsung, Motorola, Xiaomi, select "Android".
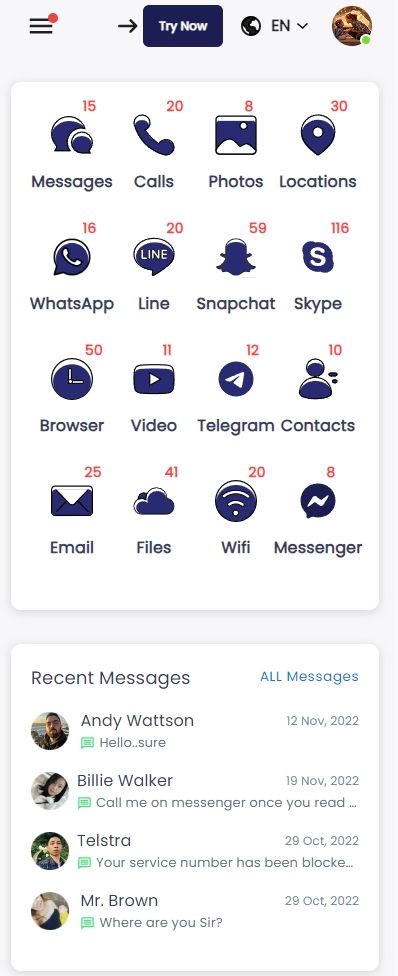
Step 3. Start tracking.
Now you can track text messages, contacts, browasr history, FaceTime, WhatsApp, Snapchat and over 30 types of data.
Part 7. FAQs
Q1. What are the alternatives to hiring a tracker for an iPhone?
If these services are considered insufficient, other options are available. These include engaging in any third-party surveillance application-SpyX. One can also inquire about the security abilities in the Apple operating system.
Q2. Is it legal to track an iPhone?
The hired tracker follows legal and ethical requirements to improve the security of the iPhone. Such acts are not illegal. However, gaining access to another person's devices without their consent is unlawful.
Q3. How to find a trustworthy security expert for an iPhone?
There are many well-known cybersecurity companies and individual ethical trackers. Search for a person who is experienced in a certain sector. They should be qualified. Credibility checks can be facilitated by viewing the comments and reviews.
Part 8. Conclusion
In conclusion, it is better to carefully view everything before making your choice to hire a tracker for iPhone safety. Ethical trackers aim to prevent cyberattacks. They also help in restoring taken-over internet channels. However, money-related issues and legal consequences should also be taken into consideration when choosing a tracker. So, third-party spy software like SpyX is also a good option for device monitoring. This platform enables extensive options. There are many customizable features and short instructions too. Finally, the decision to hire a tracker depends on the basic needs, cash availability and ethical issues. Whatever means are used, there is a necessity to protect personal and professional information.
More Articles Like This
SPYX'S SOFTWARE INTENDED FOR LEGAL USE ONLY. You are required to notify users of the device that they are being monitored. Failure to do so is likely to result in violation of applicable law and may result in severe monetary and criminal penalties ...
Disclaimer: SPYX'S SOFTWARE INTENDED FOR LEGAL USE ONLY. You are required to notify users of the device that they are being monitored. Failure to do so is likely to result .....