How to hack WhatsApp remotely: Legal ways & hacker ways
Table of content
In today's digital age, WhatsApp has become a ubiquitous communication tool. However, there are instances where individuals may find it necessary to hack into WhatsApp accounts for various reasons.
Whether it's concerned parents, suspicious partners, or individuals seeking to protect their privacy, understanding how to remotely hack WhatsApp can be invaluable.
This article explores different methods and considerations for hacking WhatsApp remotely.
Part 1. Why need to hack WhatsApp
WhatsApp is not just a messaging app. It's a gateway to personal conversations, multimedia sharing, and location tracking.
Concerned parents may want to monitor children's interactions, while suspicious partners may seek reassurance or evidence of fidelity.
Understanding the motivations behind hacking WhatsApp is crucial in navigating the ethical and legal implications of such actions.
Part 2. 3 ways to help you hack WhatsApp
This provides you with three ways to help you hack WhatsApp remotely. Let’s take a look!
Method 1. Get WhatsApp account password-the most direct way
This method is most suitable for individuals who have a close relationship with the target, such as parents monitoring their children's activities. It involves physically obtaining the target's cell phone to access their WhatsApp account.
This approach is often perceived as the most direct way to hack WhatsApp due to its simplicity and immediate access to the target's messages and data.
How to get someone’s phone and view his/her WhatsApp account and password
To execute this method, you must gain access to the target's phone surreptitiously. This may involve waiting for an opportune moment when the phone is left unattended or finding ways to temporarily borrow the device.
Once in possession of the phone, you can navigate to the WhatsApp application and view the account details, including the password if it is saved on the device.
Method 2. Hack WhatsApp via SMS
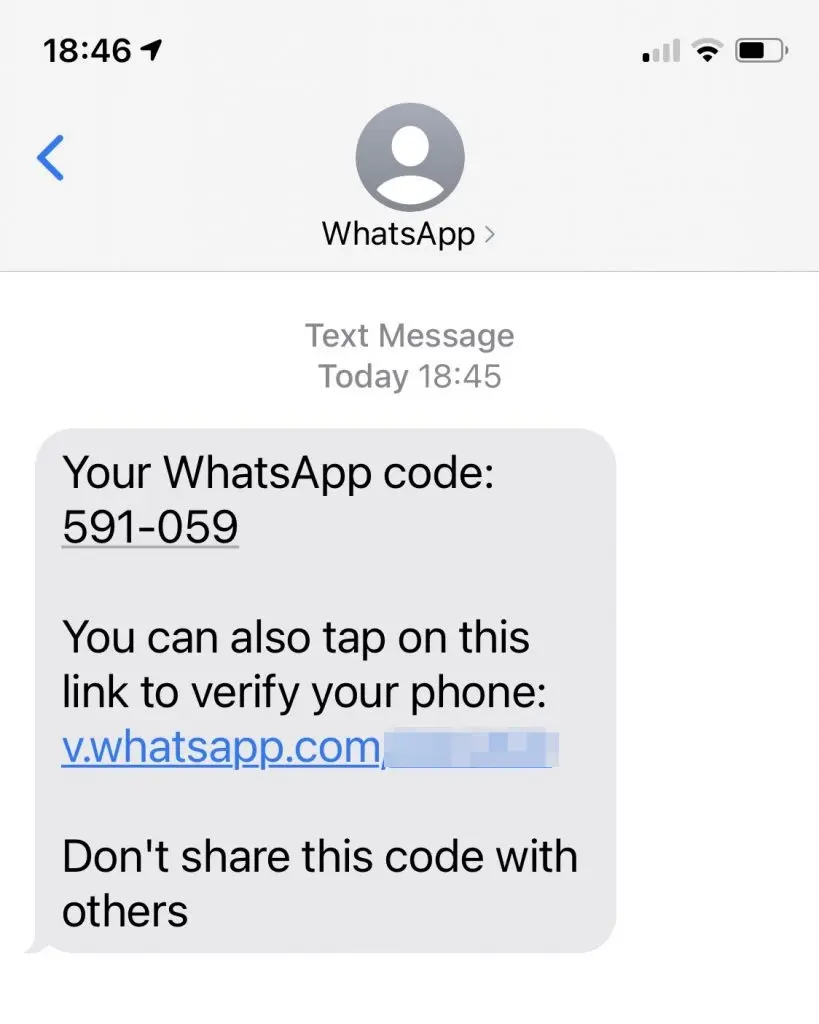
Hacking WhatsApp via SMS involves intercepting text messages sent to the target's phone to gain access to their account.
This method requires physical access to the target's device to retrieve and read incoming text messages. By monitoring the SMS communication, you can obtain verification codes or other sensitive information necessary to access the target's WhatsApp account.
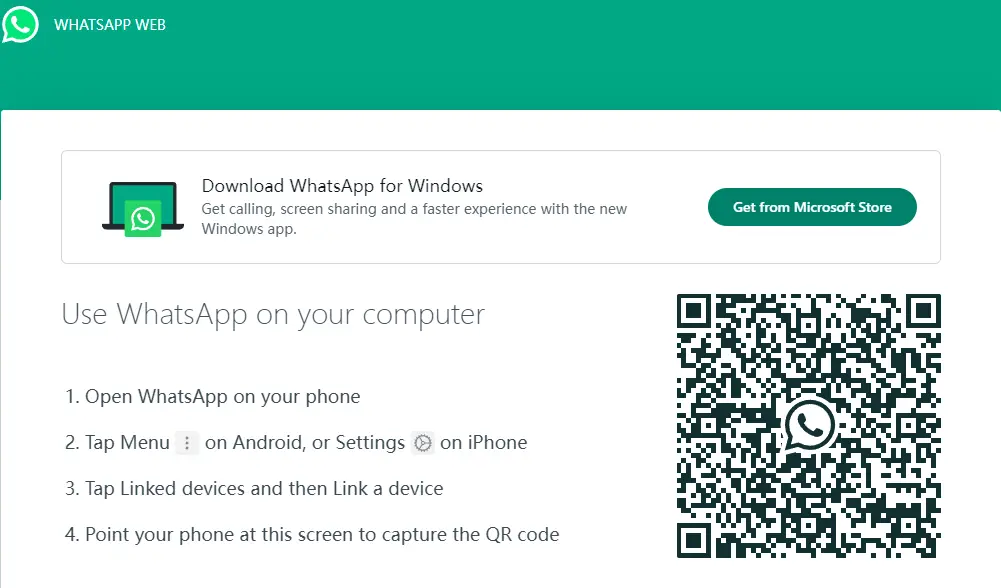
Steps to use this method (Steps for multi-device login)
Step 1. Go to the WhatsApp Web website on your computer or another device.
Step 2. Click on the option to log in. On the login screen, you will see an option to use WhatsApp Web on multiple devices.
Step 3. Click on this option to proceed. Enter the target's phone number into the provided field.
Step 4. Await for the one-time code that will be sent to the target's phone via SMS.
Step 5. Once the code is received, enter it into the designated field on the WhatsApp Web login screen.
Step 6. After entering the code, WhatsApp Web will establish a connection to the target's account without needing to scan a QR code.
Note: Messages are synchronized. It is recommended not to click on unread messages when logging into their account. This will help you avoid being discovered.
Method 3. Using WhatsApp hacking tool-SpyX is recommended
What is WhatsApp hacking tool
WhatsApp hacking tool can monitor various aspects of WhatsApp activity, including messages, calls, multimedia files, and even photos & videos.
SpyX is a specialized WhatsApp hacking tool designed to overcome the limitations of traditional hacking methods.
It offers a comprehensive solution for remotely monitoring WhatsApp activity, making it ideal for individuals who require discreet and efficient monitoring capabilities.
Its advanced features provide you with real-time insights into the target's WhatsApp usage, allowing for effective monitoring and surveillance.
Using SpyX, you can:
Steps to hack someone’s WhatsApp using SpyX remotely
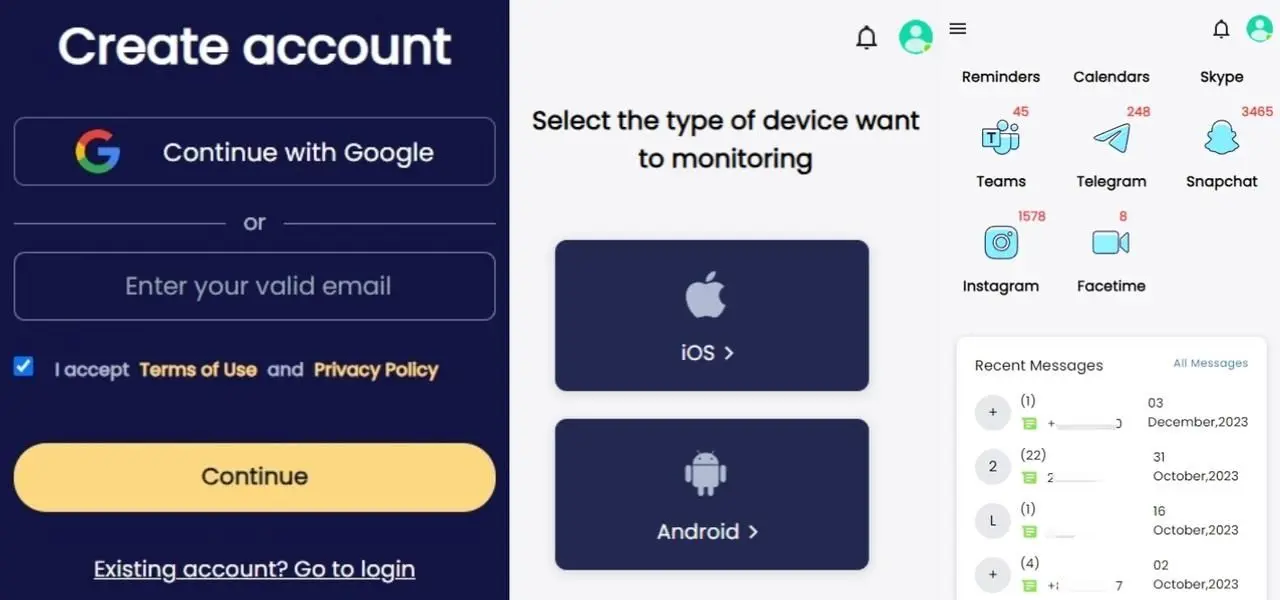
Step 1. Sign Up: Create an account on SpyX with a valid email.
Step 2. Select the Device: Decide which type of phone you'll be keeping an eye on, Android or iOS, based on what the target person uses.
Step 3. Bind the Target Phone: Next, choose a plan that works for you and follow the easy steps to link up with your child’s phone.
Step 4. Dive into WhatsApp Details: Once everything’s set, click on the WhatsApp function to start seeing the specific information.
In addition to WhatsApp monitoring, SpyX offers a range of other features.
Part 3. 5 common ways hackers hack WhatsApp
The previous part introduced some reasonable and legal methods to hack WhatsApp. So, in this part, I will introduce some common methods used by hackers to hack WhatsApp. Of course, this is illegal, so I do not recommend you to do this.
Method 1. Scan fake QR code on WhatsApp Web
Hackers often exploit the trust you place in QR codes to gain unauthorized access to WhatsApp accounts. By creating fake QR codes that resemble legitimate ones used for WhatsApp Web, hackers trick you into scanning them.
Once scanned, the hacker gains full access to your WhatsApp account, allowing them to read messages, view multimedia, and even send messages on behalf of the victim.
This method capitalizes on people's lack of awareness regarding QR code security and the ease with which QR codes can be replicated.
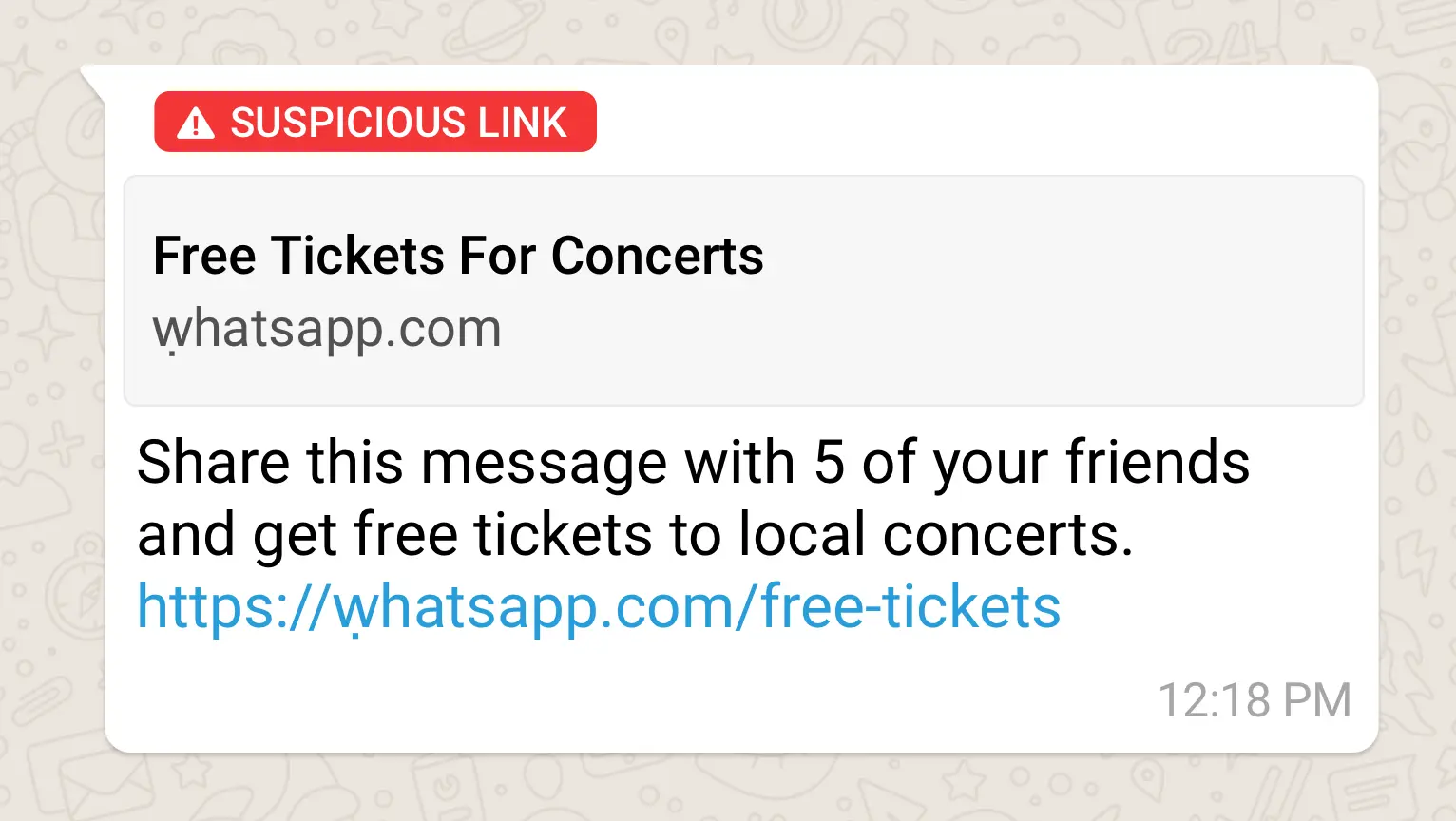
Method 2. Social Engineering attacks
Social engineering attacks involve manipulating individuals into divulging sensitive information or performing actions that compromise their security.
Hackers may impersonate trusted contacts, such as friends or colleagues, to trick you into sharing their WhatsApp verification code or clicking on malicious links.
Once you unwittingly provides access to their WhatsApp account, the hacker can exploit it for malicious purposes, such as spreading malware or stealing personal information.
Method 3. Media file jacking
Media file jacking exploits vulnerabilities in WhatsApp's end-to-end encryption to manipulate multimedia files sent and received through the platform.
By intercepting and modifying media files, such as photos, videos, and audio recordings, hackers can embed malicious code or malware payloads.
When the recipient views or downloads the manipulated media file, the malware is executed, granting the hacker access to the victim's device and potentially compromising their WhatsApp account.
Method 4. The pegasus voice attack
The Pegasus voice attack is a sophisticated cyberespionage technique developed by the NSO Group, a private Israeli surveillance company.
This attack targets WhatsApp by exploiting vulnerabilities in the app's voice-calling feature. Once compromised, the attacker gains complete control over the victim's device, including WhatsApp account.
The Pegasus voice attack is notoriously difficult to detect and defend against, making it a favored tool among state-sponsored hackers and surveillance agencies.
Method 5. Code execution via GIF
Code execution via GIF is a novel hacking technique that exploits vulnerabilities in WhatsApp's image-processing functionality.
By sending a specially crafted GIF file containing malicious code, hackers can trigger a buffer overflow or remote code execution vulnerability in WhatsApp's underlying software.
Once executed, the malicious code grants the hacker unauthorized access to the victim's device and WhatsApp account, enabling them to steal sensitive information or conduct further attacks.
Legality:
Each of these hacking methods raises significant legal concerns and may violate various laws governing cybersecurity, privacy, and data protection.
Unauthorized access to computer systems, manipulation of digital content, and exploitation of software vulnerabilities are all potential legal offenses that can result in severe penalties.
It's essential for individuals to understand the legal implications of engaging in hacking activities and to prioritize ethical behavior and respect for privacy and security.
Part 4. How to choose the most suitable method to hack WhatsApp
Legality Aspect
From a legal perspective, accessing the WhatsApp account password through direct means, such as obtaining the target's phone, is the most suitable method.
This approach is less likely to violate privacy laws compared to more intrusive methods like hacking via SMS or using unauthorized tools.
While it still involves accessing someone's device, it typically falls within the bounds of lawful monitoring, especially in cases involving minors or shared devices within a family setting.
Ease of Operation Aspect
In terms of ease of operation, choose the easiest way to operate.
SpyX offers a user-friendly interface and streamlined setup process, making it accessible even for individuals with limited technical expertise.
With SpyX, you can remotely monitor WhatsApp activity without the need for complex procedures or physical access to the target device, ensuring convenience and efficiency.
Functionality Aspect
When considering functionality, choose the tool that has the most comprehensive functions.
Other methods that may have limitations in terms of the data they can access or the level of monitoring they offer, but SpyX provides comprehensive monitoring capabilities.
Users can not only access WhatsApp messages but also track multimedia files, call logs, and even GPS locations, offering a holistic view of the target's activities.
Cost Aspect
While some hacking methods may come with minimal or no financial costs, they often require significant time and effort or may carry hidden risks.
In contrast, investing in a reputable WhatsApp hacking tool can offer greater value in the long run. While some apps may require a subscription or a one-time purchase fee.
In addition to the above aspects, you can also consider the aspects of privacy, user experience, etc., In short, the best method is the one that works for you.
Part 5. FAQs
Can someone hack my WhatsApp and see my messages?
Yes, in this age of technology, there are many ways to hack your WhatsApp. Hackers often use methods such as sending phishing links and implanting virus software to hack your WhatsApp. Once they hack into your WhatsApp, they can log into your WhatsApp and see your messages.
What are the signs that my WhatsApp is hacked?
There are several signs that your WhatsApp may have been hacked. Here are common signs:
- Random and unusual activity: Personal information has been changed, contacts have disappeared, inexplicable messages have been received, etc.
- Unusual login activity or receiving notifications about logins from an unrecognized device or location.
- unable to access your account.
How can I improve my WhatsApp security?
To improve WhatsApp security, you can follow these points:
- Use two-factor authentication
- Use a strong password
- Review your account security
- Use WhatsApp’s Lock feature
- Keep your WhatsApp updated
Can you recover a hacked WhatsApp?
If your WhatsApp account has been hacked, you should take immediate steps to recover it.
- First try logging into your WhatsApp account. Once you're logged in, immediately change your password and enable 2-step verification to add security to your account.
- If you are unable to access your account, use the "Forgot Password" option to reset your password.
- If none of the above methods work, you can contact WhatsApp support for help.
Can same WhatsApp account on two devices?
Yes, since April 2023, WhatsApp has released an update to support logging in on multiple devices with the same WhatsApp account. One account can be logged in on up to 4 devices.
Part 6. Conclusion
Hacking WhatsApp remotely is a complex endeavor that requires careful consideration of ethical and legal implications.
While there may be legitimate reasons for accessing WhatsApp accounts, such actions should be approached with caution and respect for privacy.
For those in need of monitoring solutions, SpyX offers a reliable and discreet option. Ultimately, prioritizing legality and ethical conduct is paramount in navigating the realm of WhatsApp hacking.
More Articles Like This







Disclaimer
SPYX'S SOFTWARE INTENDED FOR LEGAL USE ONLY. You are required to notify users of the device that they are being monitored. Failure to do so is likely to result in violation of applicable law and may result in severe monetary and criminal penalties ...
Company Name: UK GBYTE TECHNOLOGY CO., LIMITED
Registered Number: 15400579
Registered Address: South Bank Tower, 55 Upper Ground,, London, England, SE1 9EY
Company Name:Gbyte Technology Co., Limited
Registered Address: FLAT 2304, 23/F HO KING,COMMERCIAL CENTRE, 2-16 FAYUEN STREET, MONG KOK KOWLOON HONG KONG
Copyright © 2024 SPYX. All Rights Reserved.







Disclaimer: SPYX'S SOFTWARE INTENDED FOR LEGAL USE ONLY. You are required to notify users of the device that they are being monitored. Failure to do so is likely to result .....
Registered Address: South Bank Tower, 55 Upper Ground,, London, England, SE1 9EY
Company Name: UK GBYTE TECHNOLOGY CO., LIMITED
Wisteria Trade Limited
Copyright © 2024 SPYX. All Rights Reserved.