How to track an iPhone without password | 5 effective ways

Last updated:fev 14, 2025
Table of content
While iPhones have extremely high-security patches, and with every update, the security has been increased, it is still possible to track an iPhone without even having a password. To track an iPhone without a password, there are a number of approaches you can take, such as the best way of tracking an iPhone without a password using software or going with the free methods out there. We will explore each method one by one, but we’ll clear already that free methods may give you a headache at some point, so be aware!
Part 1. How to track an iPhone without password-Using SpyX
1.1. What is SpyX
SpyX is the most invisible tracking app for iPhone. It can easily help you track someone else's iPhone remotely without needing a password. Because it uses the most advanced connection solution-cloud connection, you also don't need to get the target device to install any software. At the same time, it is compatible with all iOS systems, whether you want to monitor iPhone 7, iPhone 8, or iPhone 14, iPhone 15, it can provide monitoring solutions.
1.2. Features of SpyX
- SpyX has the following features to help you better achieve your tracking goals.
- No need to install an app on the target iPhone.
- Tracking without needing a password.
- Ease of Use: SpyX is designed to be user-friendly, making it easy for anyone to use, even without technical knowledge.
- No jailbreaking is required.
- Works in hidden mode. No logo or icon appears on the target iPhone.
- Tracking 30+ types of data remotely.
- Offers 24/7 customer support.
1.3. What data can SpyX track
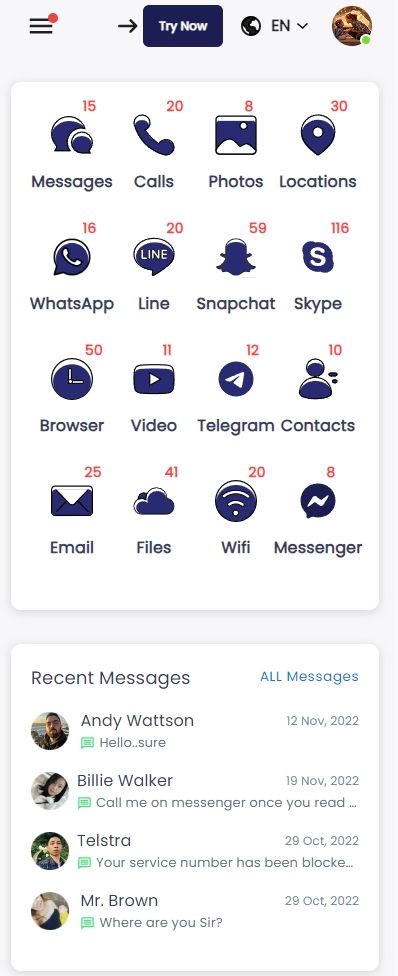
SpyX allows you to track into the following data on the target iPhone without needing a password.
General features:
Social media:
1.4. Steps of using SpyX to track someone's iPhone without password
In only 3 steps, you can track someone's iPhone without them knowing.
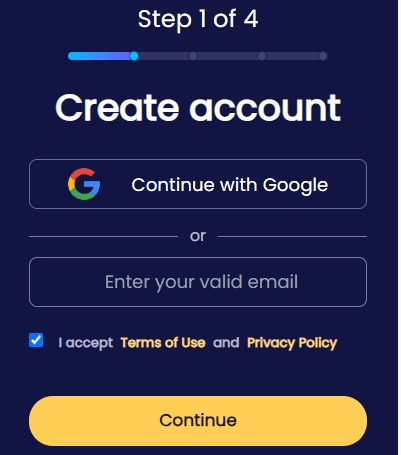
Step 1. Sign up for a free account with your email.
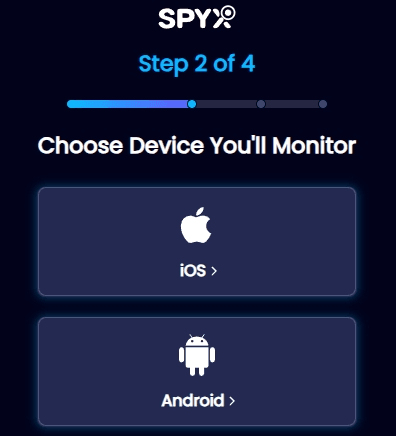
Step 2. Choose the device you want to track.
If you want to track an iPhone, select the "iOS" option. If you want to track an Android, such as Samsung, Motorola, Xiaomi, select "Android".
Step 3. Start tracking.
Now you can track GPS location, text messages, call logs, WhatsApp, Snapchat and over 30 types of data.
Part 2. How to track someone's iPhone free
Method 1. Tracking iPhone via “Tricking Siri (works on iOS 12)”.
Remember when IOS 12 was the culprit where users could use Siri to pass the lock screen? Below are the steps through which you can track an iPhone by tricking Siri.
Step 1. Try to long-press the side or the home button, and up will talk out your favourite Siri. After that, Siri will say, "Enable VoiceOver" to provide accessibility to VoiceOver audio.
Step 2. A slide of the Side button is what makes the iPhone go into power-saving mode. On the other hand, go and call your iPhone from the second phone. Press anywhere repeatedly; it doesn't matter where you do it; press twice and choose Custom. Then press and hold on the screen at the same spot in order to highlight the plus sign that has been shown in the bottom left corner of the message box.Subsequently, on your iPhone, text one of your closest pals. A deflating mood appears and motivates you to double-tap on the message.
Step 3. Then press the shown "plus" button on the upper right-hand side of the page. Then, slide left to where the Voiceover says "Cancel". Say "Cancel" to it and push on "Cancel" to choose this one option.
Step 4. Click two times at any other half of the keypad and options button, and check "numbers" also.
First, success by typing figures and then people names that begin with the figures you typed. Press "i" to inquire for information, press "Siri" to start, and press "Voiceover" to reverse.
Step 5. Therefore, see you soon, Siri. Select "Add to Existing Contact," then swim through your contact list. Add a picture, turn on "VoiceOver," select "Camera Roll.” Also grant permission to use the camera so that the image can be stored in the "Camera Roll."
Step 6. Dump Siri, tap on Add to existing Contacts icon, scroll further to where the photos are and pick one of them. Words like 'Siri', 'voiceover' and 'picture' will guide the visually impaired person with the aid of speech to produce the expected result.
Step 7. It is time to glance at the pictures and the things which you have kept aside. It runs a slow process. Furthermore, its success is only guaranteed sometimes.
Method 2. Tracking iPhone via “iTunes”.
Tracking an iPhone via iTunes is simple to do when you know which buttons to push. By doing this, you will turn the device to recovery mode and then use iTunes to restore it.
However, know that the procedure will have wiped everything on the gadget.
Step 1. Launch the iTunes version of the newer version on your PC, whether it is Windows or a Mac.
For iPhones before the 6s, try pressing the Home and Power buttons simultaneously until you see the iTunes icon.
Press and hold both the Power and Volume Down buttons together until the iTunes icon appears for the iPhone 7/7 Plus.
For models iPhone 8 and higher, press the Side key, then Volume Up, and finally, Volume Down until the icon of iTunes shows up.
Step 2. When iTunes detects that there is recovery mode, it accepts it by clicking restore or choosing to restore the device.
Method 3. Tracking iPhone via “Finder”.
The "Finder" app on macOS acts as an instrument to crack an iPhone using this method. This can be useful, especially if you need to restart the phone without using the passcode.
This can be a possible method, but you should be equipped with a Mac OS computer, or else it may only work for some.
Step 1. Link the iPhone to a macOS device using the USB cable.
Step 2. On your Mac, select the Finder application.
Step 3. Pick the joined iPhone from the Finder window.
Step 4. On the Stored data section of the iPhone, tap "Restore iPhone."
Step 5. To get your iPhone back to the way it was when you first got it, follow the on-screen directions.
Method 4. Tracking iPhone via “Find My”.
"Find My" is a very fast tracking option that needs an internet connection on an iPhone and does not require a computer or iTunes.
The Find My iPhone service from Apple has been developed with a specific focus on finding lost iOS devices. However, you can also use it to link two devices, which, when done, unlocks the device.
Meanwhile, you should also ensure that the phone is connected to the Internet and then switch on the Find My iPhone service on the target cell phone.
Furthermore, apart from your iTunes password, you have to possess the iCloud password for the linked account.
Step 1. Navigate to the official iCloud site through a different phone or search for the Find iPhone app on the device running on the iOS system. The next thing you need to do is use the iCloud passwords that can be retrieved from the target phone to log in.
Step 2. Following logging in, a list with all the connected devices will become visible. Select the iPhone from the list that you want to track. The iPhone will be capable of an instant load of its current latitude and longitude. At the bottom of the screen, there is a button labelled "Actions" Tap it.
Step 3. Have a list of choices, mark away, then choose the option "Erase iPhone," this will completely delete everything on your iPhone.
Step 4. Give a mere glance at your selection and timing the task to completion. It will already be at a great distance from him, and it will be this that will unlock it in the end.
Part 3. FAQs
Q1. Is it possible to unlock an iPhone without its password?
Of course, any human can try accessing an iPhone without the password. You can use Apple's built-in ways, such as "iTune" "Find My iPhone", you can also try the professional iPhone tracking app-SpyX.
Q2. Can I track someone's iPhone without installing any app on the target iPhone?
Yes, you can track someone's iPhone without installing an app on the target iPhone. SpyX uses a cloud connection solution, you just need to register a free account on the SpyX website and then follow the page guidelines to complete the two-step verification, there is no need to install any software at all!
Q3. Is SpyX a hidden iPhone tracking app?
Yes, SpyX is a completely invisible tracking app for iPhone. Because you don't need to install any software on the target device, so there won't be any logo or icon appearing on the target phone, nor any pop-up alerts, so you don't need to worry about being detected at all.
Part 4. Conclusion
In conclusion, one can crack into an iPhone without a password. However, you have to be attentive and follow the legal and ethical rules. There are numerous methods of how this can be done. Examples include using iTunes, Finder, and the Find My iPhone service or taking advantage of the loopholes in iOS. Each has its pluses and minuses.
You can also opt for a trustworthy tracking app like SpyX which offers privacy and security of the user. Protecting personal data and the digital rights of others is undoubtedly their top priority. People can hardly make their devices safe from threats and intruders. By opting for SpyX , one can dodge possible risks and observe the best practices for cybersecurity.
More Articles Like This